Multi-data-source access method, device and system, and readable storage medium
A multi-data source and data system technology, applied in the field of data processing, can solve the problems of high difficulty, large data source access, difficulty, etc., and achieve strong data access capabilities, flexible data access methods, and improved flexibility in calculation and access Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
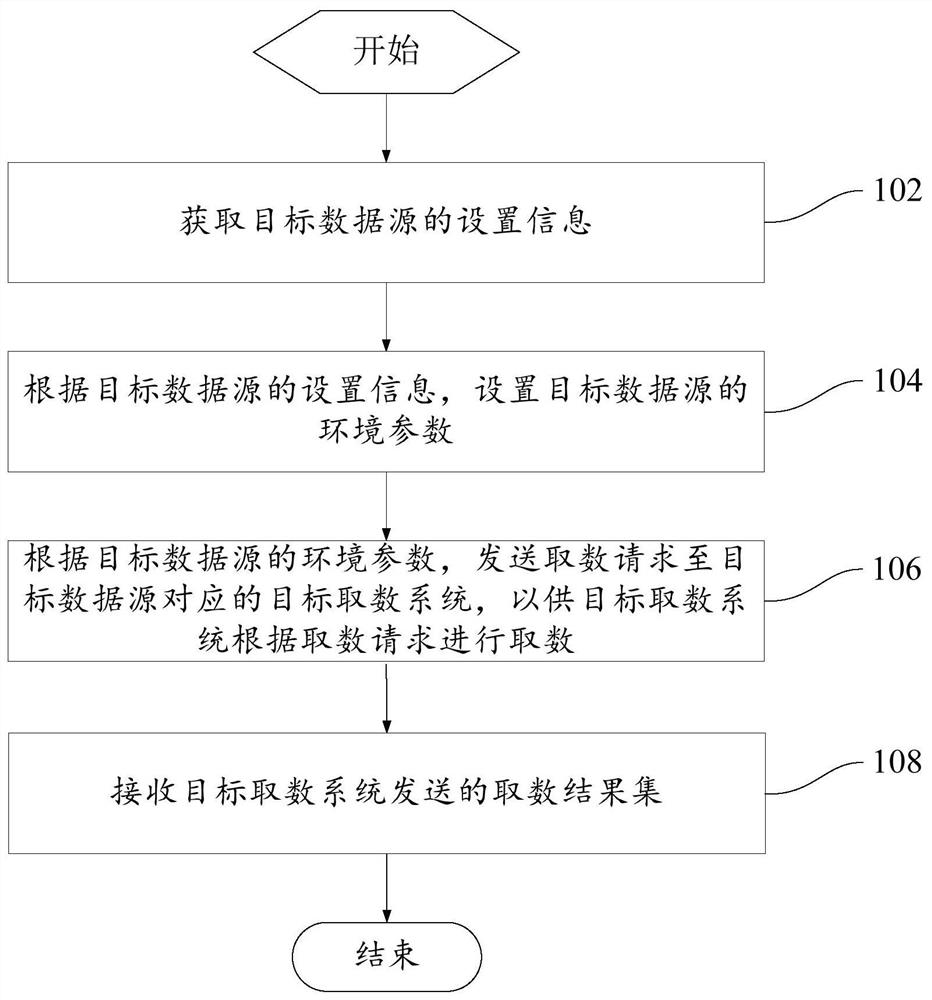
[0049] Such as figure 1 As shown, Embodiment 1 provides a method for fetching numbers from multiple data sources, including:
[0050] Step 102, obtaining the setting information of the target data source;
[0051] Step 104, setting the environment parameters of the target data source according to the setting information of the target data source;
[0052] Step 106, according to the environmental parameters of the target data source, send a data fetching request to the target data fetching system corresponding to the target data source, so that the target data fetching system can fetch data according to the data fetching request;
[0053] Step 108, receiving the number fetching result set sent by the target number fetching system.
[0054] The multi-data source access method provided by the embodiment of the present invention obtains the setting information of the user-defined data source to be accessed by obtaining the setting information of the target data source, thereby p...
