Data searchable encryption and keyword search method, system, terminal and device
An encryption method and keyword technology, applied in file systems, digital data protection, electronic digital data processing, etc., can solve problems such as troublesome operation, limited searchable keywords, and increased data set construction time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
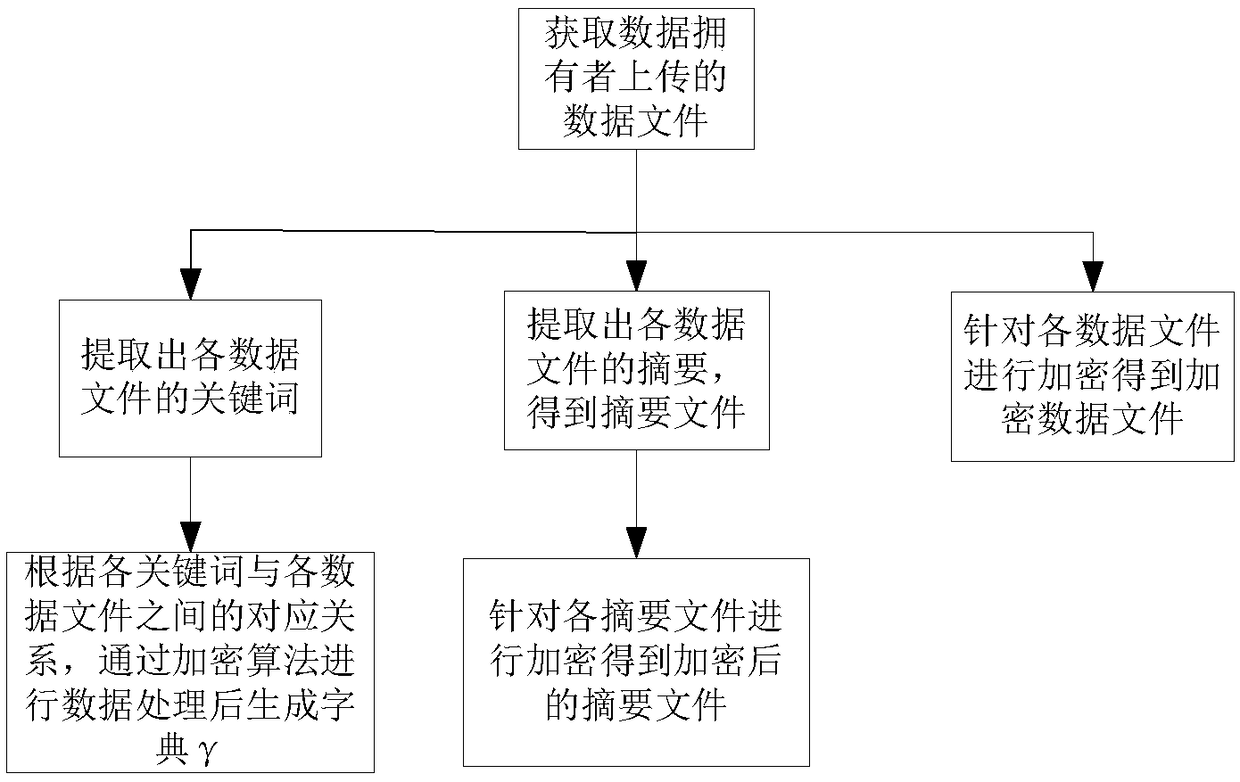
[0111] This embodiment discloses a data searchable encryption method, such as figure 1 As shown, the steps are as follows:
[0112] Step S1, obtaining the data file uploaded by the data owner;
[0113] Step S2, extracting the keywords of each data file; performing abstract extraction on each data file at the same time to obtain an abstract file; wherein, in this embodiment, the process of obtaining each abstract file is as follows:
[0114] First, extract the summary file from the data file through the document summary extraction algorithm; then use the file number corresponding to the summary as an index to store the summary in the corresponding position, and fill the remaining positions with characters to form a summary file.
