Network intrusion detection method based on information entropy and confidence down-sampling
A network intrusion detection and information entropy technology, applied in the field of unbalanced network intrusion detection and identification, can solve the problem that the sampling integration algorithm cannot effectively solve unbalanced network intrusions, and achieve the goal of improving generalization performance, reducing dependence, and suppressing information loss Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
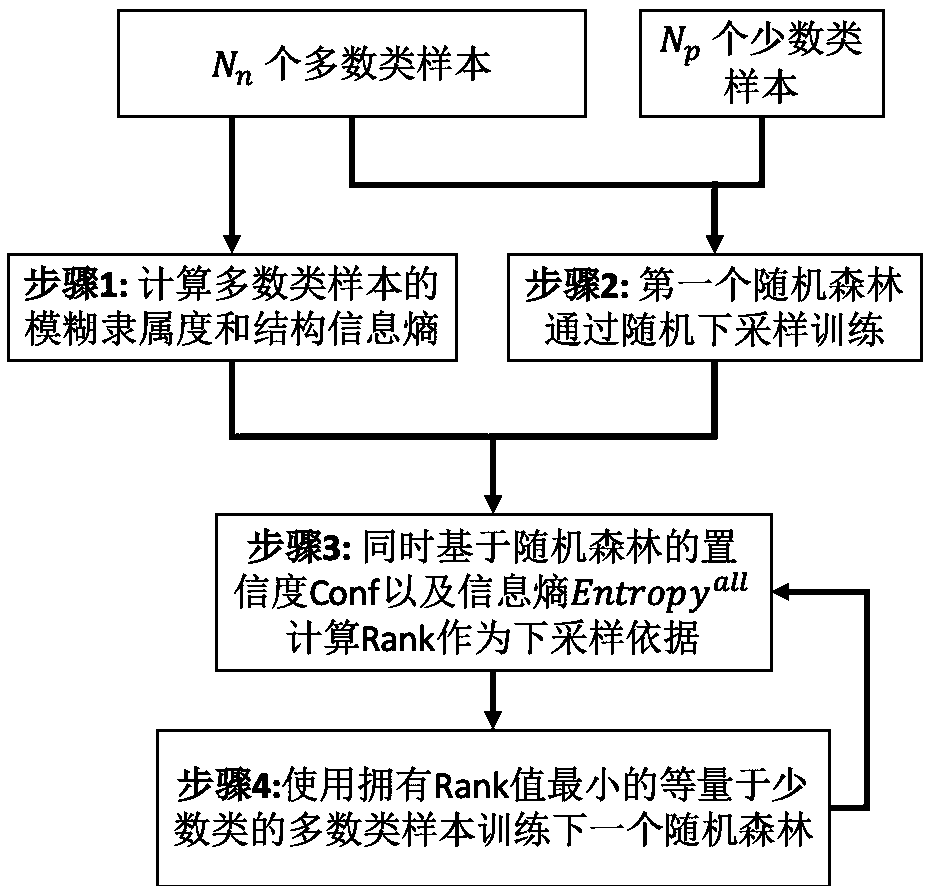
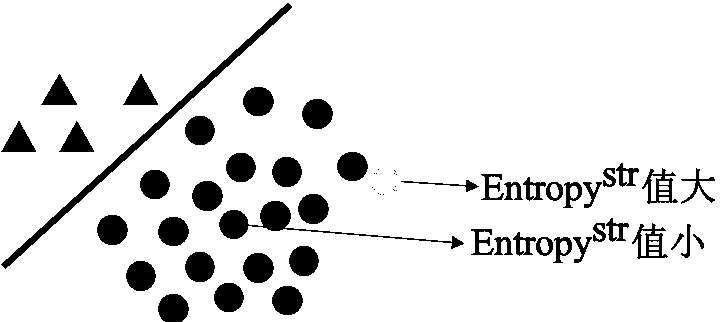
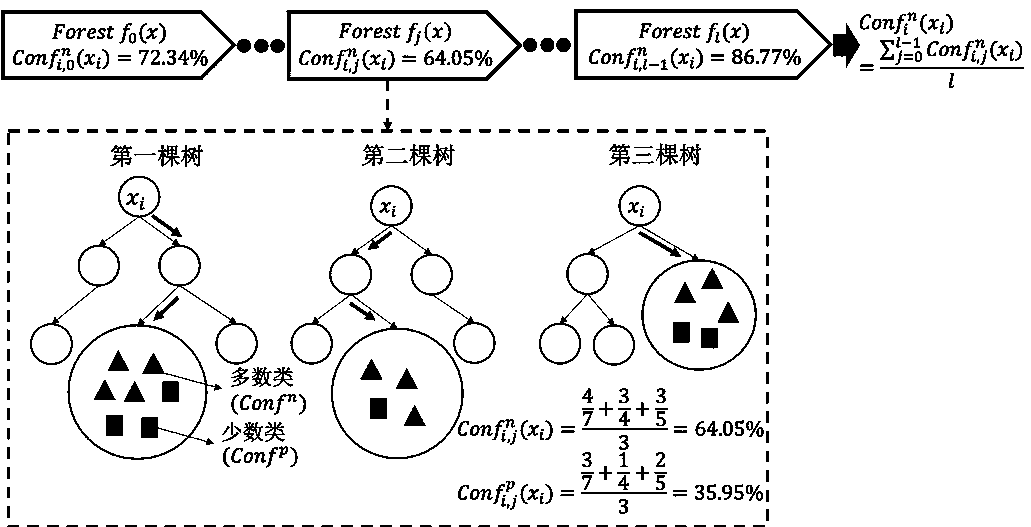
[0014] Below in conjunction with accompanying drawing and example the present invention will be further introduced: the system designed by the present invention is divided into four modules altogether.
[0015] Part I: Data Acquisition
[0016] The process of data collection is to convert real samples into data, and generate a data set represented by vectors for subsequent modules to process. In this step, the collected samples are divided into training samples and testing samples. The training samples are processed first. A training sample generates a vector Among them, i indicates that the sample is the i-th of the total training samples, and c indicates that the sample belongs to the c-th class. Each element of the vector corresponds to an attribute of the sample, and the dimension d of the vector is the number of attributes of the sample. For the convenience of subsequent calculations, all training samples are combined into a training matrix D, in which each row is a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com