Peep-proof cipherer and password recognition method
An identification method and technology of a cipher, which are applied in the field of anti-peep cipher and password identification, can solve the problems of poor anti-theft performance of the cipher, and achieve good anti-peep effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
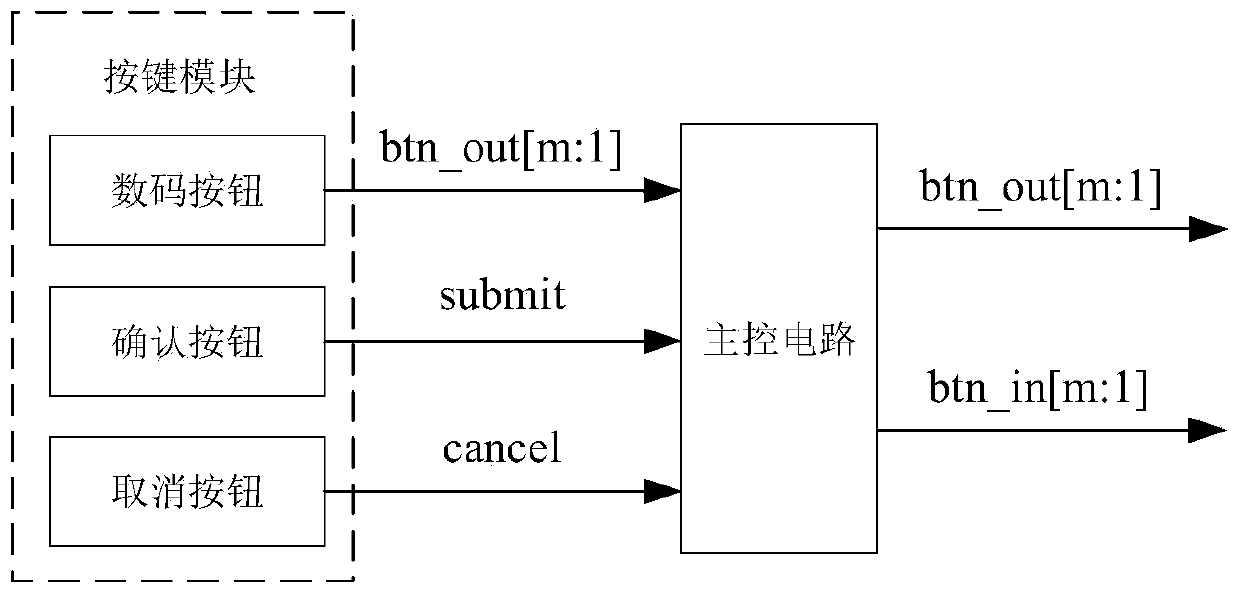
[0026] The embodiment of the present application provides an anti-peeping cipher, such as figure 1 As shown, the anti-peeping cipher includes a key module and a main control circuit.
[0027] The key module includes a number button, a confirm button and a cancel button. The digital button outputs pressing signals btn_out[m:1] of m digital buttons to the main control circuit, and each pressing signal in btn_out[m:1] corresponds to one bit of the digital buttons. For example, the pressing signal output by the i-th digital key is btn_out[i]. When the user presses the ith (1<=i<=m) button effectively, btn_out[i] is 1, the btn_out[i] signal is valid, and the btn_out[i] signal is output to the main control circuit. Otherwise, when the user presses the ith (1<=i<=m) key invalidly, btn_out[i] is 0, and no signal is output.
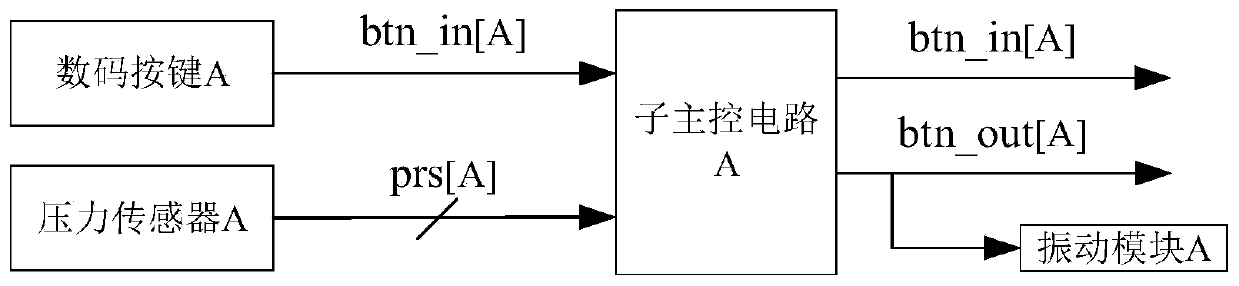
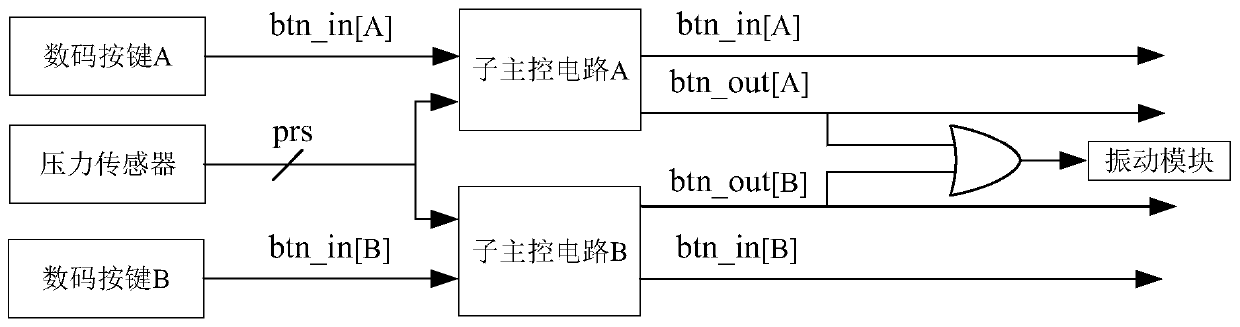
[0028] In this application, each digital key of the digital button has a sub-main control circuit, and a pressure sensor is arranged below the digital key. The...
Embodiment 2
[0045] The present application also provides a password identification method corresponding to the above-mentioned anti-peeping password device.
[0046] like Figure 4 As shown, the password identification method of the sub-main control circuit includes the following steps:
[0047] S410: The sub-main control circuit receives the pressing signal btn_in output by the digital key, that is, btn_in is 1.
[0048] S420: The sub-main control circuit collects the pressure signal prs signal output by the pressure sensor.
[0049] S430: The sub-main control circuit judges whether the pressure exceeds the threshold T, that is, the pressure≥threshold T. If yes, execute S440. Otherwise, execute S450.
[0050] S440: The sub-main control circuit outputs a valid pressing signal to the main control circuit and the vibration module, that is, btn_out is 1. The main control circuit saves the code value after receiving an effective pressing signal, and the vibration module triggers vibratio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com