Blacklist management method and device, computer system and readable storage medium
A management method and blacklist technology, applied in the field of communication, can solve the problem that the authenticity of information in the blacklist cannot be guaranteed, and achieve the effect of ensuring closure, privacy and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
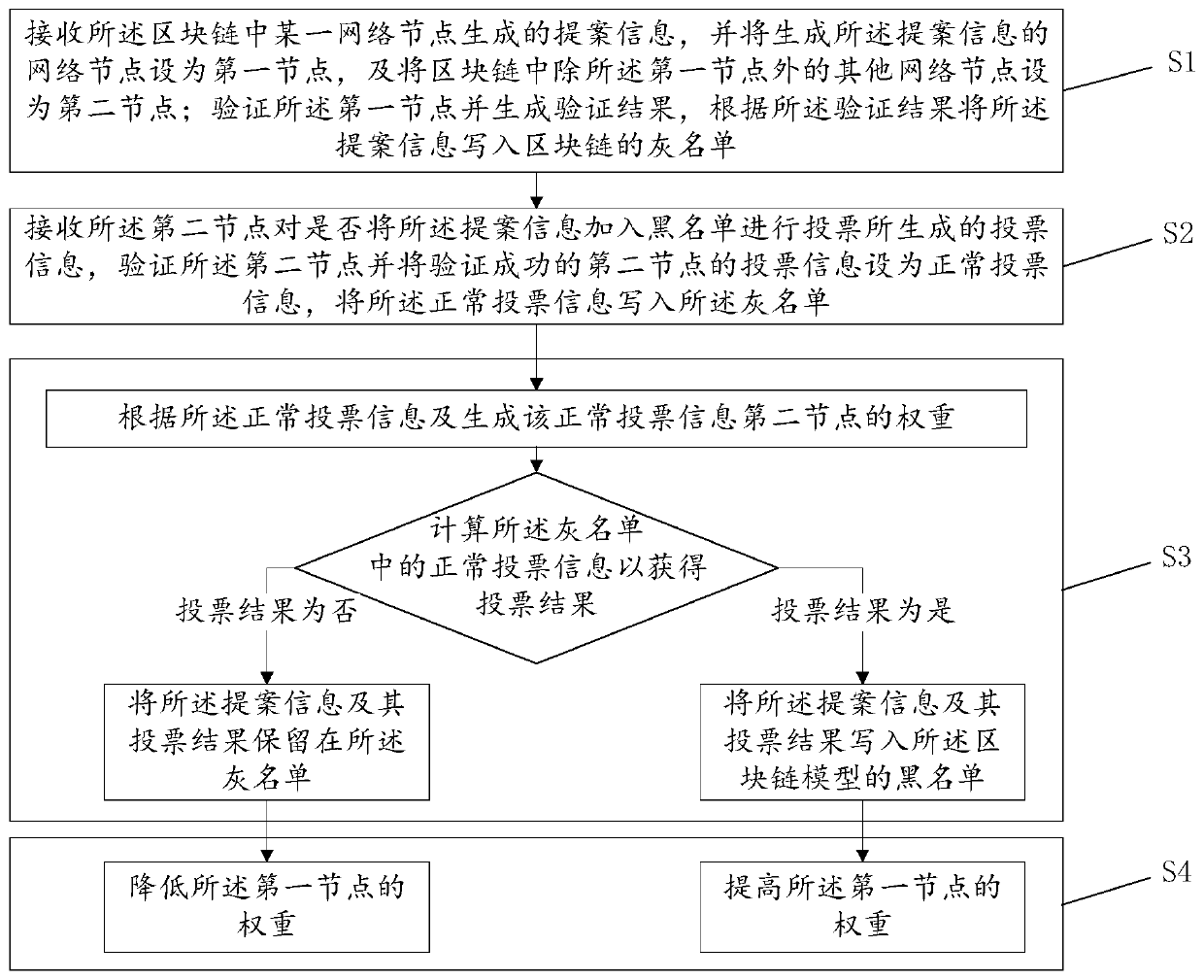
[0059] See figure 1 , The blacklist management method of this embodiment is based on a blockchain, the blockchain having at least one network node, and includes the following steps:
[0060] S1: Receive proposal information generated by a certain network node in the blockchain, and set the network node that