A face recognition verification system and its association method with a target system
A target system and face recognition technology, which is applied in the field of image recognition and multi-system correlation fusion, can solve the problems of high rate of false results of face recognition, unreasonable point setting, hidden dangers of system security, etc., to improve the security of login verification performance, improve risk management and control capabilities, and save development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
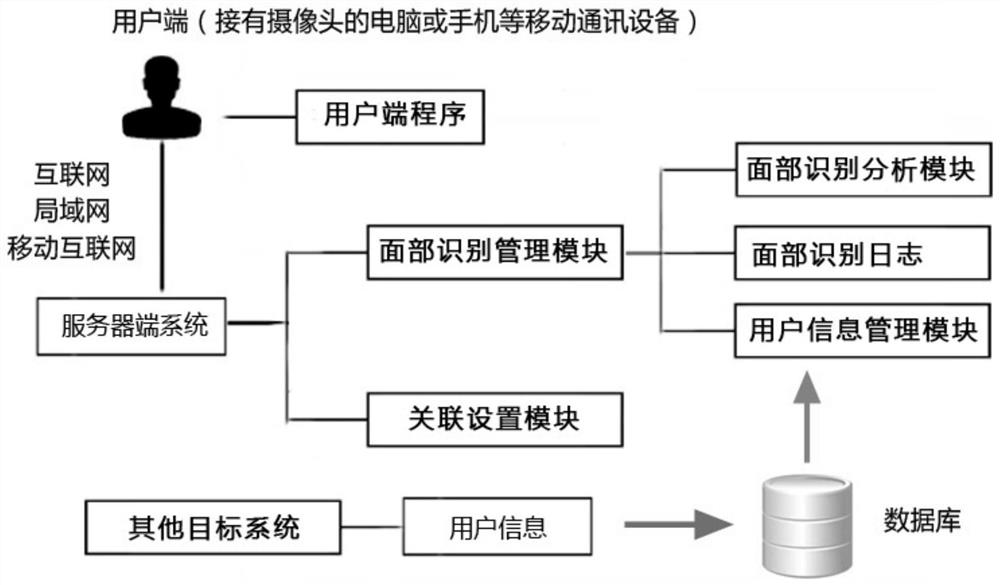
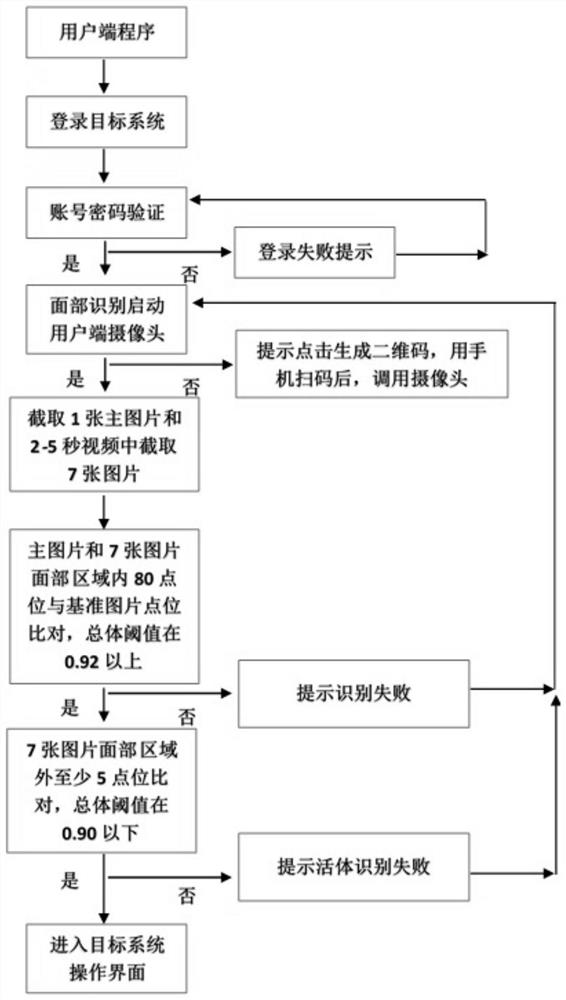
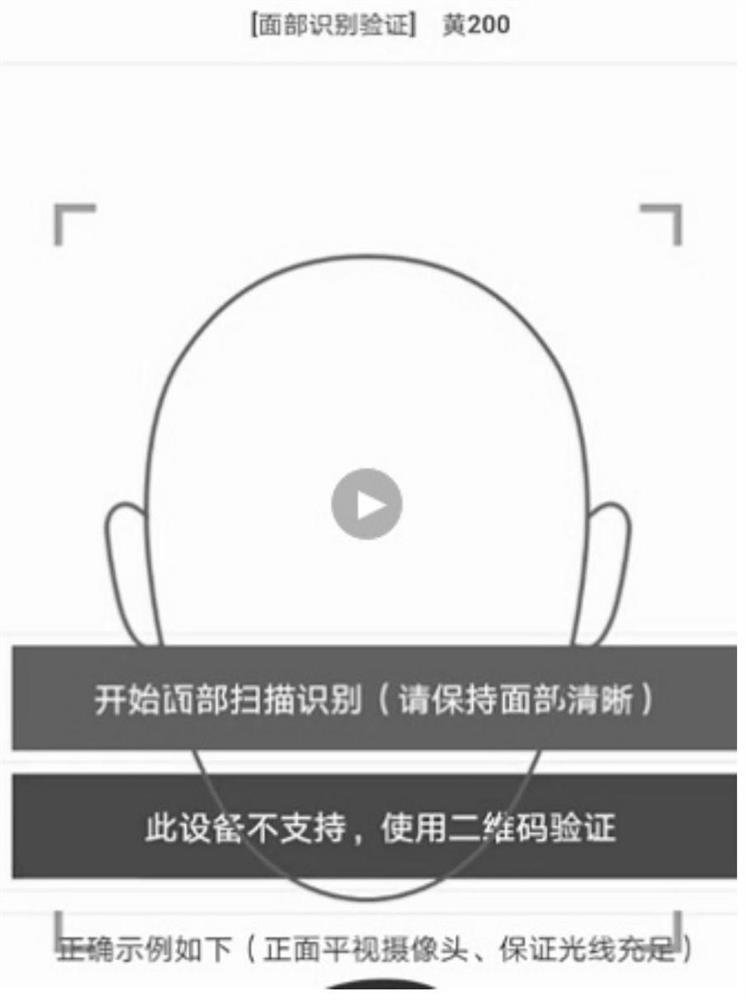
[0041] Such as figure 1 Shown is the structural diagram of the face recognition verification system of the present invention.
[0042] The face recognition verification system includes a client program and a server system.
[0043] The server-side system includes a facial recognition management module and an association setting module, wherein the facial recognition management module includes a facial recognition analysis module, a facial recognition log, and a user information management module.
[0044] The server-side system and other target systems are installed on the same server. It is a system program based on the database structure. Through the user information management module of the server-side system, the open database technology (ODBC) is used to synchronize with the user information data of other target systems. , set the login...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com