A Dynamic Password Control Method Applicable to Excavators
A control method and dynamic password technology, applied in the usage of multiple keys/algorithms, transmission systems, electrical components, etc., can solve the problems of complex control systems of excavators, and achieve the effect of improving security and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
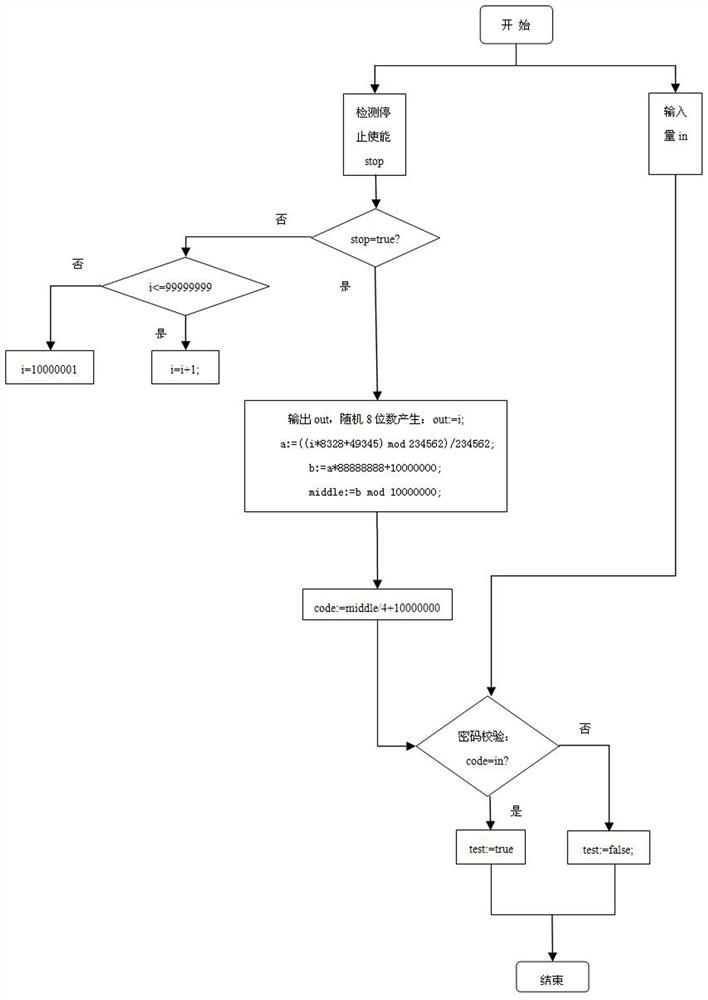
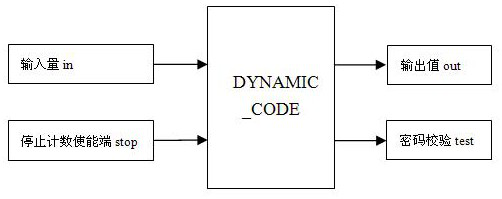
[0023] By the following figure 1 Attach figure 2 This invention is described in detail. figure 1 For the flow chart of the invention, attached figure 2 Indicates the input and output port description of the dynamic cryptographic library.
[0024] When the control system generates a related modification instruction, output the OUT to the corresponding device, the device is the same algorithm operation, producing another 8-bit number password code, passing IN with CODE, password verification, verify the pass, otherwise Unable to modify excavator parameters.
[0025] The library file has been counting inside without receiving the stop instruction, where the input variable is received after receiving the modification instruction, and the input value in; the output variable is: Verify output TEST, output 8 digits OUT; The intermediate variables used are: circulating cycle computing variables I, intermediate calculation variables A, B, Middle, password Code.
[0026] details as follows:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com