Image encryption method based on composite chaotic system and image processing device
A technology of chaotic system and encryption method, which is applied in the direction of image data processing, image data processing, electrical digital data processing, etc., can solve the problems of bad chaotic behavior, high possibility of being attacked, and narrow chaotic range, so as to reduce the The probability of attack, the effect of increasing the robustness, and widening the range of chaos
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] see figure 1 The image encryption method based on the composite chaotic system provided by Embodiment 1 of the present invention includes the following steps:
[0027] S101. Using the Sine map, the Tent map and the Logistic map as seed maps, using cascade operations and nonlinear combinations to expand the chaotic range to generate a compound chaotic system.
[0028] In Embodiment 1 of the present invention, the nonlinear combination specifically includes addition and modulo operation.
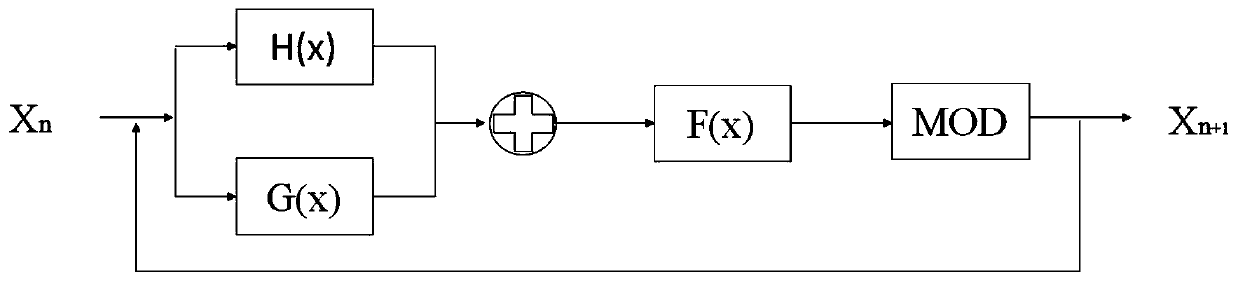
[0029] The structure diagram of compound chaotic system is as follows: figure 2 shown. The definition formula of compound chaotic system is:
[0030] x n+1 =F(G(x n )+H(x n ))mod1 (1)
[0031] Among them, F(x), G(x) and H(x) are three seed maps. In Embodiment 1 of the present invention, Sine mapping, Tent mapping and Logistic mapping are selected as seed mapping, x n is the iteration value, x n+1 is the output of the composite chaotic system, and the mod operation is to ensur...
Embodiment 2
[0089] Embodiment 2 of the present invention provides a computer-readable storage medium, the computer-readable storage medium stores a computer program, and when the computer program is executed by a processor, the complex chaos system based Steps of an image encryption method.
Embodiment 3
[0091] Figure 8 A specific structural block diagram of an image processing device provided in Embodiment 3 of the present invention is shown. An image processing device 100 includes: one or more processors 101, memory 102, and one or more computer programs, wherein the processor 101 and the memory 102 are connected by a bus, the one or more computer programs are stored in the memory 102, and configured to be executed by the one or more processors 101, and the processor 101 executes the The computer program is used to realize the steps of the image encryption method based on the composite chaotic system provided in Embodiment 1 of the present invention.
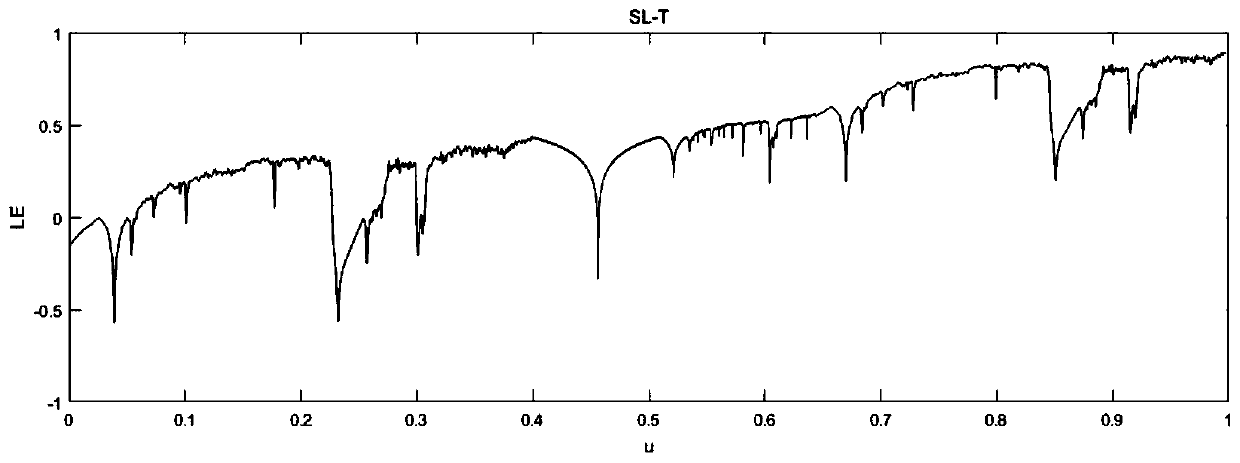
[0092]In the present invention, Sine mapping, Tent mapping and Logistic mapping are used as seed mapping, and cascade operation and nonlinear combination are used to expand the chaotic range to generate a composite chaotic system; the composite chaotic system is used to generate a chaotic sequence to pre-encrypt the plaintext...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com