A method to determine the attack path of lateral movement in honeynet based on the analysis of attack behavior
An attack path and behavior analysis technology, applied to electrical components, transmission systems, etc., can solve problems such as the inability to identify multiple attackers’ attack paths, rigid methods for determining attack behavior, and inaccessible paths.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
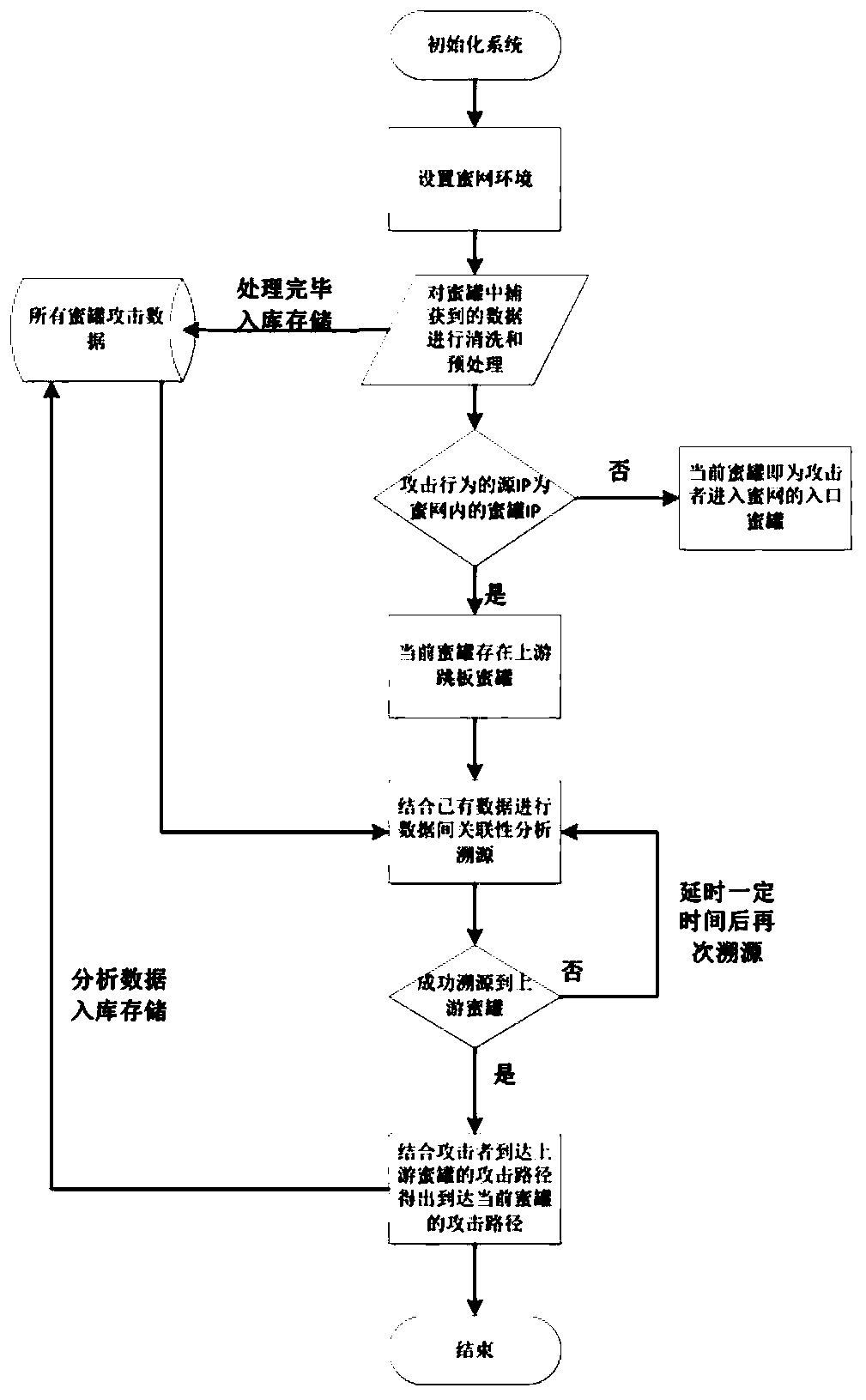
[0057] The method for determining the lateral movement attack path in the honeynet based on attack behavior analysis provided by the present invention comprises the following steps:
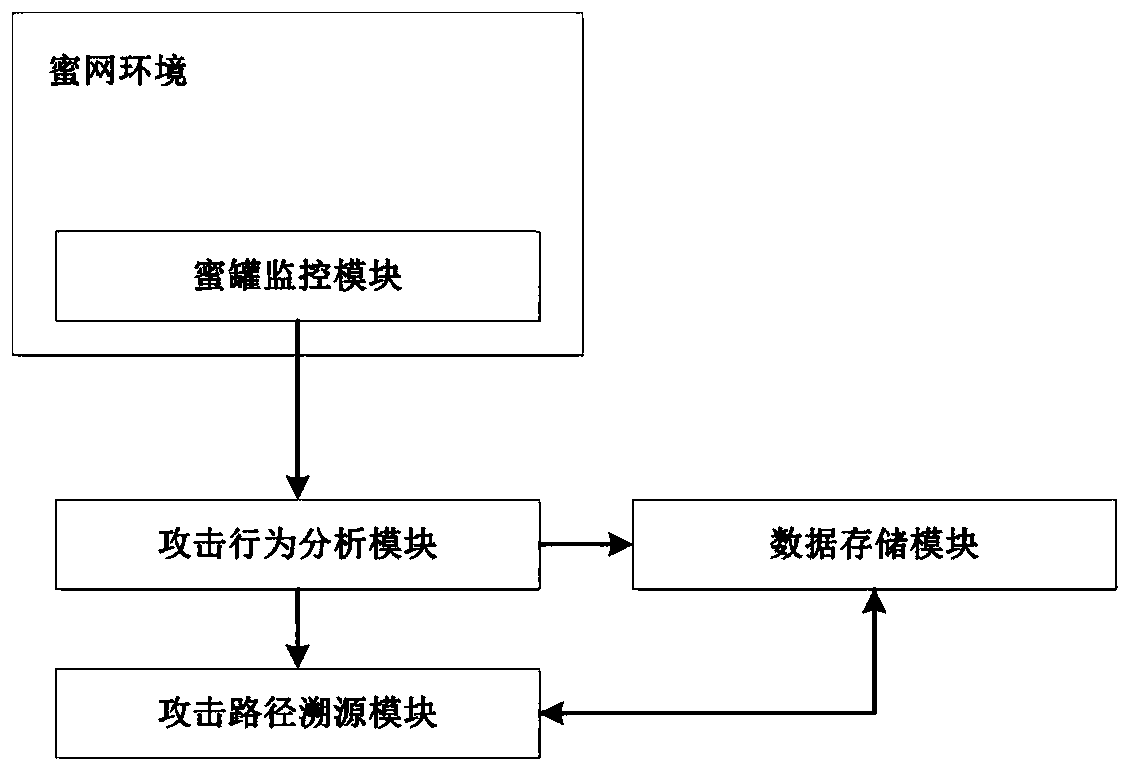
[0058] S1: Deploy multiple honeypots to form a honeynet environment. The honeynet environment includes honeypot A, honeypot B, honeypot C...;
[0059] Among them, the honeypot is equipped with a honeypot monitoring module. The honeypot monitoring module is a set of monitoring programs that run secretly in the honeypot. The processes, files, network data and network connections related to the monitoring program have deep hidden characteristics. and tools cannot detect;
[0060] The monitoring program monitors the core layer, the network layer and the application layer in the honeypot host in real time, and the honeypot monitoring module is used to accurately identify active attackers in the current honeypot, and links the attack behavior data with the attack source;
[0061] The honeypot monitori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com