Agent behavior safety monitoring method and device, computer equipment and storage medium
A security monitoring and computer program technology, applied in the field of agent behavior security monitoring, can solve the problems of high risk rate in the face-to-face process, and achieve the effect of monitoring and reducing the risk rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
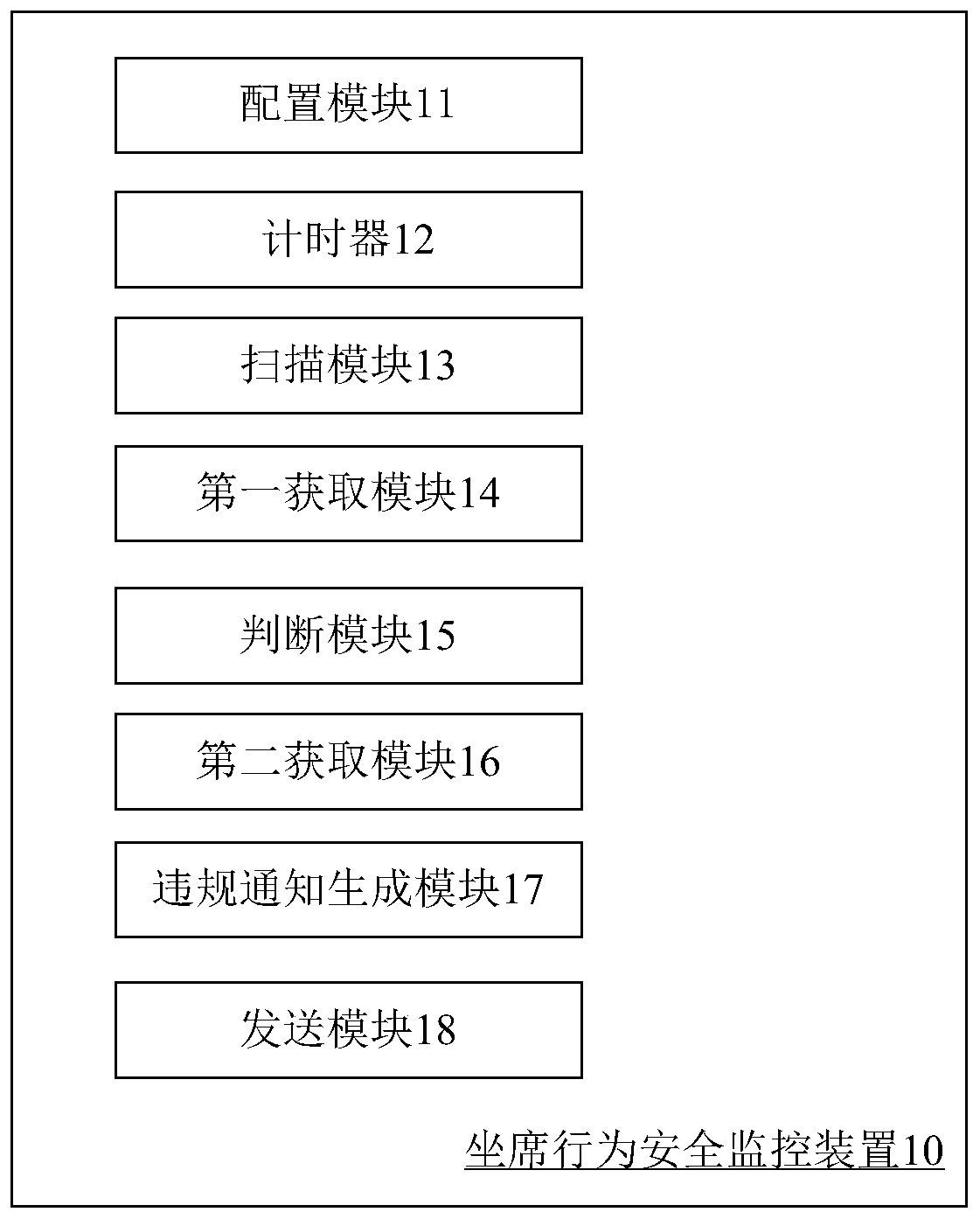
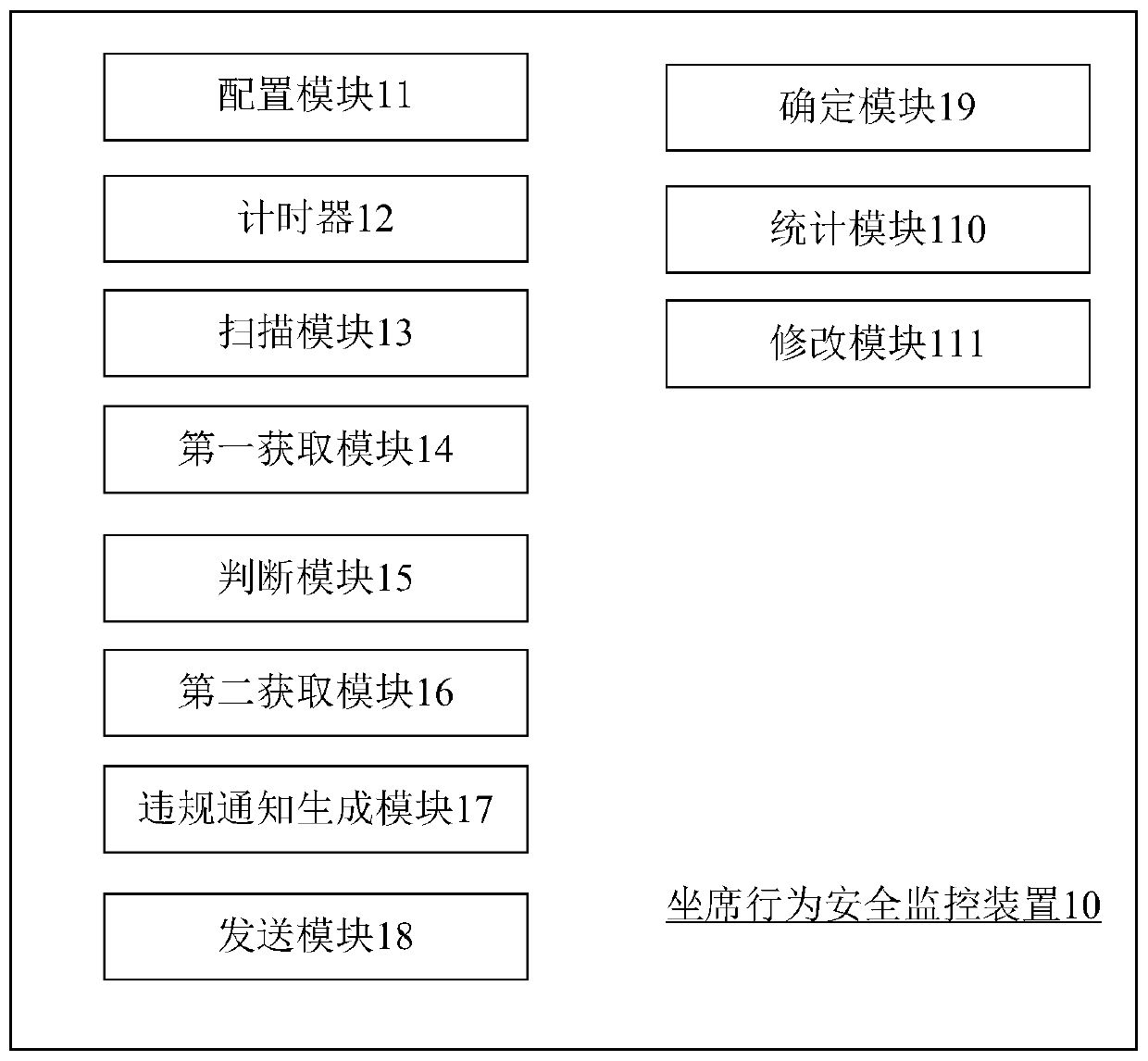
Image
Examples
Embodiment 1
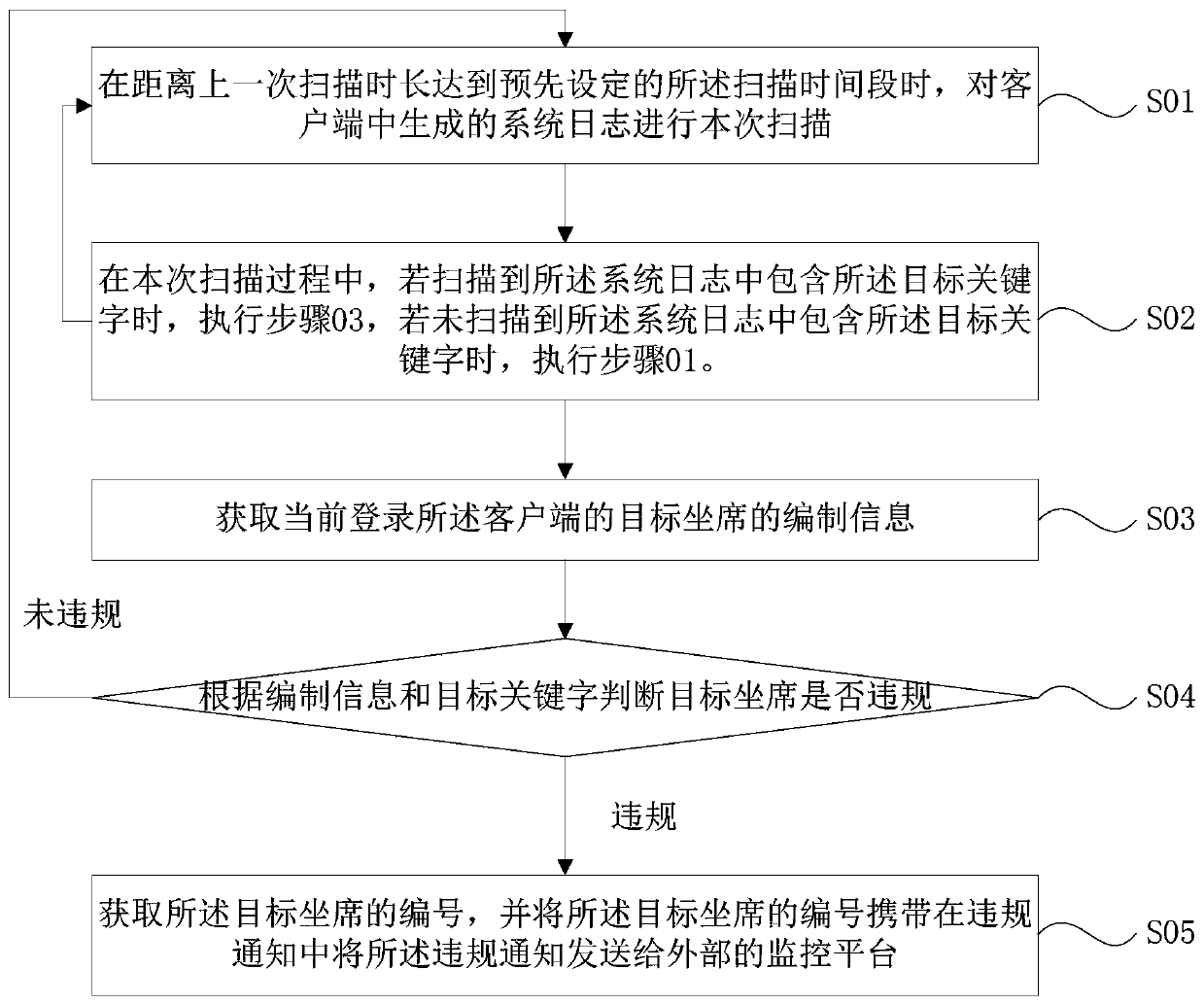
[0043] see figure 1 , in a kind of agent behavior security monitoring method of the present embodiment, comprise the following steps:
[0044] Step 01, when the time from the last scan reaches the preset scan time period, perform this scan on the system log generated in the client.
[0045] System logs are information that records hardware, software, and system problems in the system, and can also monitor events that occur in the system. Users can use it to check why the error occurred, or to find traces left by the attacker when it was attacked. During the process of using the client to handle business, the operations performed by the agent will generate system logs. Therefore, the monitoring of the agent phone can be realized by scanning the system log.
[0046] In this embodiment, in order to monitor the agent's phone, it is necessary to pre-set the target keyword and the scanning time period.
[0047] In this embodiment, the target keyword is the first character used t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com