A decentralized chip research and development transaction data storage method and system
A technology for trading data and storage systems, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
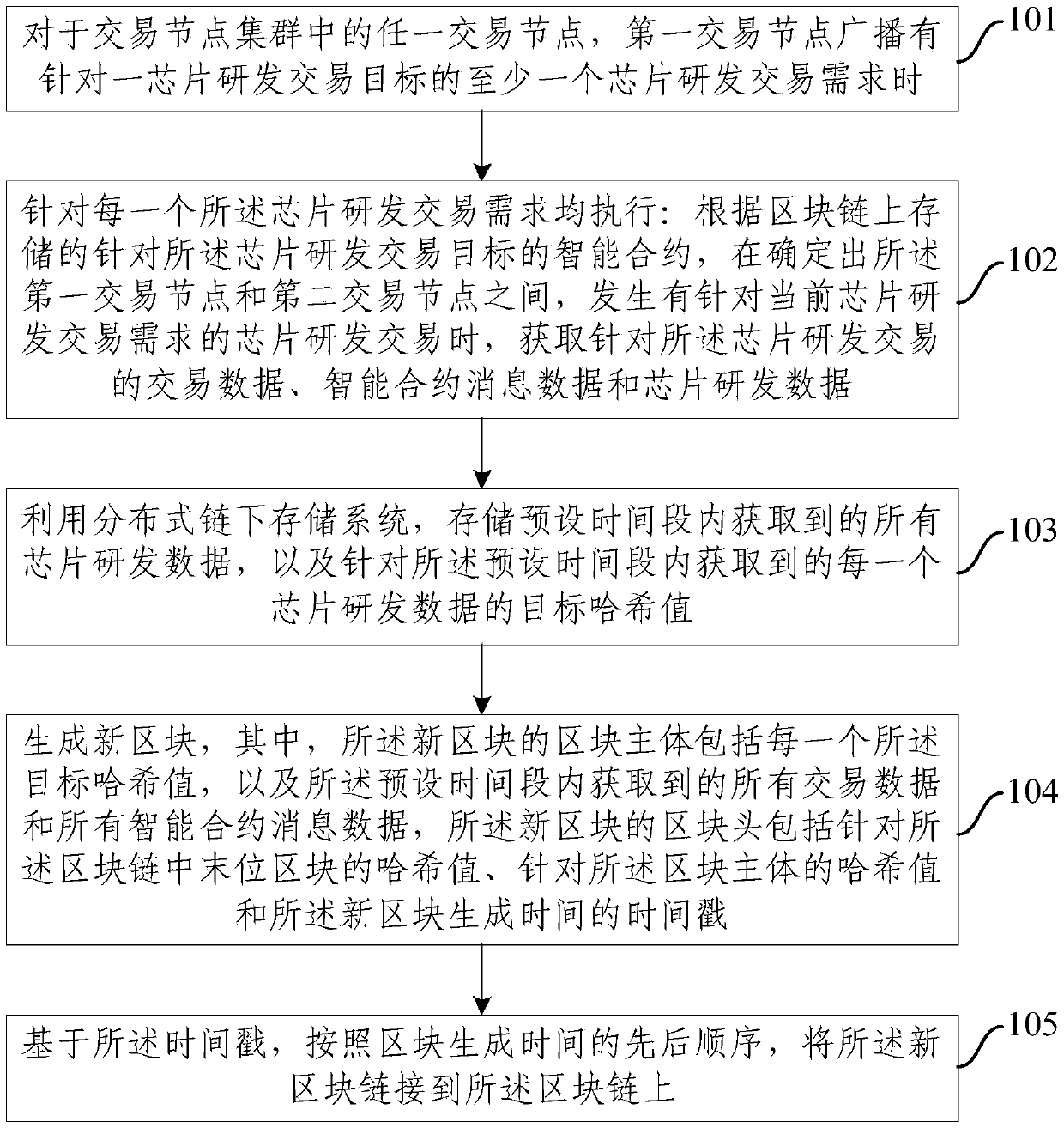
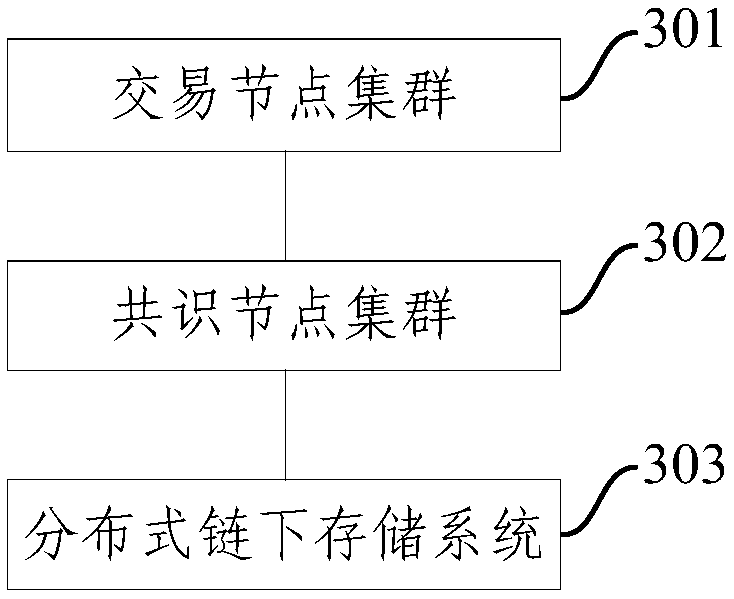
[0033] Such as figure 1 As shown, Embodiment 1 provides a decentralized chip research and development transaction data storage method, which may include the following steps:
[0034] Step 101: For any trading node in the trading node cluster, when the first trading node broadcasts at least one chip research and development transaction demand for a chip research and development transaction target, execute step 102.