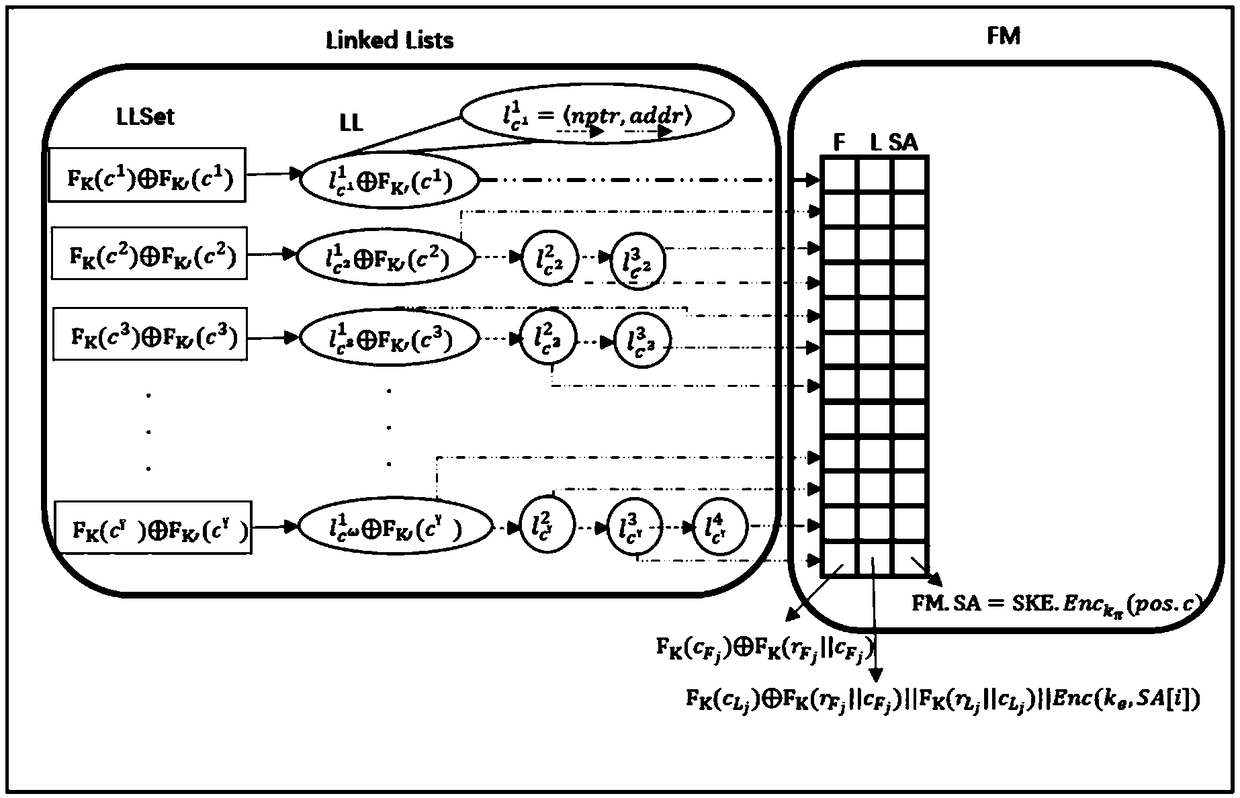
[0115] Step S3, according to the corresponding relationship between each keyword and each data file, generate a dictionary γ after performing data processing through an encryption algorithm, wherein the dictionary γ stores the tags corresponding to e...
