Network security scanning function implementation method based on graphical programming
A graphical programming and network security technology, applied in the field of network security scanning function based on graphical programming, can solve problems such as no design method, and achieve the effect of improving timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The specific embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
[0061] Glossary:
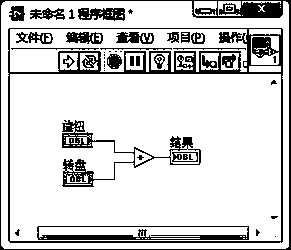
[0062] Atomic load: The atomic load in the present invention refers to the atomic function module, and the program is directly assembled from the atomic load and logical relations.
[0063] Graphic element / graphic module / visual display icon: The graphic element, graphical module and visual display icon in the present invention have the same meaning and can be interchanged, and all represent the representation of the atomic function module in the graphical interface.
[0064] Graphical programming: refers to the process of using basic graphic elements as programming elements to implement specific function software programming by adding, dragging and splicing graphic elements. This programming method frees users from tedious code writing, pays more attention to the realization of business functions, and can effectively improve progr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com