[0035] Step 102: Execute for each of the chip research and development transaction requirements: according to the smart contract for the chip research and development transaction target stored on the block chain, between the first transaction node and the second transaction node are determined, When there is a chip research and development transaction for the current chip research and development transaction demand, the transaction data, smart contract message data and chip research and development data for the chip research and development transaction are obtained...
Embodiment 2
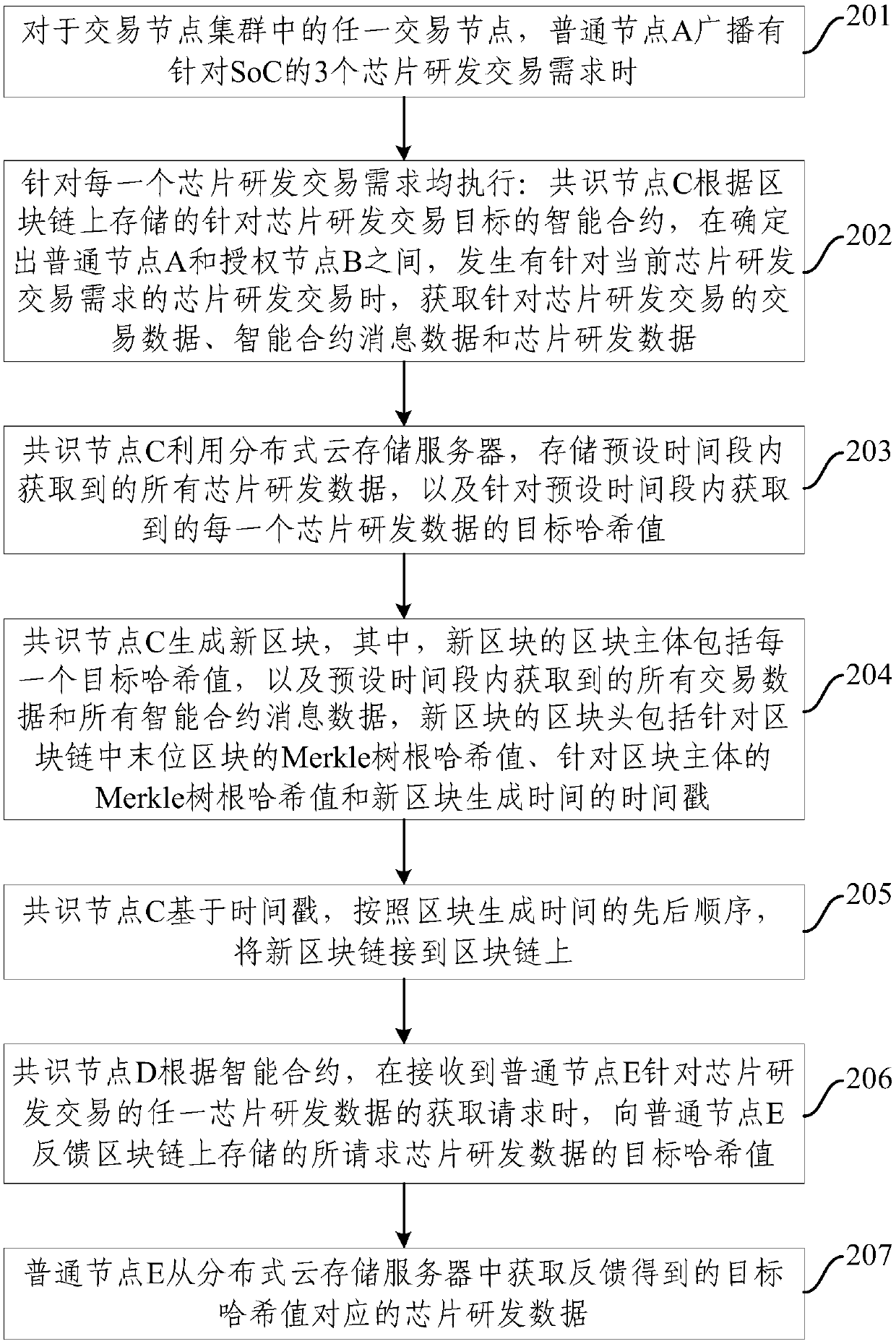
[0053] Embodiment 2 is basically the same as Embodiment 1, and the similarities will not be repeated. The difference is: the first transaction node is: an authorized node with consensus power, which does not involve the block construction process but has the right to read the block Ordinary nodes, any of the visitor nodes that do not involve the block construction process, do not have block reading rights, have transaction rights and can read transaction information related to themselves;
[0054] The second transaction node is: any one of the authorized node, the normal node and the visitor node;
[0055] The authorized nodes include business entity nodes and business individual nodes.
[0056] In detail, guest nodes, ordinary nodes and authorized nodes can all be used as transaction nodes to conduct transactions with other transaction nodes. Among them, the guest node can become an ordinary node after being authorized, the ordinary node can become an authorized node after b...
Embodiment 3
[0059] Embodiment 3 is basically the same as Embodiment 1, and the similarities will not be repeated. The difference is that the method may further include: performing at least one transaction data and all smart contract message data included in the block body. The double-hash algorithm is combined with two-by-two splicing operations to obtain a Merkle tree root hash value as the hash value for the block body.
[0060] Correspondingly, the hash value of the previous block can also be the root hash value of the Merkle tree of the previous block.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com