Embodiment 2
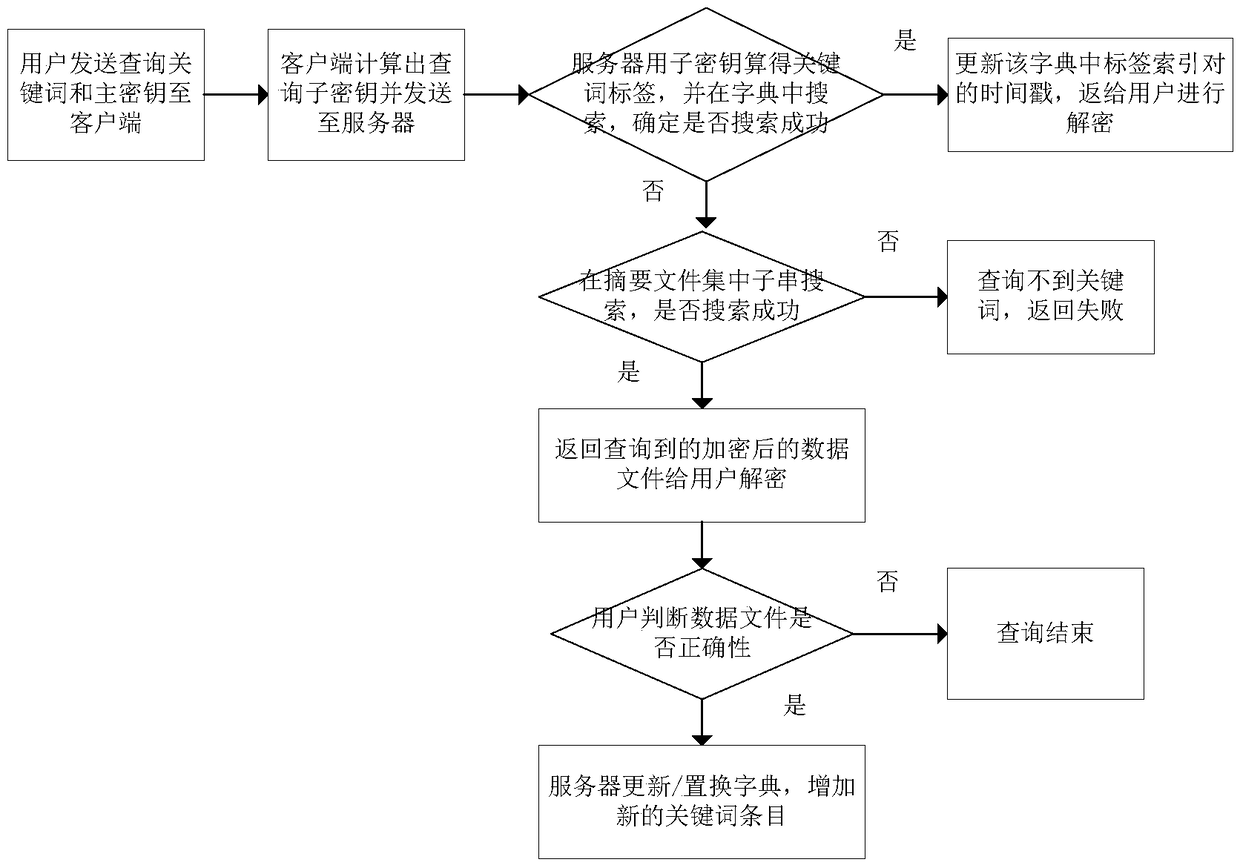
[0147] This embodiment discloses a keyword search method, such as figure 2 As shown, the steps are as follows:
[0148] Step X1, first obtain the dictionary γ obtained by the data searchable encryption method of the embodiment, the encrypted data file and the encrypted summary file;
[0149] When receiving the keywords sent by the user that need to be searched, first determine whether there is an encrypted data file that includes the keyword through the search dictionary γ; if so, return the corresponding encrypted data file to the user as a query result Decrypt; if not, enter step X2;
[0150] Wherein in the present embodiment, for each keyword that needs to be searched, the specific process of determining whether the keyword is included in the encrypted data file by searching the dictionary γ is as follows:
[0151] Step X11, for each keyword that the user needs to search, generate a pair of sub-keys K' for the keyword according to the master key K issued by the user 1 ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com