Sequence attack detection method and device
A detection method and sequence technology, applied in computer security devices, instruments, calculations, etc., can solve problems affecting ICS high real-time performance, safety is not considered, system abnormalities, etc., to solve the problem of undetectable operation sequence, realize intrusion detection, The effect of expanding the detection range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
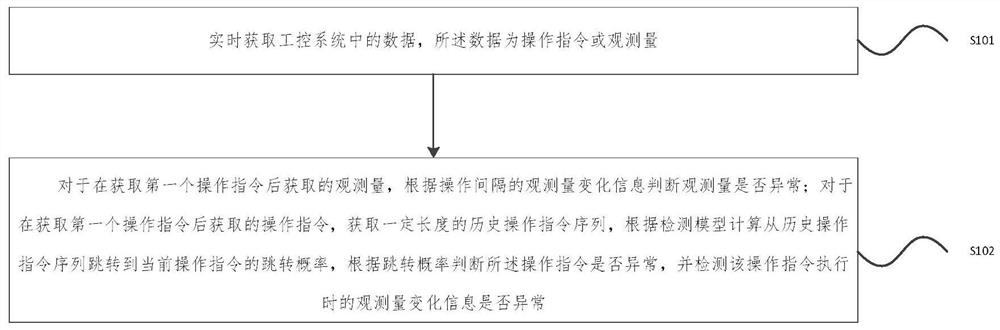
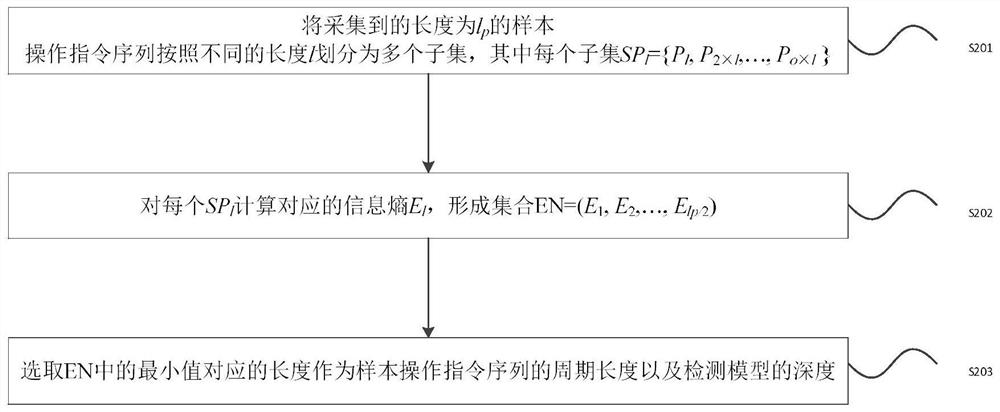
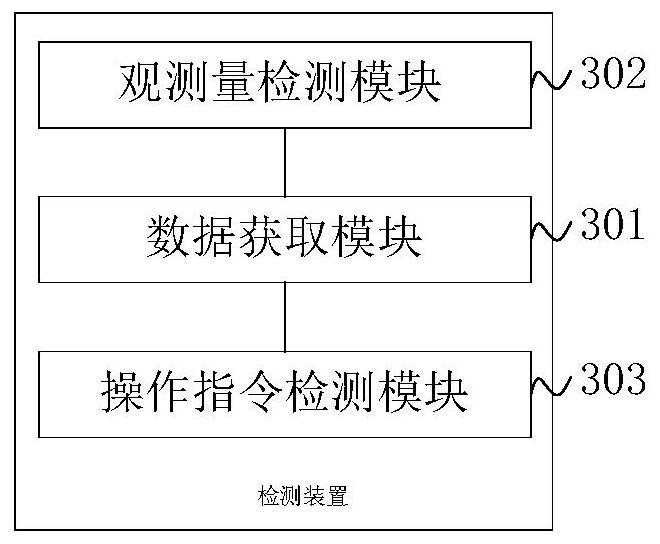
[0028] In order to overcome the shortcomings of the controller sequence attack detection method in the prior art, such as incomplete detection and great influence by data authenticity, the sequence attack cannot be effectively identified, causing serious service interruption and equipment damage, the embodiment of the present invention adopts The analysis of the controller shows that the controller not only receives the control flow data, but also receives the state flow data. The control flow data and the state flow data are bound by the business process of the system, and they are closely related. They can mutually verify the correctness of their respective data. The inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com