A Vulnerability Analysis Method for Network Operation and Maintenance
A technology for network operation and maintenance and analysis methods, which is applied in the field of network operation and maintenance vulnerability measurement and analysis, and can solve the problems of different vulnerability measurement and analysis methods and different objects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
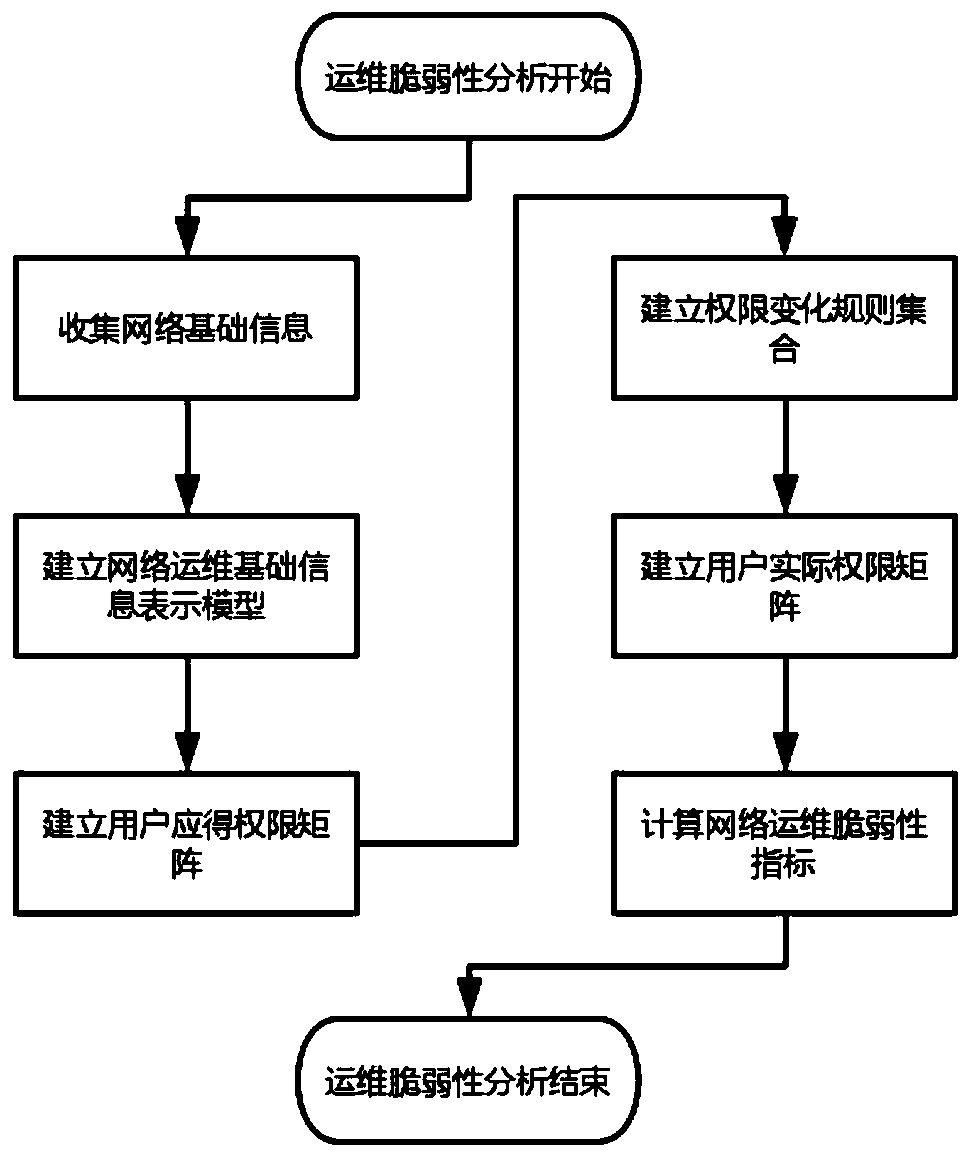
[0065] The present invention proposes a network operation and maintenance vulnerability analysis method, which uses network planning and design and multi-domain configuration as the basic analysis object, and uses the difference between the user's actual authority and the user's due authority as an index to construct the corresponding vulnerability Analytical methods can effectively discover the impact of improper network operation, maintenance and management on network security.
[0066] The network operation and maintenance vulnerability analysis method proposed by the present invention, its main steps are as follows figure 1 As shown, it mainly includes the steps of collecting basic network information, establishing a basic information representation model for network operation and maintenance, establishing a matrix of user permissions, establishing a set of permission change rules, establishing a matrix of actual user permissions, and calculating vulnerability indicators fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com