Embodiment 2
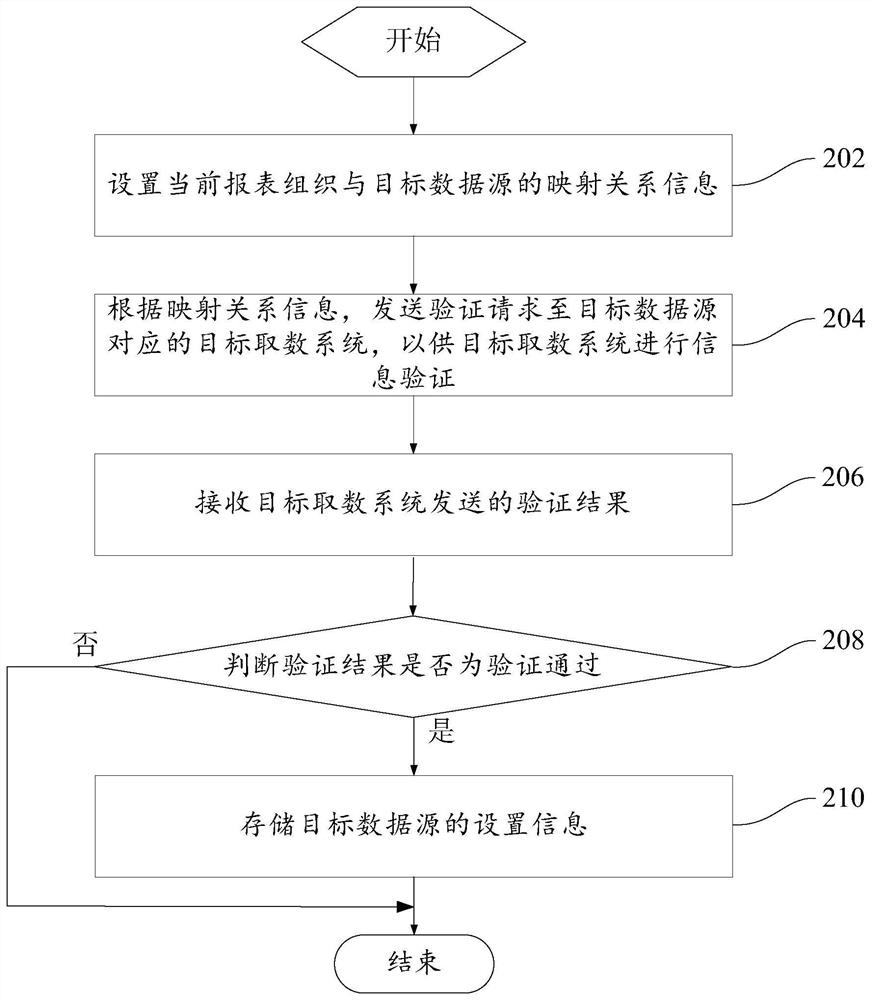
[0060] Such as figure 2 As shown, on the basis of Embodiment 1, Embodiment 2 provides a multi-data source access method, which further defines that before the step of obtaining the report organization information of the current system, the multi-data source access method also includes:
[0061] Step 202, setting the mapping relationship information between the current report organization and the target data source;
[0062] Step 204, according to the mapping relationship information, send a verification request to the target data access system corresponding to the target data source, so that the target data access system can perform information verification;
[0063] Step 206, receiving the verification result sent by the target data retrieval system;
[0064] Step 208, judging whether the verification result is verified, if the judgment result is yes, execute step 210, and when the judgment result is no, end;
[0065] Step 210, storing the setting information of the target...
Embodiment 3
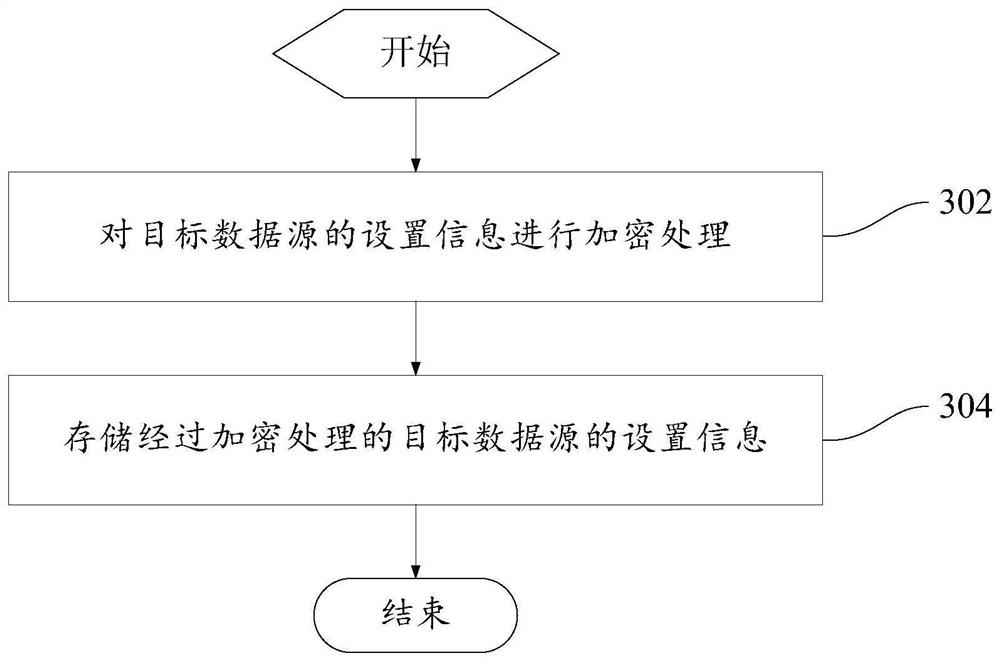
[0070] Such as image 3 As shown, on the basis of any of the above embodiments, the third embodiment defines the steps of storing the setting information of the target data source, which specifically includes:
[0071] Step 302, encrypting the setting information of the target data source;
[0072] Step 304, storing the encrypted setting information of the target data source.
[0073] In this embodiment, when storing the setting information of the target data source, the setting information of the target data source is encrypted first, and then stored, so as to ensure data security during data transmission and network transmission during data retrieval. security.
[0074] In one embodiment, when storing the setting information of the target data source, the current report organization information is also stored, and the current report organization information and the setting information of the target data source are only symmetrically encrypted to further improve the securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com