Authentication method, authentication device and intelligent terminal device
A technology of smart terminal equipment and authentication methods, applied in the field of smart terminals, can solve problems such as dirty fingers and inconvenient fingers, and achieve the effect of timely and effective unlocking and locking screen operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
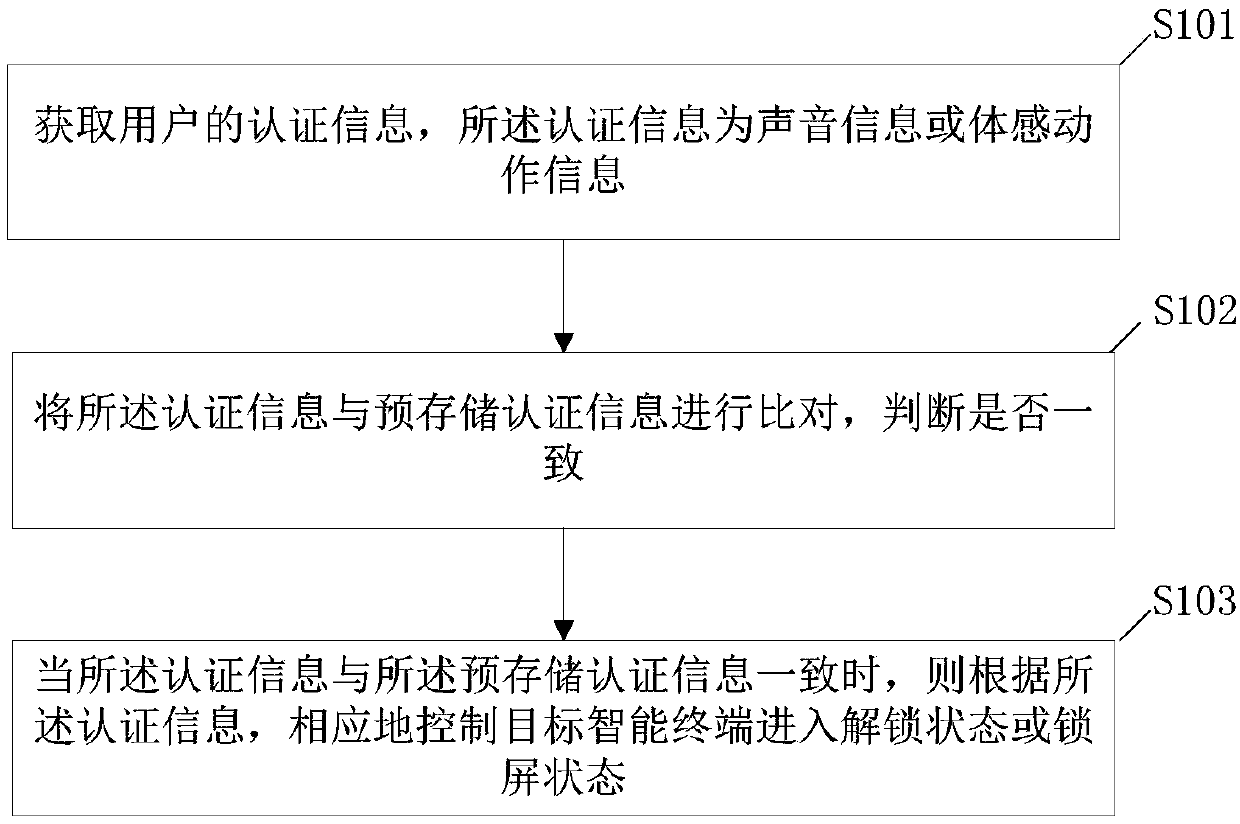
[0046] see figure 1 , which is a schematic flowchart of an authentication method for an intelligent terminal device provided in an embodiment of the present invention, the method may include the following steps:
[0047] Step 101. Obtain authentication information of the user, the authentication information being voice information or somatosensory action information;
[0048] In a specific application, the user's voice and somatosensory motion can be collected respectively through the voice collection device and the somatosensory motion collection device, and the corresponding sound information and somatosensory motion information can be extracted from the sound and somatosensory motion.
