Method and apparatus for deleting security-relevant information in a device
A technology related to information and equipment, applied in the direction of security devices, computer security devices, wireless communications, etc., can solve the problem that the manipulation sensor no longer operates the anti-manipulation function correctly
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Many devices with microprocessors, such as computers, and field devices in robots, aircraft, vehicles or perhaps automation devices use encryption methods in order to communicate with communication partners in a manipulation-proof manner and / or, for example, can use Radionavigation applications of anti-manipulation signals. To this end, security-relevant information, such as encryption keys used in the encryption method, is stored in the corresponding device or is arranged in a special device in the device.
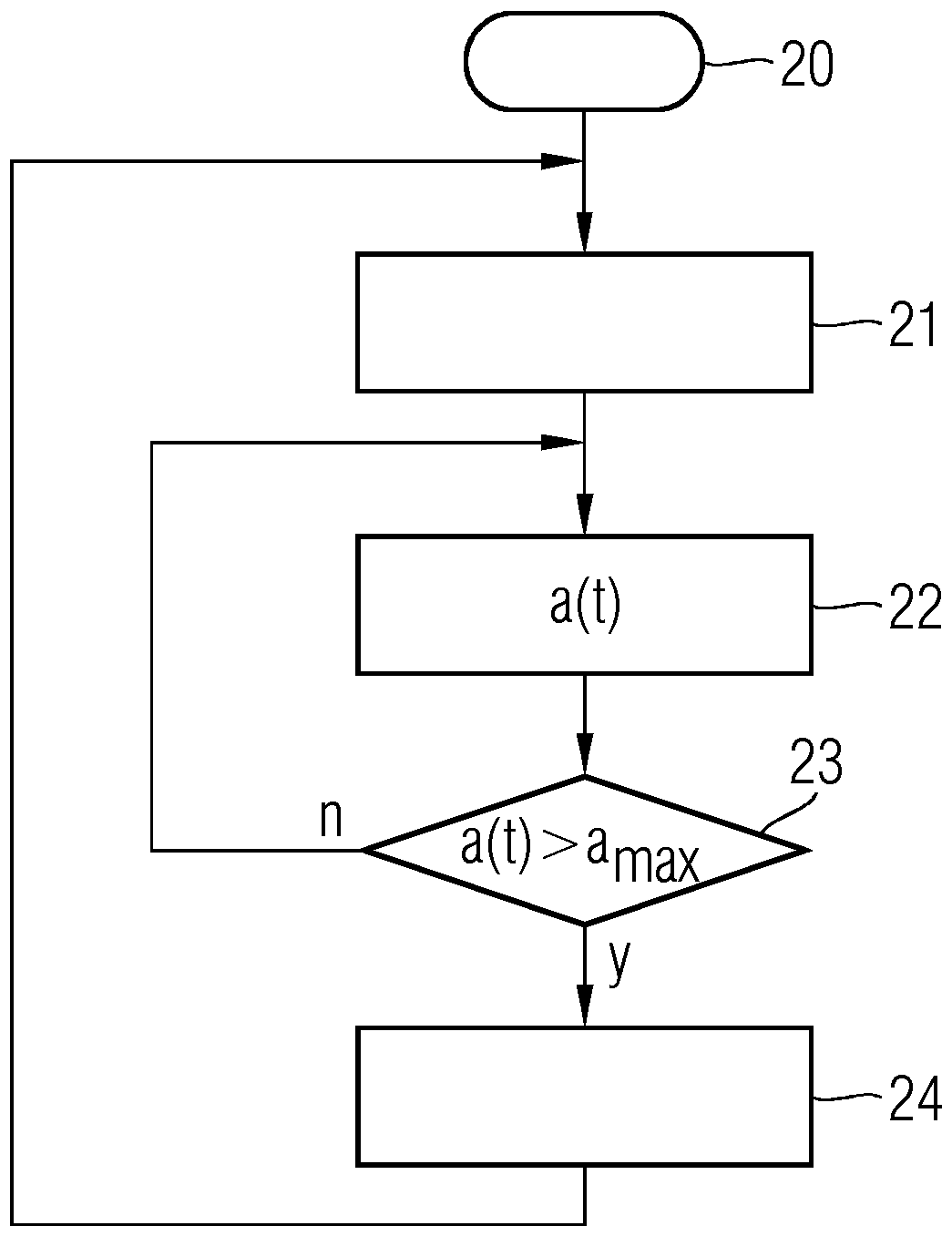
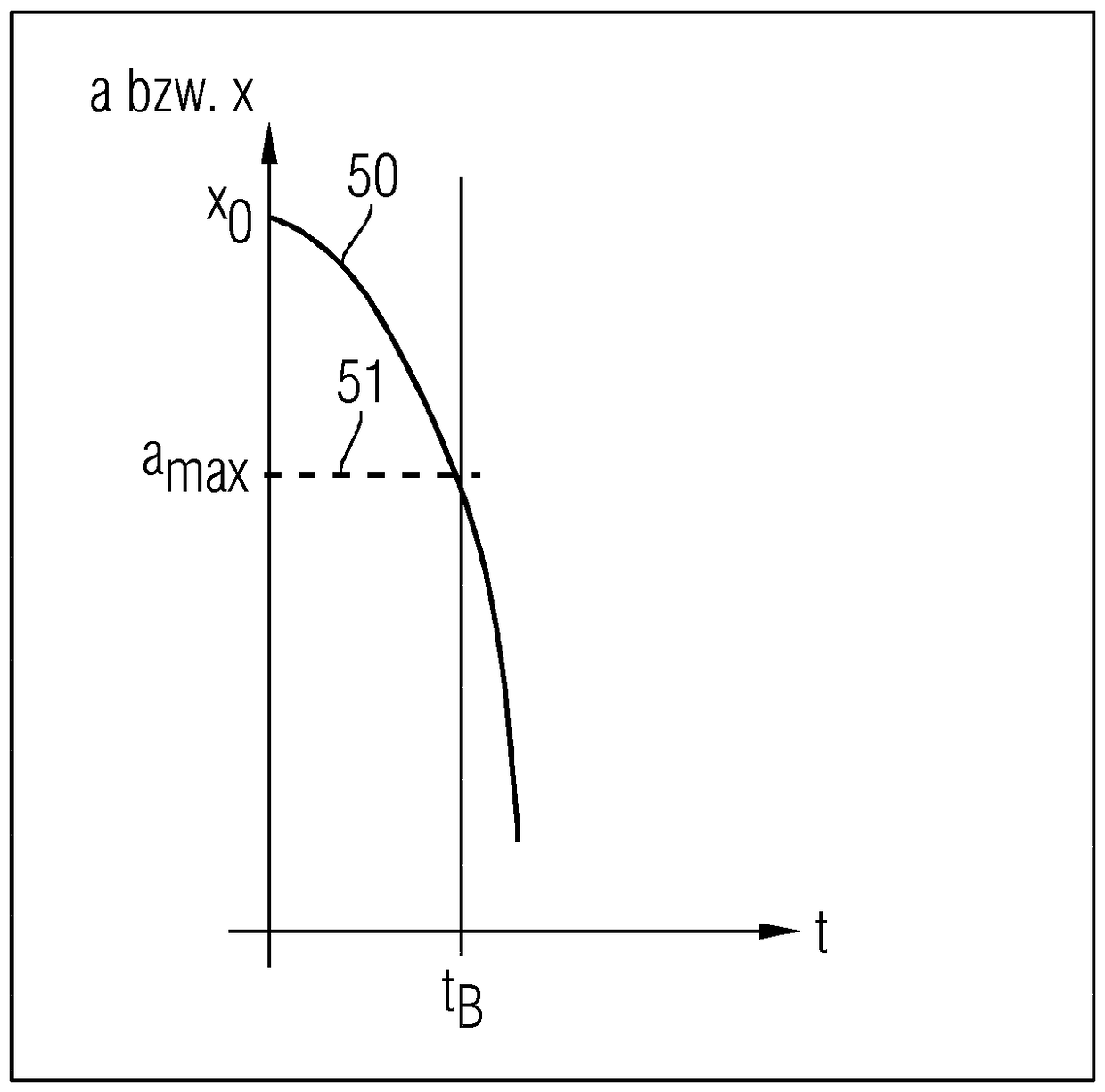
[0039] use as figure 1 The method according to the present invention as described in [0019] ensures that security-related information is deleted in a timely manner before the device becomes inoperable. In an initial state 10 of the method, security-related information is present in the device. For example, this information can be stored in a security module. In this case, at least one motion parameter of the device is determined continuously over time in method ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com