Operator data-based public security case time-space analysis method and apparatus
A spatiotemporal analysis, operator technology, applied in data processing applications, electrical digital data processing, special data processing applications, etc., can solve problems such as coverage blind spots, achieve small blind spots, wide coverage, and improve the efficiency and quality of case solving. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0051] In a specific embodiment, the time-space analysis method for public security cases based on operator data further includes the steps,
[0052] S40: Verify the similarity between the suspect's action trajectory and the case's action trajectory, and if the similarity meets a certain threshold, list him as the final suspect and obtain a final list of suspects.
[0053] In this embodiment, the location information of the suspect at the time of the crime will be obtained based on the operator data, and the location information will be used to generate an action trajectory, which will then be compared with the case action trajectory. If the two trajectories have a high degree of similarity, their Listed as the final suspect, the similarity threshold here is 90% similarity.
Embodiment 2
[0055] In a specific embodiment, the step S30 specifically includes,
[0056] S31: Screen out the operator customers who appear within the error range of the crime location within the error range of the time of the crime;
[0057] S32: Screen out the operator customers who match the action track of the case within the time error range of the case, and obtain a list of suspects.
[0058] In this embodiment, the crime location is a fixed location value, including longitude and latitude information. The error range of the crime location is to make up for the error of the positioning accuracy of the base station, and the error range of the crime time is to make up for the difference between the time of the crime and the time of committing the crime. error.
Embodiment 3
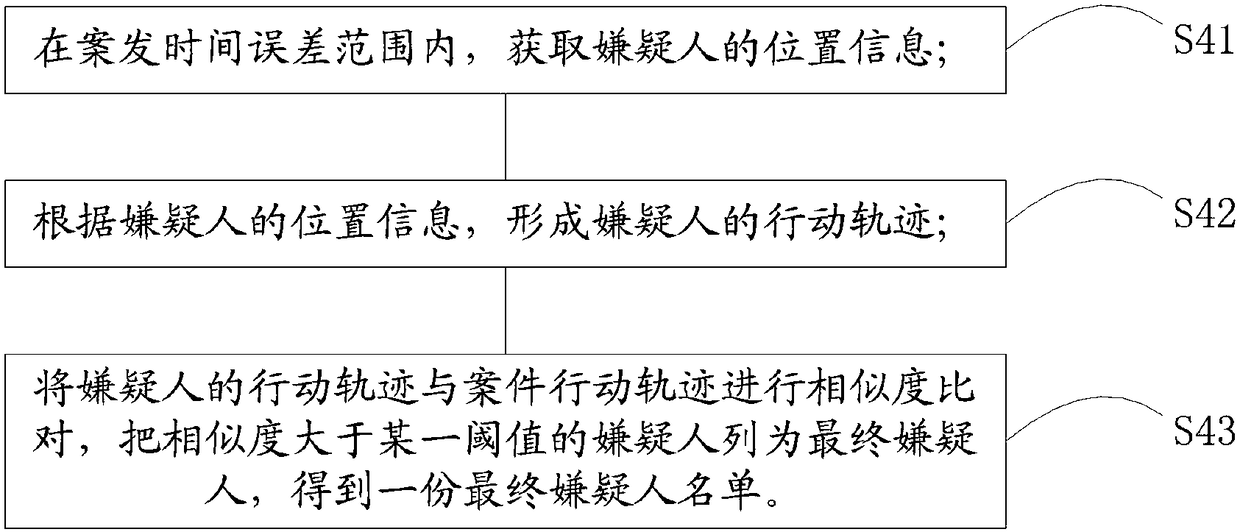
[0060] see figure 2 , in a specific embodiment, the step S40 specifically includes,
[0061] S41: Obtain the location information of the suspect within the error range of the incident time;
[0062] S42: Form the suspect's action track according to the suspect's location information;
[0063] S43: Compare the similarity between the action trajectory of the suspect and the action trajectory of the case, list the suspects whose similarity is greater than a certain threshold as the final suspects, and obtain a list of final suspects.
[0064] In this embodiment, the latitude and longitude information of the suspect is obtained, and the latitude and longitude information is connected on the map according to the time sequence of the crime, and the action trajectory of the suspect is sequentially connected, and the action trajectory of the suspect is compared with the action trajectory of the case, which is satisfied. Suspects with similarity requirements are listed as final susp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com