Security protection method, security protection device, computer device and computer readable storage medium
A computer program and security technology, applied in the field of data processing, can solve problems such as loss or damage, failure to supervise and manage, access control system does not have access management registration, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
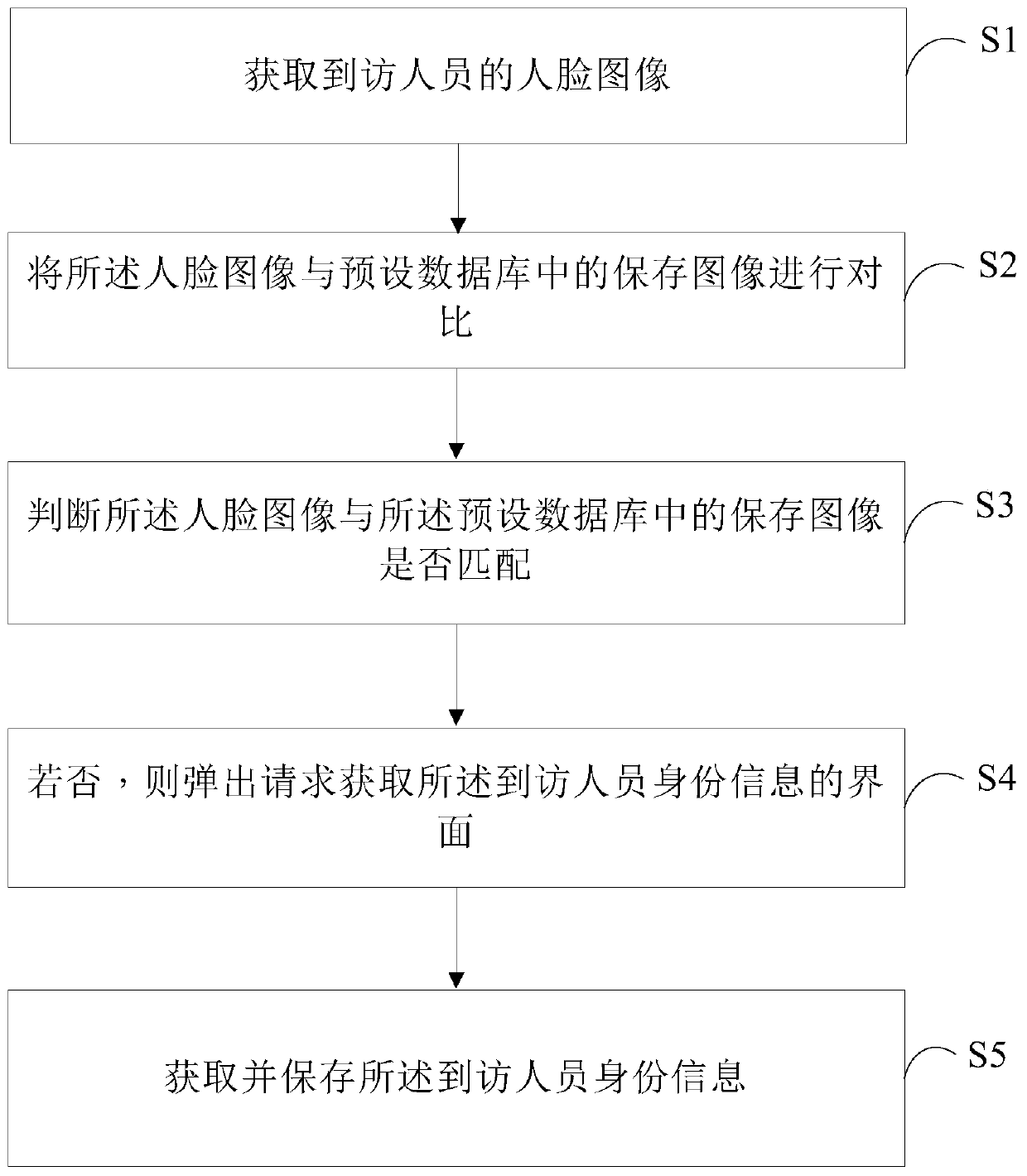
[0052] figure 1 It is a flow chart of steps in a preferred embodiment of the security method of the present invention. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0053] refer to figure 1 As shown, the security method specifically includes the following steps.
[0054] Step S1, acquiring the face image of the visitor.
[0055] In this embodiment, after the visitor passes through the access control, the camera installed on the terminal scans the visitor to obtain the face image of the visitor. During face scanning, a voice prompt similar to "Face recognition is about to enter, please do not leave" can be issued. Wherein, the identity information of the visitor refers to an internal employee or an external visitor. And when the identity information of the visitor is an internal employee, the personal information of the internal employee is retrieved and displayed on the interface for checking....