generated the proposal information as the first node, and set other networks in the blockchain except the first node The node is set as the second node; the first node is verified and the verification result is generated, and the proposal information is written into the gray list of the blockchain according to the verification result; wherein, the gray list is used to store proposal information In the historical database, the proposal information is information of suspects suspected of dishonesty entered into the network node by the user through the user terminal;
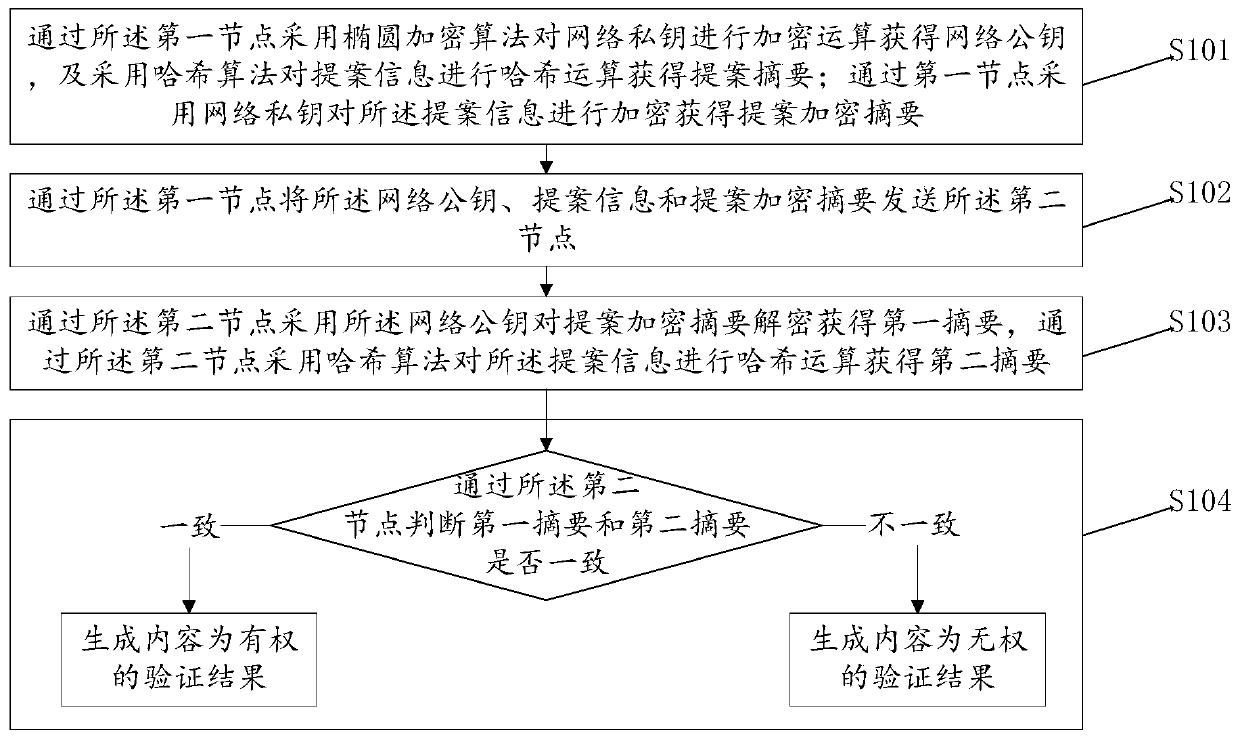
[0061] S2: Receive the voting information generated by the second node to vote whether to add the proposal informa...
