DOS attack and defense simulation method based on random Petri network
An attack-defense simulation and attack-side technology, applied to electrical components, transmission systems, etc., can solve the problems of not considering the function of system attack detection at the same time, the system repair function defense strategy, and the failure to show the details of the system defense process well.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
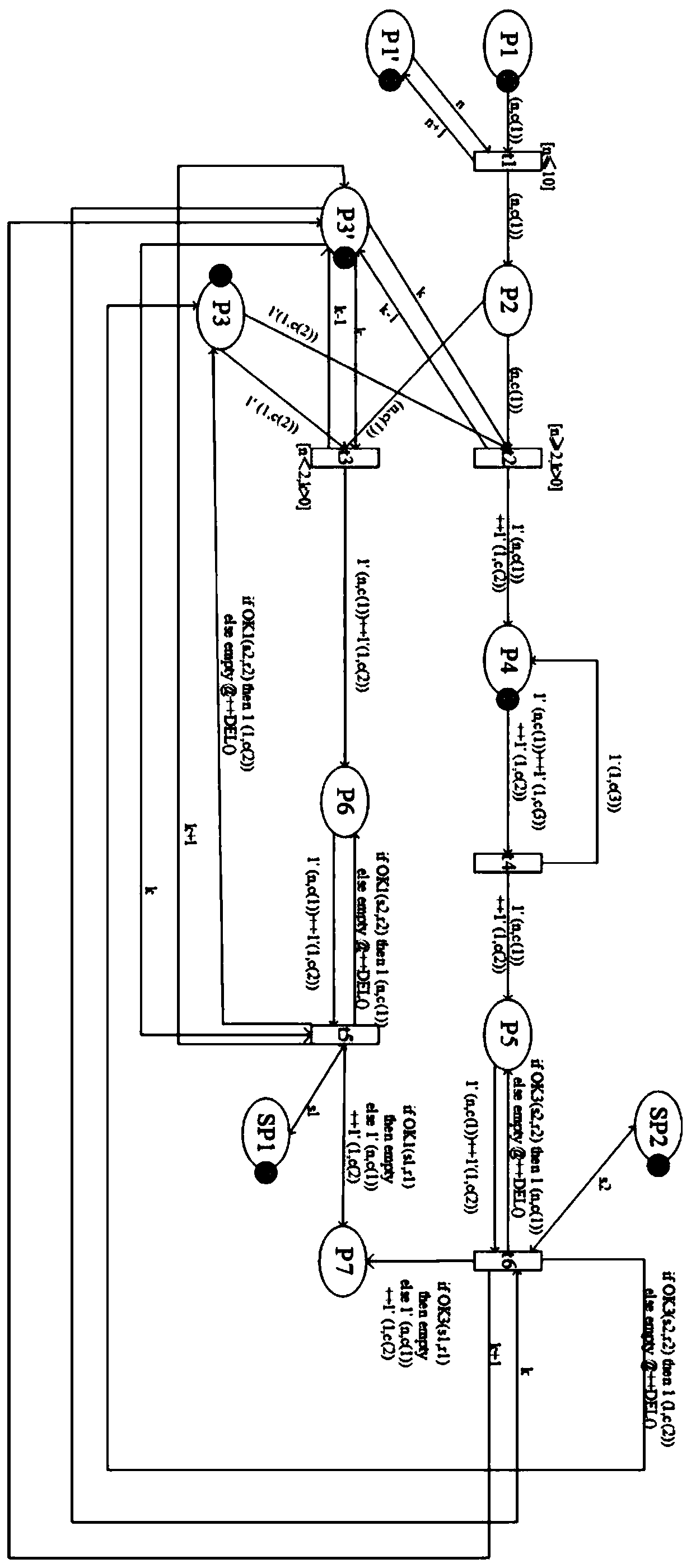
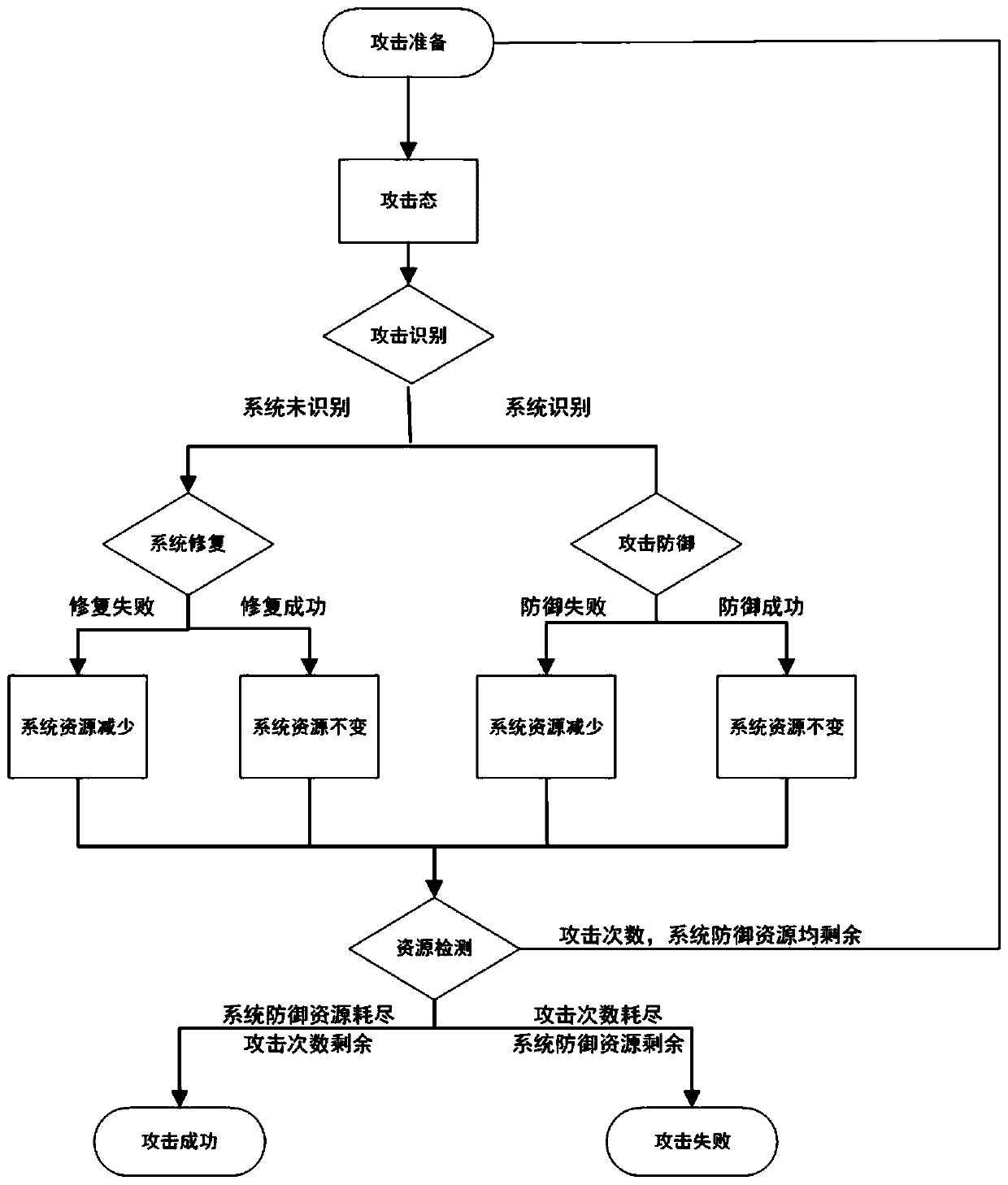
[0062] The DOS attack and defense simulation method based on random Petri nets includes the following process:
[0063] Step 1: Using colored Petri nets, construct a system defense model of colored Petri nets under DOS attacks;
[0064] The coloring Petri net seven-tuple is: {P, T, G, A, F, C, M 0},
[0065] Among them: P is the finite set of places p, indicating the state of the system; T is the finite set of transition t, indicating the action that causes the system state to change; G is the transition guard function, indicating the condition that triggers the system transition; A is the arc a Set is a directed arc connecting places and transitions; F is an arc function, indicating the change of Tokens in places when the system state changes; C is the color set of Tokens, indicating the types of Tokens in the system; M 0 is the initial identification, indicating the number of Token distributions in the warehouse in the initial state of the system;
[0066] In a system def...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com