Embodiment 2
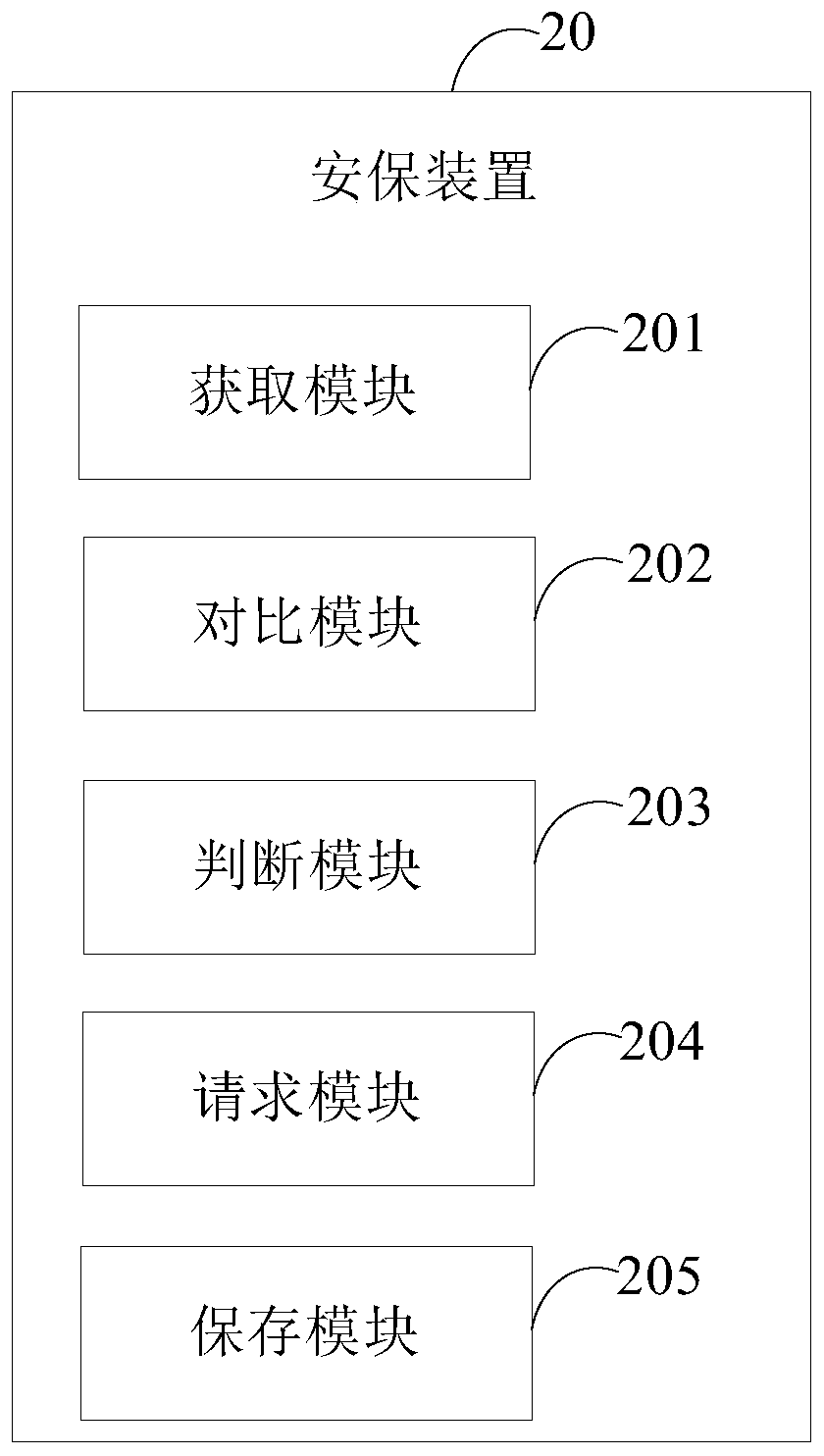
[0083] figure 2 It is a functional block diagram of a preferred embodiment of the security device of the present invention.
[0084] refer to figure 2 As shown, the security device 20 may include an acquisition module 201 , a comparison module 202 , a judgment module 203 , a request module 204 and a save module 205 .
[0085] The acquiring module 201 is used to acquire the face images of visitors.
