Privacy protection clustering method for big data analysis and computer storage medium
A technology of privacy protection and clustering method, which is applied in the field of privacy protection clustering method and computer storage medium, which can solve the problems of large random noise, privacy leakage of big data clustering mining, affecting the quality of clustering results, etc., and achieve high clustering Availability, effects of good clustering quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
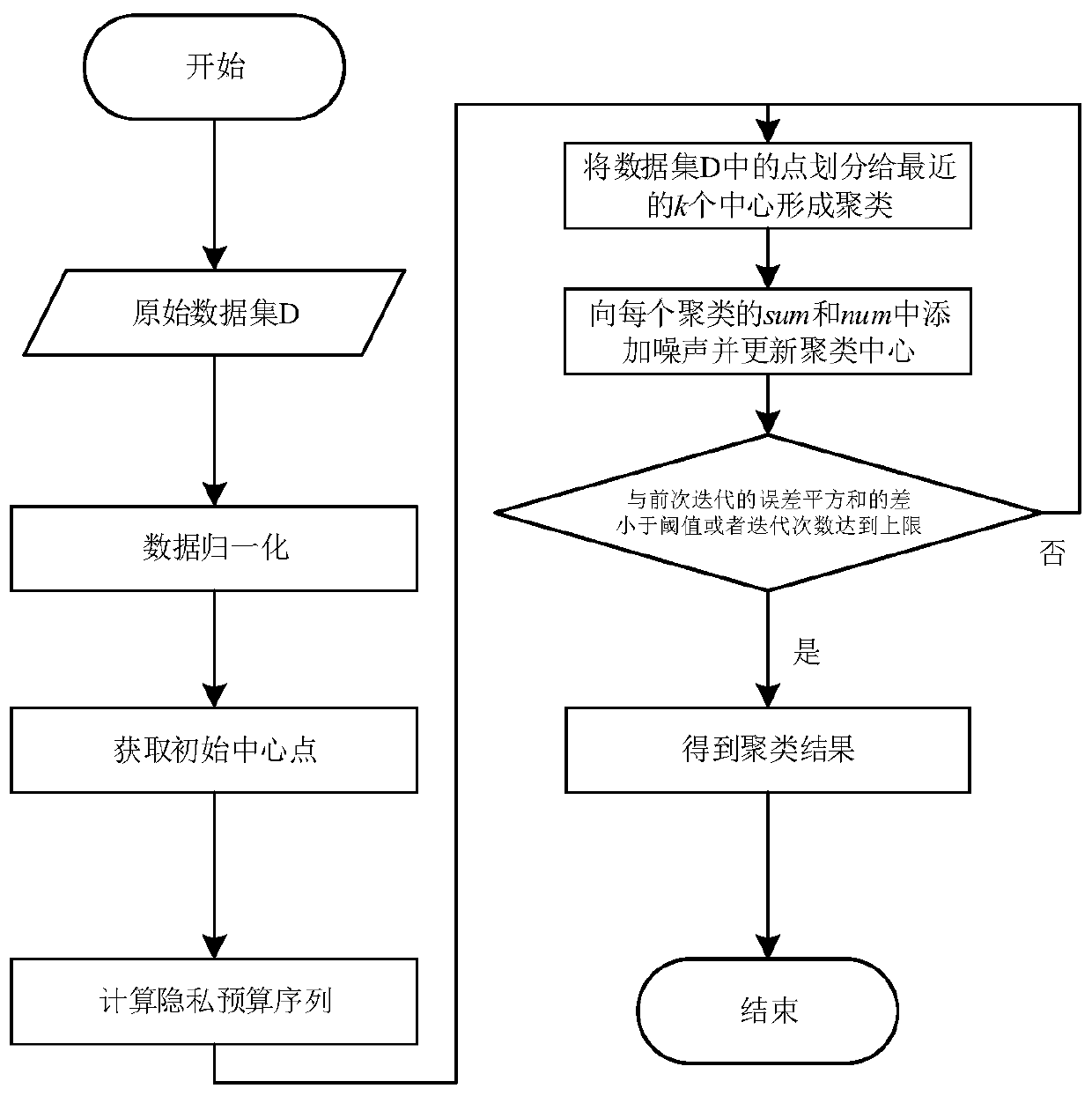