[0049] Step 102, comparing the authentication information with the pre-stored authentication information, and judging whether they are consistent;
[0050] It should be noted that there may be multiple pre-stored authentication information, that is, multiple voice information and multiple s...
Embodiment 2
[0058] When the authentication information is somatosensory action information, it is relatively easy to have a security hole. For example, the unlocking body motion set by the user of the target smart terminal is as a finger sliding up, and in some cases, the user who is not the target smart terminal happens to make the same gesture, and the target smart terminal receives the unlocking body motion, The unlock operation will be performed. In this way, the security of the target smart terminal will be lower.
[0059] In order to further improve the security of the target smart terminal, voice authentication can be performed on the basis of somatosensory motion authentication.
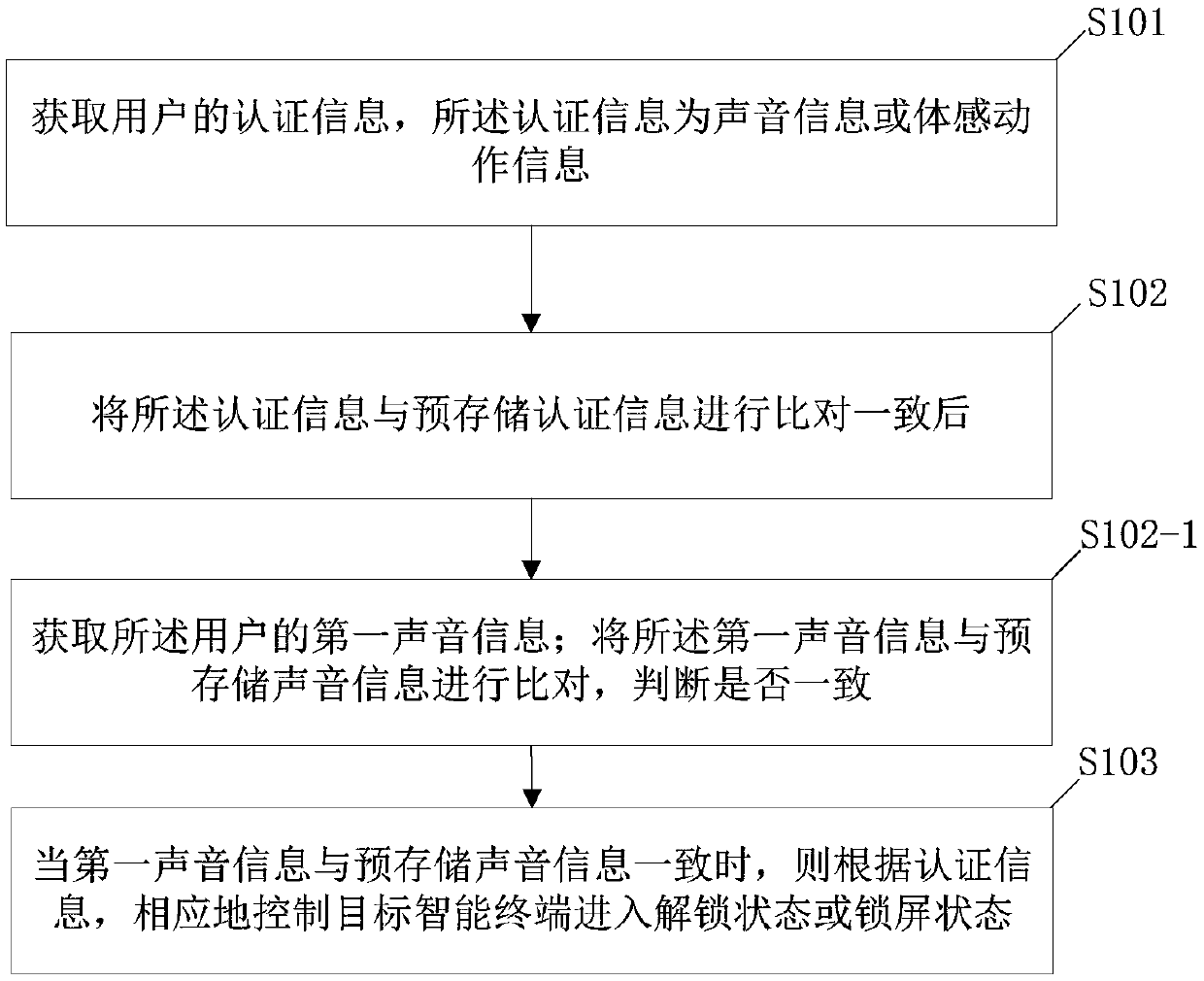
[0060] Therefore, based on the first embodiment above, see figure 2 , between the above step 102 and step 103 may also include:
[0061] Step 102-1. When the authentication information is motion information, after the authentication information is compared with the pre-stored authentication informati...
