Confidential statistical data sharing method and system based on set operation
A technology of statistical data and set operation, applied in the field of information security, it can solve problems such as leakage of intersection elements and achieve the effect of traffic optimization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
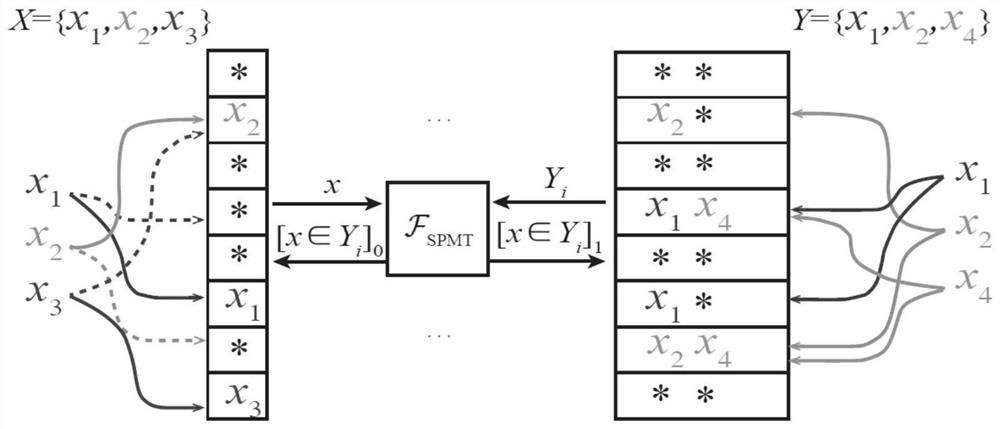
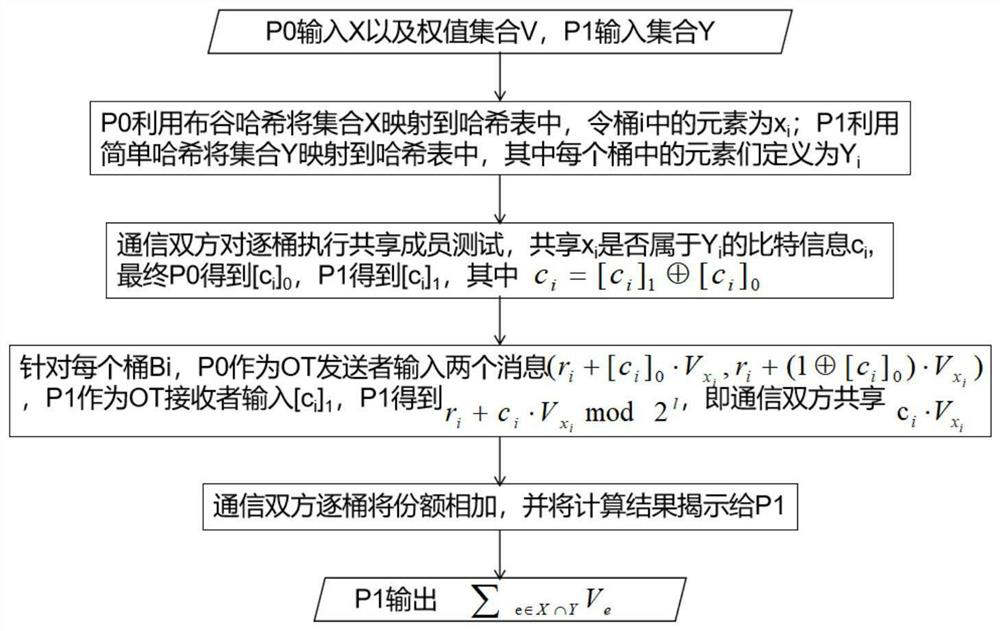
[0070] Such as image 3 As shown, the present embodiment provides a confidential statistical data sharing method based on set operations, which includes:
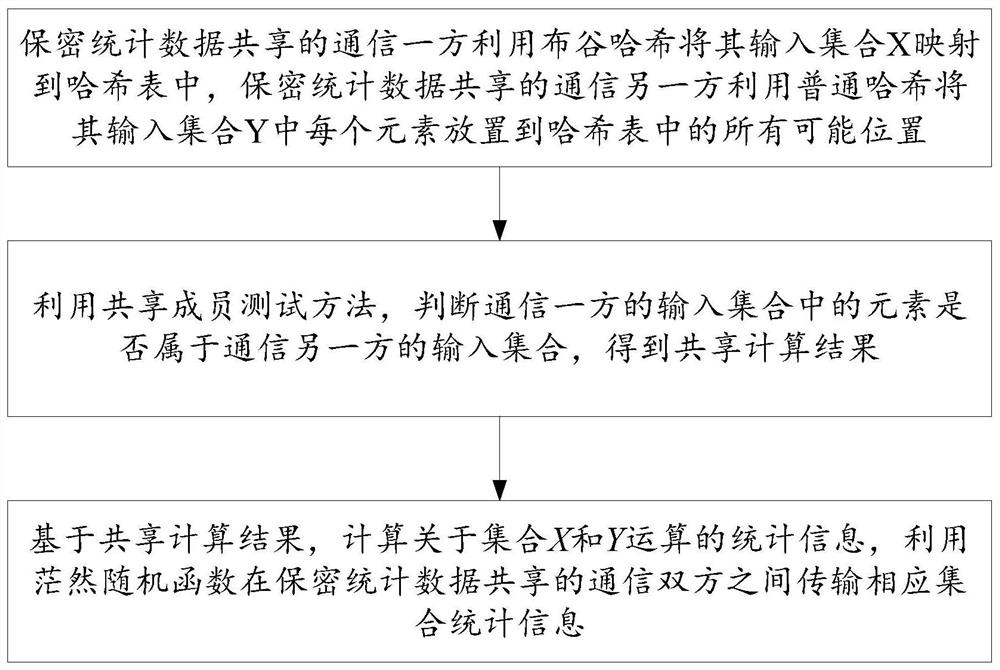
[0071] Step 1: One party communicating with confidential statistical data uses cuckoo hash to map its input set X to a hash table, and the other party communicating with confidential statistical data uses common hash to place each element in its input set Y into hash table all possible positions in the Greek table;
[0072] Step 2: Use the shared membership test method to judge whether the elements in the input set of one party of communication belong to the input set of the other party of communication, and obtain the shared calculation result;
[0073] Step 3: Based on the shared calculation results, calculate the statistical information about the set X and Y operations, and use the dazed random function to transmit the corresponding set statistical information between the communication parties sharing the confidential s...
Embodiment 2
[0106] This embodiment provides a confidential statistical data sharing system based on set operations, which includes:
[0107] The communication party sharing confidential statistical data uses cuckoo hash to map its input set X into a hash table;
[0108] The other party to the communication of confidential statistical data sharing, which uses ordinary hashing to place each element of its input set Y into all possible positions in the hash table;
[0109] The communicating parties for confidential statistics sharing are configured as:
[0110] Use the shared membership test method to judge whether the elements in the input set belong to the input set of the other party in communication, obtain the shared calculation result, and then calculate the statistical information about the operation of the set X and Y;
[0111] Transferring ensemble statistics using dazed random functions.
[0112] Among them, the protocol communication complexity of set X and set Y is equal.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com