Alarming method and alarming device
A technology of location information and camera modules, which is applied in the field of data processing and can solve problems such as object danger
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
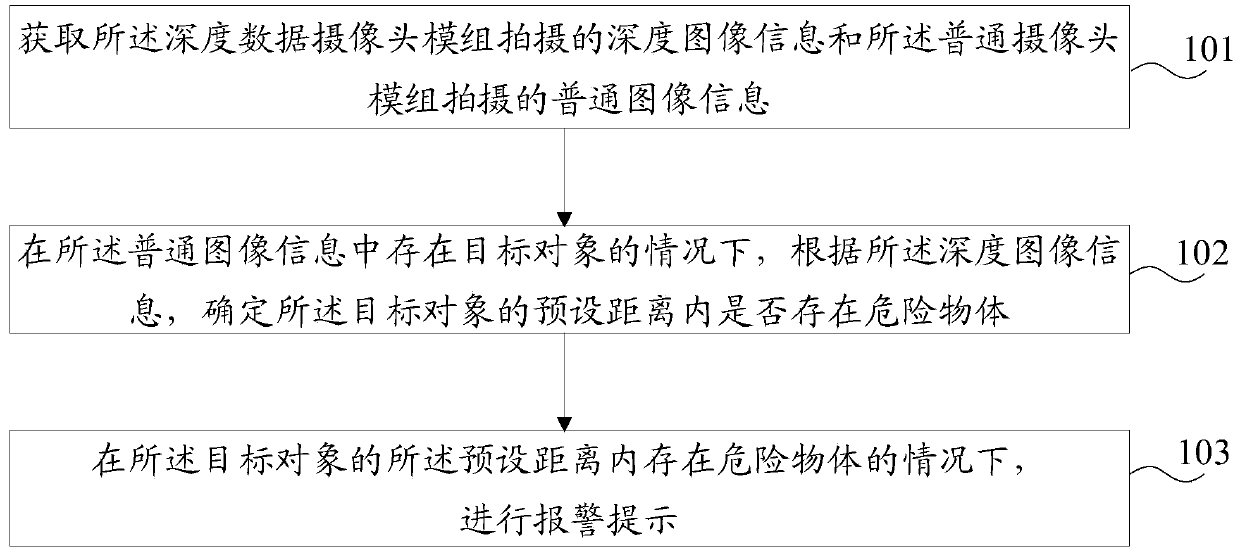
[0057] refer to figure 1 , figure 1 A flow chart of an alarm method provided by an embodiment of the present invention is shown. The alarm method is applied to a mobile terminal, and the mobile terminal may include: a mobile phone, a notebook, a tablet computer, and the like. In the embodiment of the present invention, there is no specific limitation on this.
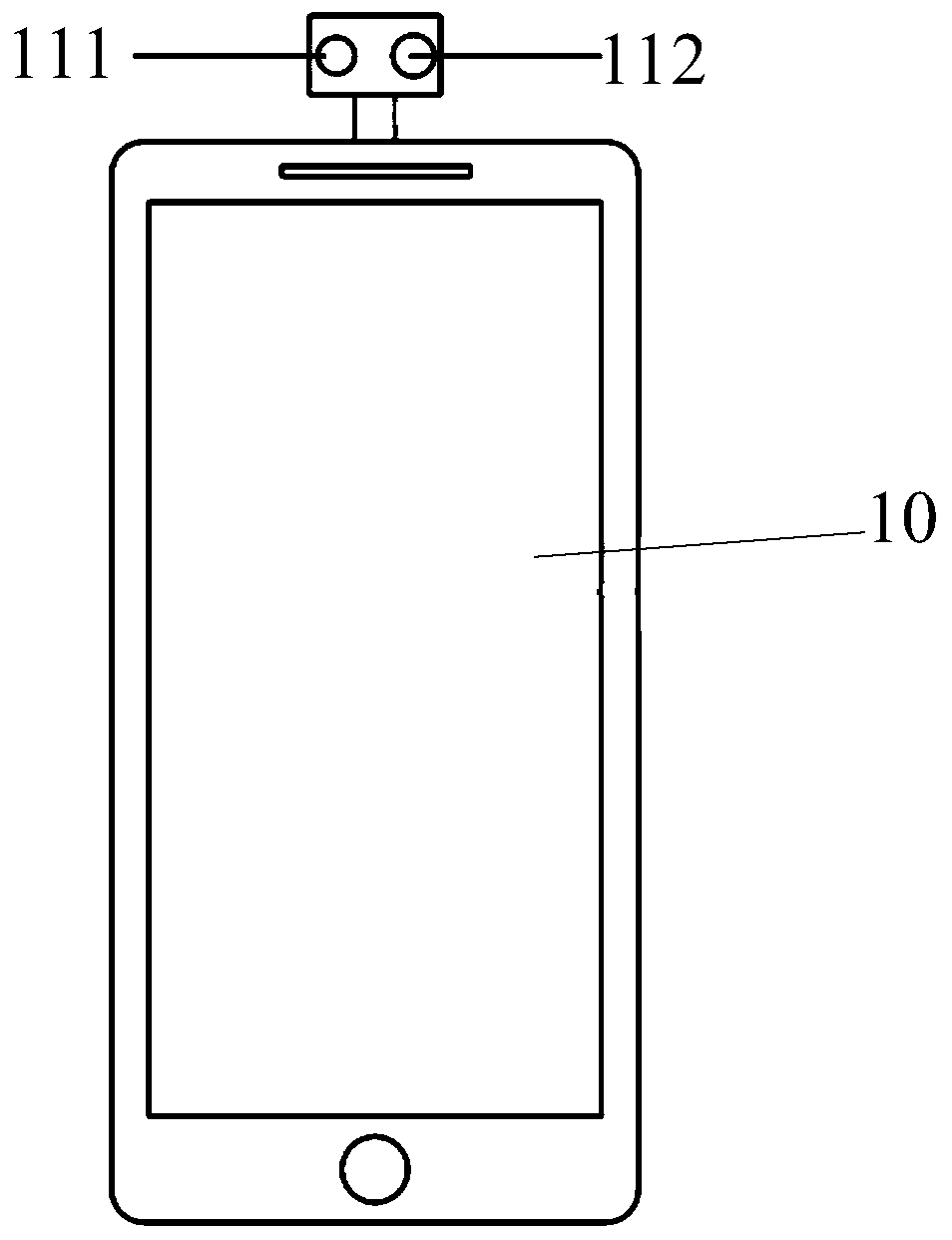
[0058] refer to figure 2 as shown, figure 2 A schematic structural diagram of a first type of mobile terminal provided by an embodiment of the present invention is shown. The mobile terminal 10 may include: a depth data camera module 111 and a common camera module 112 . In the embodiment of the present invention, the quantity and installation positions of the above-mentioned depth data camera modules 111 and common camera modules 112 are not specifically limited.
[0059] In the embodiment of the present invention, the difference between the imaging ranges of the above-mentioned depth data camera module 111 and t...
Embodiment 2
[0086] refer to image 3 , shows a flow chart of another alarm method provided by an embodiment of the present invention, the alarm method is also applied to a mobile terminal, and the mobile terminal includes: a depth data camera module and a common camera module; the above-mentioned depth data camera module The difference between the imaging range of the common camera module and the common camera module is within the preset difference range. For the depth data camera module and the common camera module, reference may be made to the relevant records in the above embodiments. In order to avoid repetition, details are not repeated here. The method specifically may include the following steps:
[0087]Step 201, determine the location information of the target object.
[0088] In the embodiment of the present invention, the location information of the target object may be determined. Specifically, depth image information or general image information of the target object may be ...
Embodiment 3
[0110] refer to Figure 8 , showing a flow chart of another alarm method provided by an embodiment of the present invention, the alarm method is also applied to a mobile terminal, and the mobile terminal includes: a depth data camera module and a common camera module; the above-mentioned depth data camera module The difference between the imaging range of the common camera module and the common camera module is within the preset difference range. For the depth data camera module and the common camera module, reference may be made to the relevant records in the above embodiments. In order to avoid repetition, details are not repeated here. The method specifically may include the following steps:
[0111] Step 301, acquire the depth image information captured by the depth data camera module and the normal image information captured by the common camera module.
[0112] In the embodiment of the present invention, for the above step 301, reference may be made to the related recor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com