Video and audio credible playing method based on asymmetric encryption
A technology of asymmetric encryption and playback method, applied in the field of digital security, can solve the problems of inability to determine illegal replacement of video streaming media, lack of verification considerations for video content, etc., to improve reliability, achieve security and real-time performance, and reduce computing effect of overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
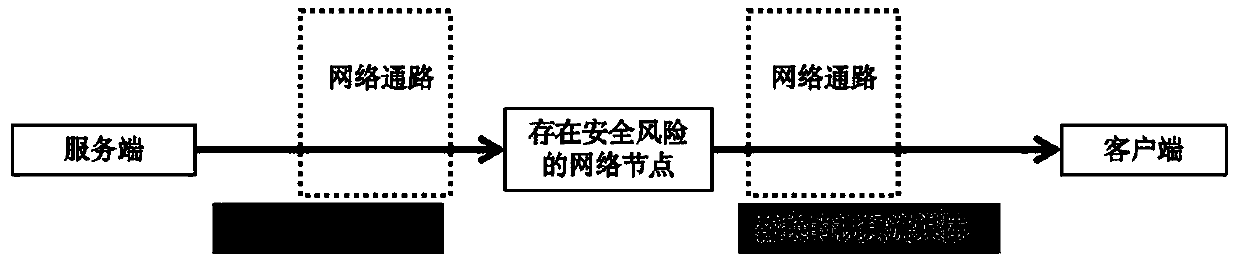
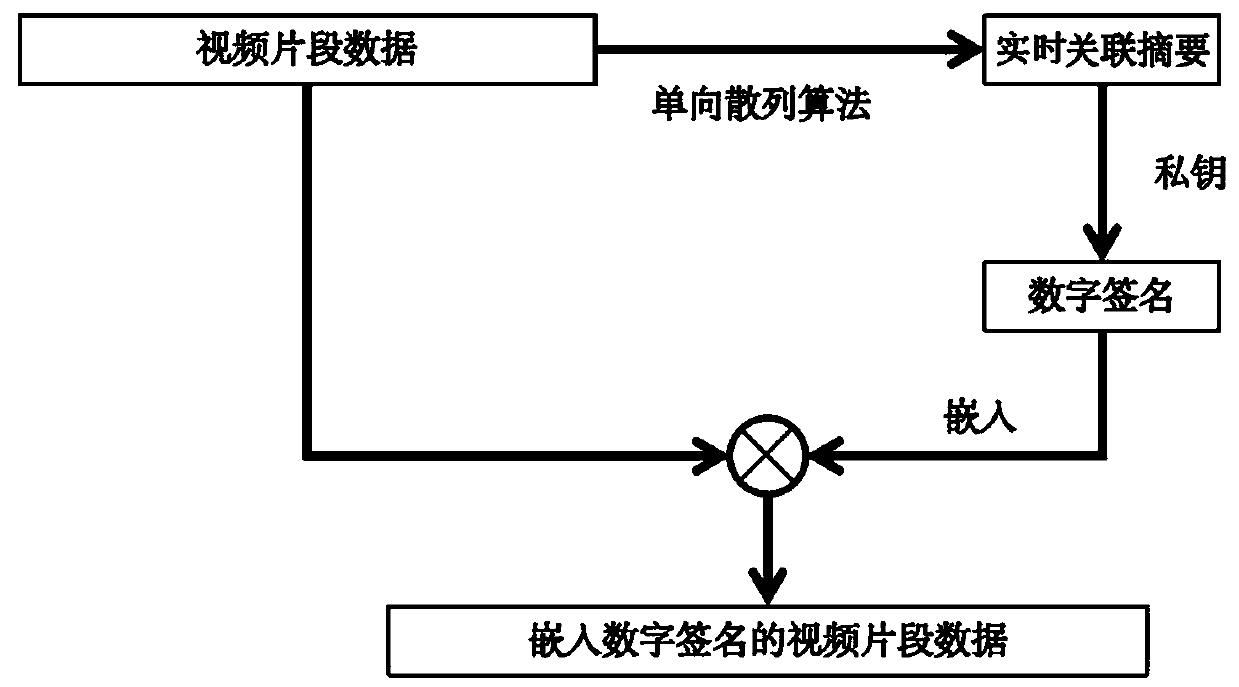
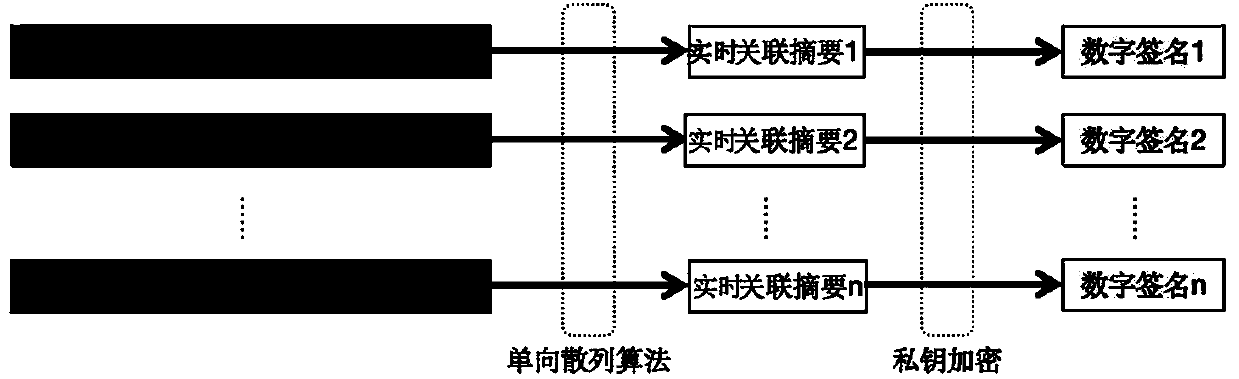
[0064] Such as figure 1 As shown, the present embodiment provides a trusted video and audio playback method based on asymmetric encryption, including the following steps:
[0065] S1: The publishing end embeds a digital signature encrypted with a private key into the video streaming media during the transcoding service process of the video streaming media, and then pushes the video streaming media embedded with the digital signature to the intermediate network;
[0066] Usually, the transcoding service of the video publishing end is to successively scale, encode and sign the decoded video streaming media, but in this embodiment, the digital signature encrypted by the private key is embedded into the video streaming media; the involved in S1 The intermediate network is the existing network circulation channel, which is used as the media of video streaming media;
[0067] S2: After receiving the video streaming media through the intermediate network, the client extracts the di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com