Embodiment 3
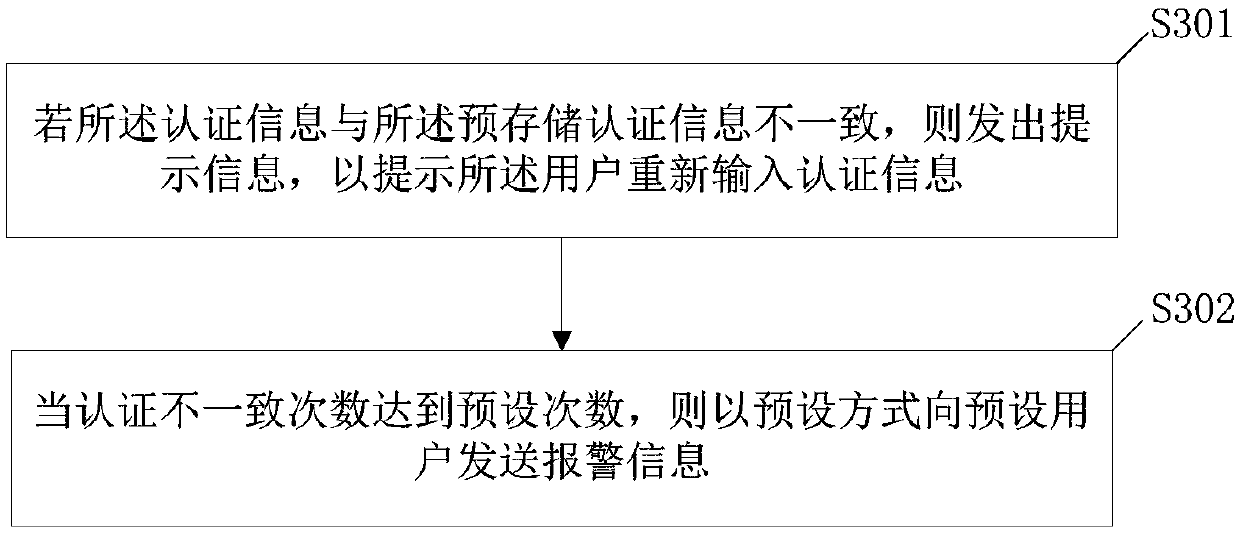
[0066] Based on any of the above embodiments, see image 3 , after comparing the above-mentioned authentication information with the pre-stored authentication information and judging whether they are consistent, the following steps may also be included:
[0067] Step 301, if the authentication information is inconsistent with the pre-stored authentication information, send a prompt message to prompt the user to re-enter the authentication information;
[0068] Step 302, when the number of times of authentication inconsistencies reaches a preset number, send an alarm message to a preset user in a preset manner.
[0069] It should be noted that the above-mentioned preset method may be, but not limited to, email, short message, etc., and the preset user refers to a pre-designated recipient of the alarm information. The preset number of times can be manually set according to actual needs. Generally, the preset number of times can be set to 3 or 5 times.
[0070] see Figure 4 ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com