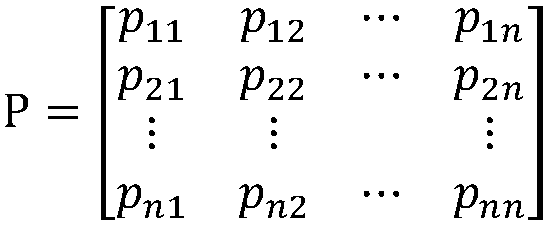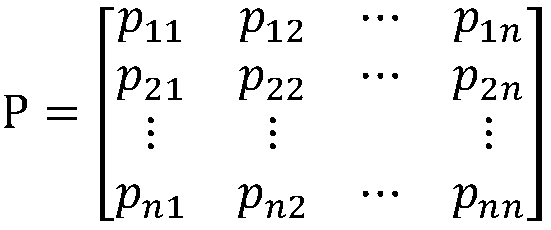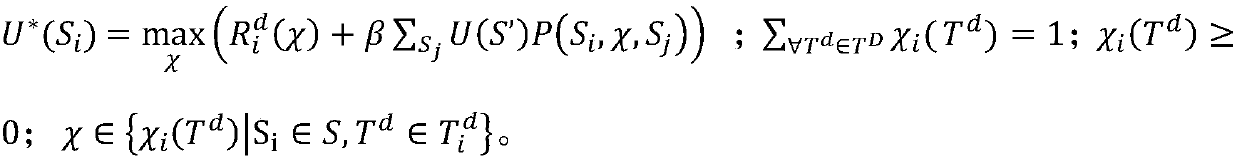Method for establishing attack and defense random game model facing malicious code defense
A game model, malicious code technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with examples.
[0023] The present invention is a method for establishing an attack-defense random game model oriented to malicious code defense, comprising:
[0024] 1. Establish a Markov offensive and defensive random game model, including:
[0025] Definition 1 ADSG-M game model, specifically: ADSG-M={N, S, A d ,A a ,P,R d , R a ,U}, the meanings of each element are as follows:
[0026] N={attacker, defender} is the set of participants in the attack-defense game. This embodiment only considers the situation of N=2, that is, the attacker and the defender. If there are multiple malicious softwares attacking at the same time, these softwares are merged as a single attacker, and the attack behavior is regarded as a distributed coordinated attack;
[0027] S={S ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com