Two-factor authentication apparatus and method, and computer readable storage medium
An authentication method and authentication device technology, applied in the field of login verification, can solve the problem of high verification cost of two-factor authentication, and achieve the effect of low verification cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
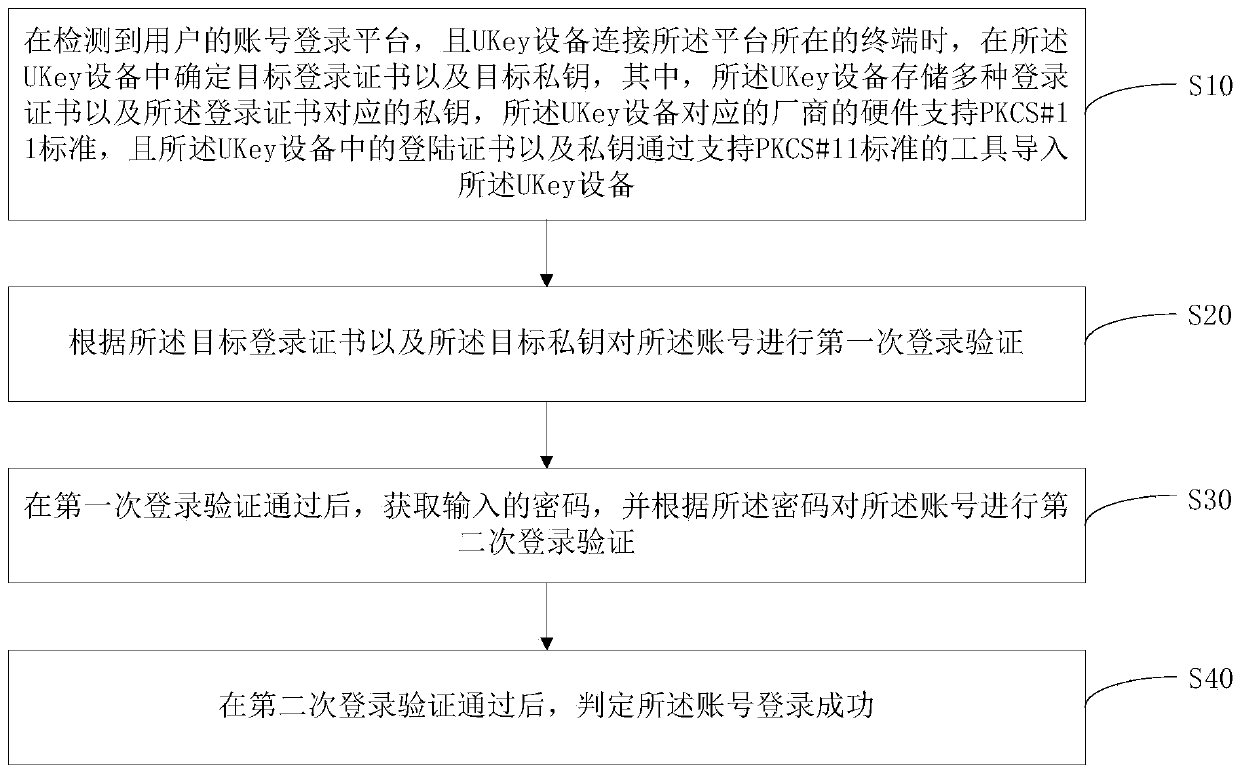
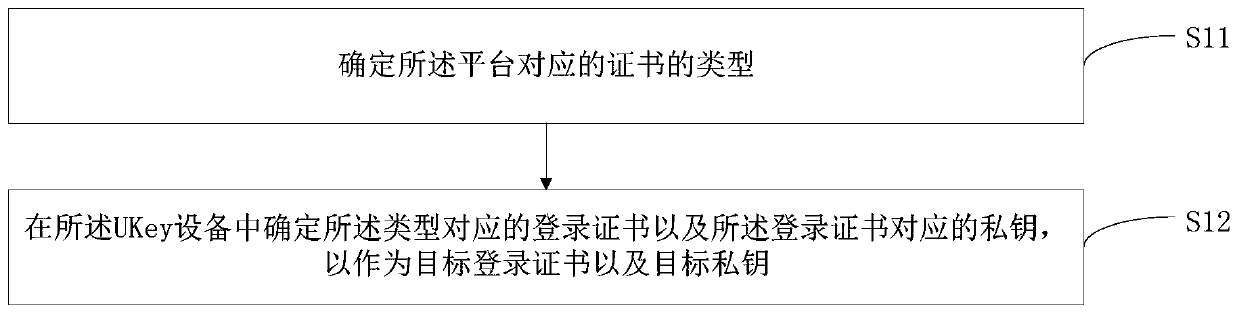
[0080] refer to figure 2 , figure 2 As the first embodiment of the two-factor authentication method of the present invention, the two-factor authentication method includes the following steps:
[0081] Step S10, when it is detected that the user's account is logged into the platform, and the UKey device is connected