Embodiment 2
[0129] See Picture 9 , A blacklist management device 1 of this embodiment includes:
[0130] The proposal verification module 11 is configured to receive proposal information generated by a certain network node in the blockchain, and set the network node generating the proposal information as the first node, and divide the first node from the blockchain The other network nodes outside the node are set as the second node; the first node is verified and the verification result is generated, and the proposal information is written into the gray list of the blockchain according to the verification result; wherein, the gray list is used In a historical database storing proposal information, the proposal information is information of suspected untrustworthy suspects entered by the user through the user terminal to the network node;
[0131] The voting verification module 12 is configured to receive the voting information generated by the second node to vote whether to add the proposal i...
Embodiment 3
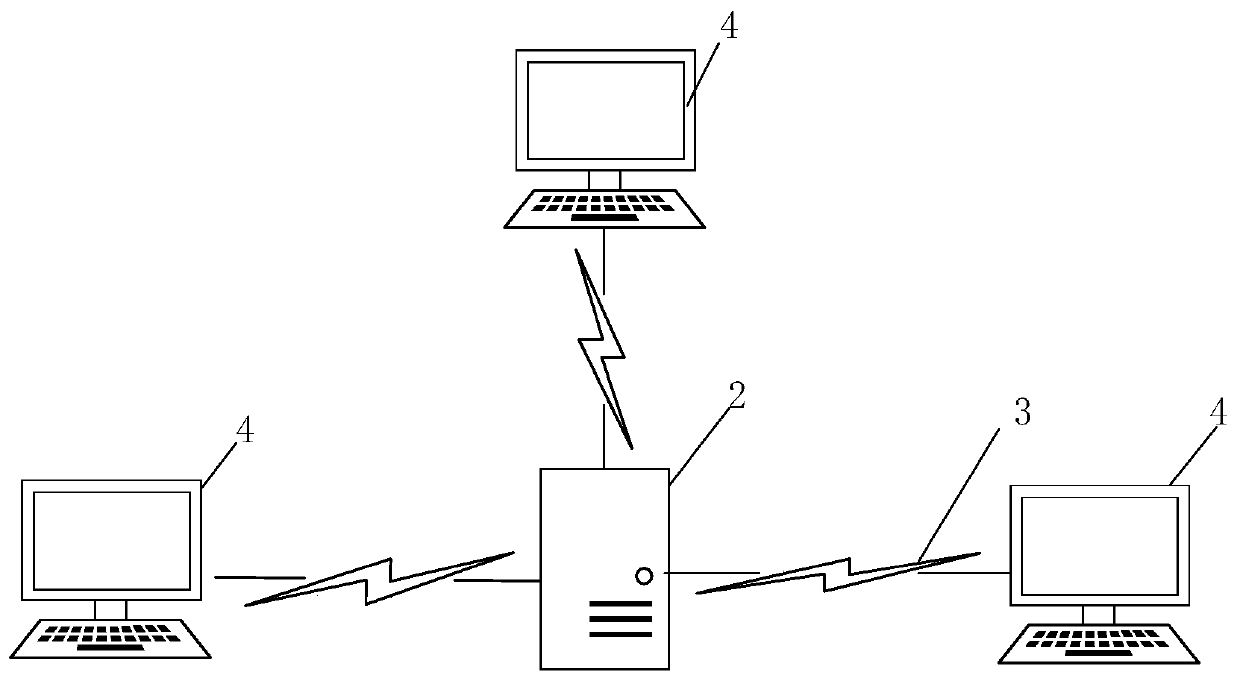
[0136] In order to achieve the above-mentioned object, the present invention also provides a computer system, which includes a plurality of computer devices 5. The components of the blacklist management apparatus 1 of the second embodiment can be dispersed in different computer devices, and the computer devices can be executed Program smart phones, tablet computers, notebook computers, desktop computers, rack servers, blade servers, tower servers or cabinet servers (including independent servers, or server clusters composed of multiple servers), etc. The computer device in this embodiment at least includes but is not limited to: a memory 51 and a processor 52 that can be communicatively connected to each other through a system bus, such as Picture 10 Shown. It should be pointed out that Picture 10 Only a computer device with components is shown, but it should be understood that it is not required to implement all the illustrated components, and more or fewer components may b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com