[0031] The flow chart of the method in this embodiment is as follows figure 1 As shown, the specific steps are as follows:
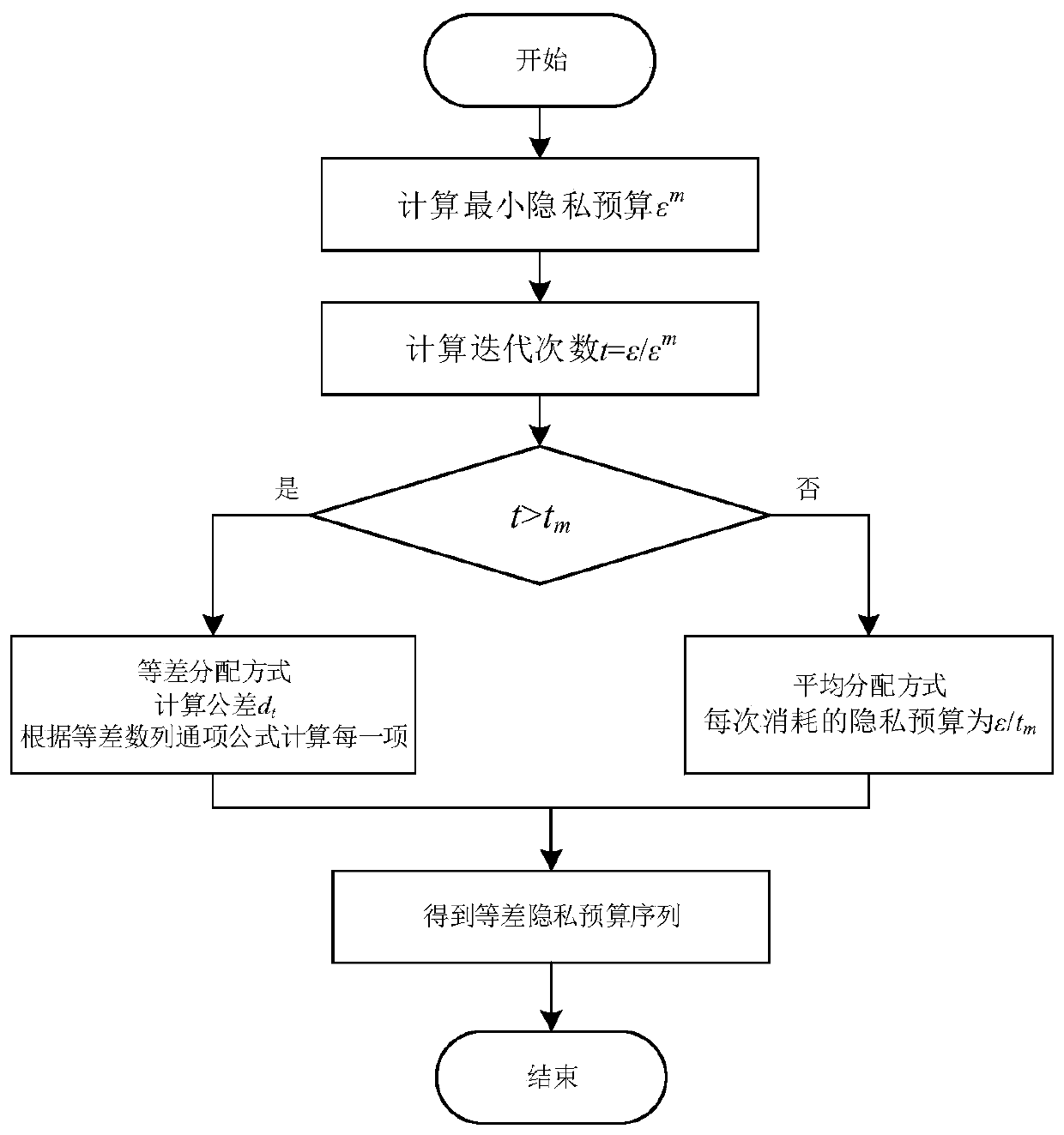
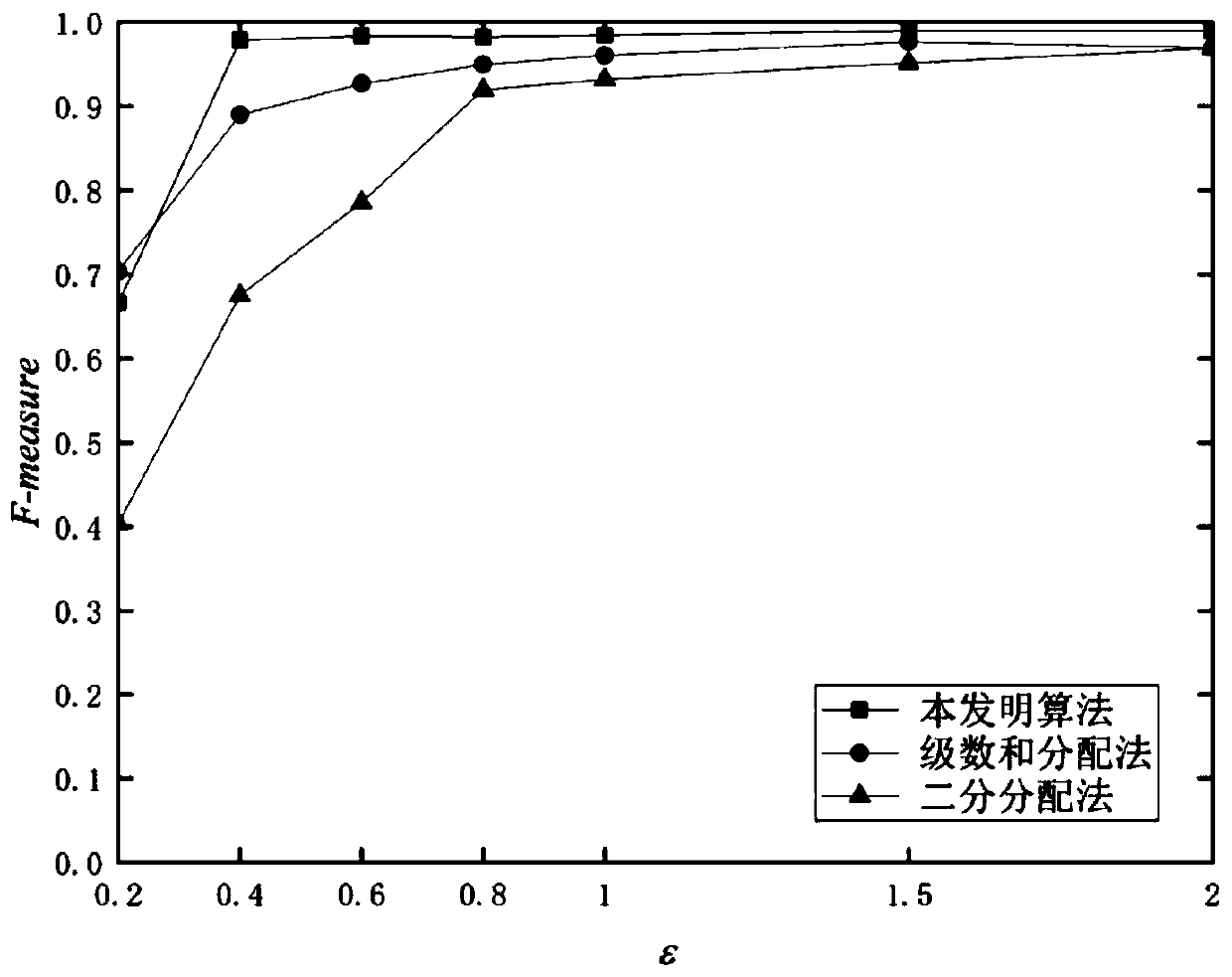
[0032] Step 1, the existing Image.csv dataset, which comes from the clustering dataset of the School of Computer Science, University of Eastern Finland (http: / / cs.joensuu.fi / sipu / datasets / ). Record the data set as D, the number of records N in the data set is 34112, and the data dimension d is 3, that is, each piece of data has 3 attributes. The total privacy budget ε controls the degree of privacy protection. The smaller ε is set, the greater the added noise and the higher the degree of privacy protection. Here, the total privacy budget ε is set to 0.8, the number of clusters k is 3, and each piece of data can be regarded as a sample point in the k-dimensional space. Normalize each dimension of the data set D to [0,1].
[0033] Data normalization is to scale each dimension of data to [0,1], which is performed by the following formula:
[0034]
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com