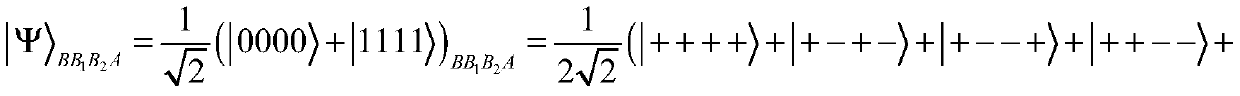Cluster state-based dynamic quantum agent blind signature method
A technology of proxy signature and proxy blindness, which is applied in key distribution, can solve the problems that the signature cannot be successful, and the dynamic attributes of the proxy signer are not considered.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
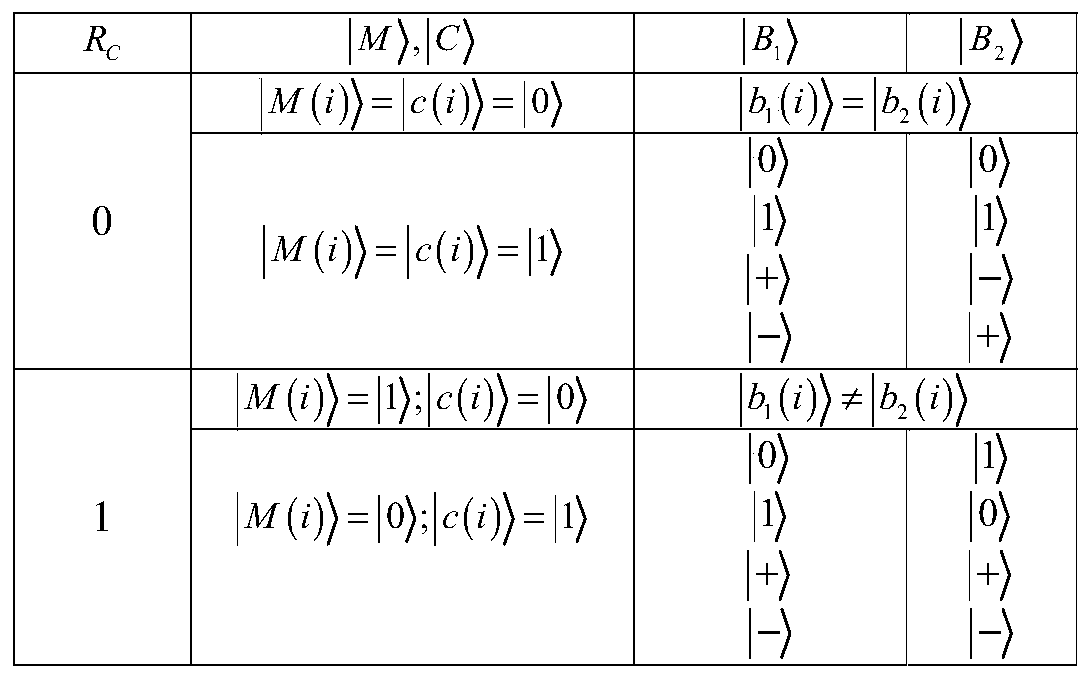
[0072] In this embodiment, a cluster state-based dynamic quantum agent blind signature method is disclosed. The method includes five communication parties, namely Alice, the message owner who holds the information to be signed, Bob, the initial signer who cannot sign normally, Proxy signer Bob1, proxy signer Bob2, and trusted receiver Charlie, where the message owner Alice stores the key k A , four-particle GHZ state subsequence S A and the four-particle cluster state subsequence S' A , the initial signer Bob stores the key k B and the four-particle GHZ state subsequence S B , the proxy signer Bob1 stores the key Four-particle GHZ state subsequence S B1 and the four-particle cluster state subsequence S" B1 , the proxy signer Bob2 stores the key Four-particle GHZ state subsequence S B2 and the four-particle cluster state subsequence S" B2 , the trusted receiver Charlie stores the key k A , key k B , key key and the four-particle cluster state subsequence S' C . ...
Embodiment 2
[0186] The method in this embodiment is used to add the proxy signer in the first embodiment. In the case of only one proxy signer in the first embodiment, a second proxy signer, David, is added.
[0187] Before the start of this method, there are 4 communicating parties, namely, the message owner Alice who holds the information to be signed, the initial signer Bob who cannot sign normally, the proxy signer Bob2, and the trusted receiver Charlie, in which the message owner Alice stores with key k A , four-particle GHZ state subsequence S A and the four-particle cluster state subsequence The initial signer Bob stores the key k B and the four-particle GHZ state subsequence S B , the proxy signer Bob2 stores the key Four-particle GHZ state subsequence S B2 and the four-particle cluster state subsequence The trusted receiver Charlie stores the key k A , key k B , key key and the four-particle cluster state subsequence This method is used to perform quantum proxy b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com