Method for actively discovering distributed self-built system and scanning security vulnerabilities
An active discovery and distributed technology, applied in the field of information security, can solve problems such as difficult data access, many information security loopholes, hidden dangers, etc., and achieve the effect of real-time reliable data support
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
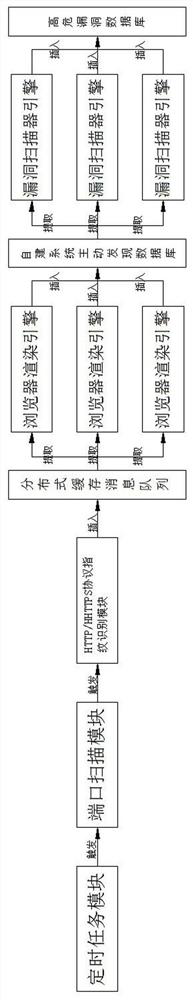
[0028] The technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings.
[0029] The method for proactively discovering distributed self-built systems and scanning for security holes is characterized in that it includes the following steps:
[0030] Step 1, the user defines the time period in the timing task module, and the timing task module triggers the port scanning module to perform scanning tasks according to the time period defined by the user;
[0031] Step 2, the port scanning module resolves the target address segment predefined by the user, and resolves the target address segment into target addresses one by one, and sends a SYN packet requesting connection to a port of the target host of each target address; the scanning of the port scanning module The device scans the data packet returned by the target host, and determines whether the port of the target host is open according to the packet type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com