to the terminal where the platform is located, the target login certificate and the target private key are determined in the UKey device, wherein the UKey device stores multiple login certificates And the private key corresponding to the login certificate, the hardware of the manufacturer corresponding to the UKey device supports the PKCS#11 standard, and the login certificate and the private key in the UKey device are imported into the UKey device through a tool that supports the PKCS#11 standard ;
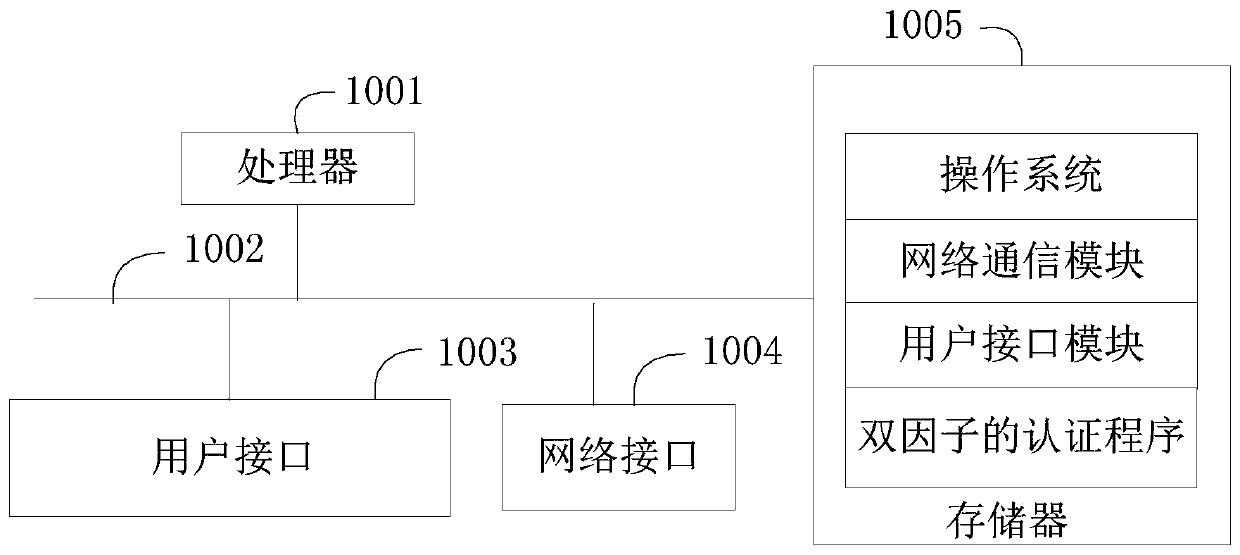
[0082] In this embodiment, the execution subject is a two-factor authentication device. For ease of expression, an authentication device is used below to refer t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com