[0086] In this embodiment, after the visitor passes through the access control, the acquiring module 201 scans the visitor through the camera installed on the terminal, so as to acquire the face image of the visitor. During face scanning, a voice prompt similar to "Face recognition is about to enter, please do not leave" can be issued. Wherein, the identity information of the visitor refers to an internal employee or an external visitor. And when the identity information of the visitor is an internal employee, the personal information of the internal employee is retrieved and...
Embodiment 3
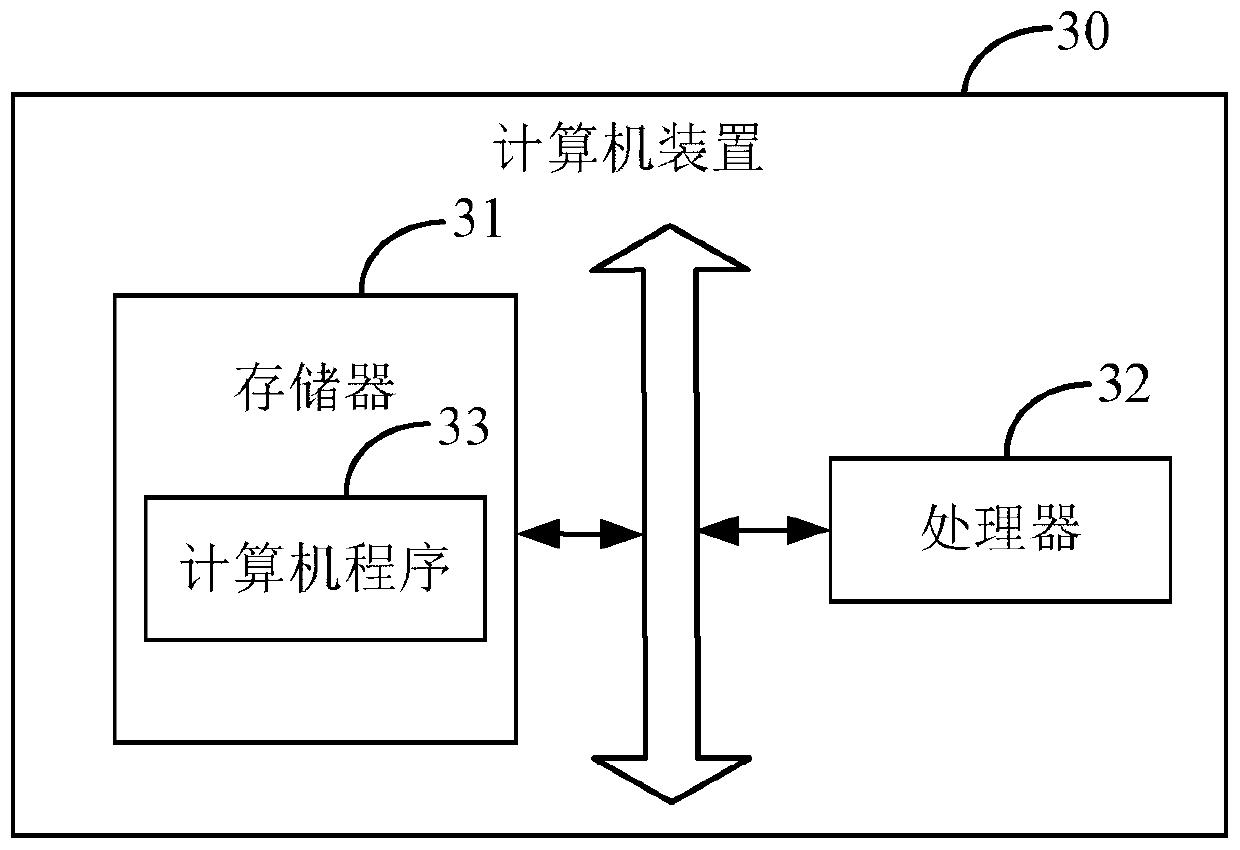
[0114] image 3 It is a schematic diagram of a preferred embodiment of the computer device of the present invention.
[0115] The computer device 30 includes a memory 31 , a processor 32 and a computer program 33 stored in the memory 31 and operable on the processor 32 , such as a mobile phone control program. When the processor 32 executes the computer program 33, the steps in the above security method embodiments are implemented, for example figure 1 Steps S1-S5 are shown. Alternatively, when the processor 32 executes the computer program 33, it realizes the functions of each module in the above security device embodiment, for example figure 2 Modules 201-205 in .
[0116] Exemplarily, the computer program 33 can be divided into one or more modules / units, and the one or more modules / units are stored in the memory 31 and executed by the processor 32 to complete this invention. The one or more modules / units may be a series of computer program instruction segments capable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com