Authority management method, authority management device, mobile terminal and storage medium
A technology of authority management and mobile terminal, which is applied in the direction of telephone communication, electrical components, branch office equipment, etc., can solve the problems of unfavorable operation experience, mobile terminal security, etc., and achieve the effect of avoiding the direct use of equipment management authority and improving system performance and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0024] see figure 1 , figure 1 A schematic flowchart of the rights management method provided in the first embodiment of the present application is shown. The rights management method is used to prevent malicious programs from directly using device management rights by adding prompt information, and improve system performance and stability. In a specific embodiment, the rights management method is applied as Figure 7 The rights management device 200 shown and the mobile terminal configured with the rights management device 200 ( Figure 9 ). The following will take the mobile terminal as an example to illustrate the specific process of this embodiment. Of course, it can be understood that the mobile terminal used in this embodiment can be a smart phone, a tablet computer, a wearable electronic device, etc., and no specific details will be given here. limited. The following will target figure 1 The flow shown is described in detail, and the rights management method may s...
no. 2 example
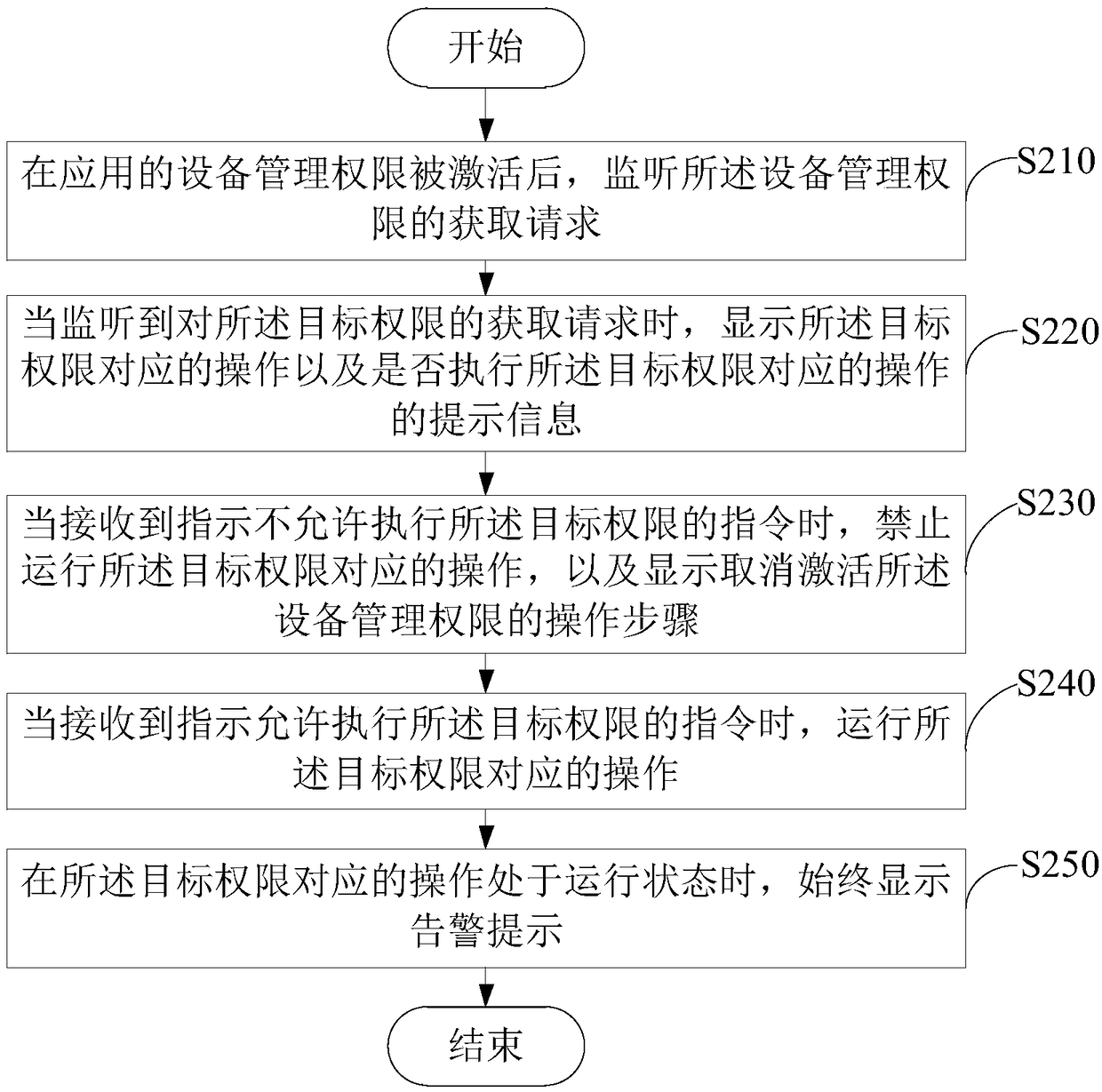
[0036] see image 3 , image 3 A schematic flowchart of the rights management method provided by the second embodiment of the present application is shown. The following will target image 3 The flow shown is described in detail, and the method may specifically include the following steps:
[0037] Step S210: After the device management permission of the application is activated, monitor the acquisition request of the device management permission;
[0038] Step S220: When an acquisition request for the target authority is detected, display an operation corresponding to the target authority and a prompt message indicating whether to execute the operation corresponding to the target authority.
[0039] see Figure 4 , in this embodiment, when listening to the acquisition request for the target authority, the mobile terminal displays the operation corresponding to the target authority in addition to displaying whether the operation corresponding to the target authority is all...
no. 3 example
[0049] see Figure 5 , Figure 5 A schematic flowchart of the rights management method provided by the third embodiment of the present application is shown. The following will target Figure 5 The shown process is described, and the shown method may specifically include the following steps:
[0050] Step S310: After the device management permission of the application is activated, monitor the acquisition request of the device management permission.
[0051] Step S320: When an acquisition request for the target authority is detected, display a prompt message indicating whether the operation corresponding to the target authority is allowed to be performed, and display selection information for reminding each time or not reminding again.
[0052] see Figure 6 , in this embodiment, when listening to the acquisition request of the target authority, in addition to displaying the prompt information of whether to allow the operation corresponding to the target authority, the mobi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com