Interceptor configuration method and device, storage medium and electronic equipment
A configuration method and interceptor technology, which is applied in the field of data processing, can solve problems such as business method transactions that cannot be submitted, and achieve the effects of improving user experience, ensuring normal processing, and meeting user requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] Specific embodiments of the present disclosure will be described in detail below in conjunction with the accompanying drawings. It should be understood that the specific embodiments described here are only used to illustrate and explain the present disclosure, and are not intended to limit the present disclosure.
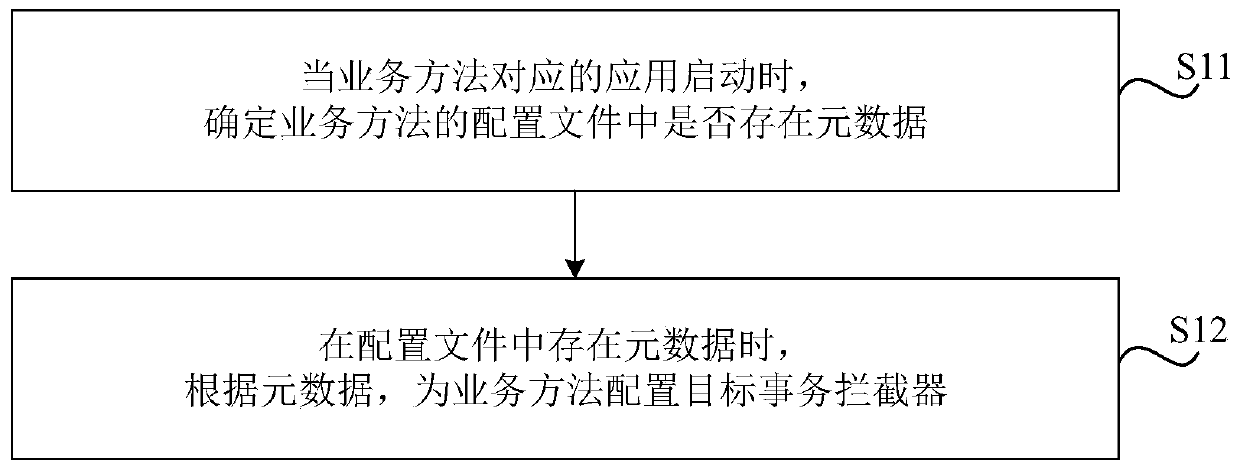
[0047] figure 1 As shown, it is a flowchart of an interceptor configuration method provided according to an embodiment of the present disclosure. As an example, a proxy class can be created, and the following methods can be executed when the proxy class is implemented, and corresponding interception can be configured for each business method device, specifically, such as figure 1 As shown, the method includes:
[0048] In S11, when the application corresponding to the business method is started, it is determined whether there is metadata in the configuration file of the business method, wherein the metadata is generated when the business method is created a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com