Visitor mode opening method, terminal and computer readable storage medium
A visitor mode and visitor technology, applied in computer components, computer security devices, computing, etc., can solve problems such as user information leakage, information leakage, and reduced terminal security, and achieve the effect of overcoming information leakage and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
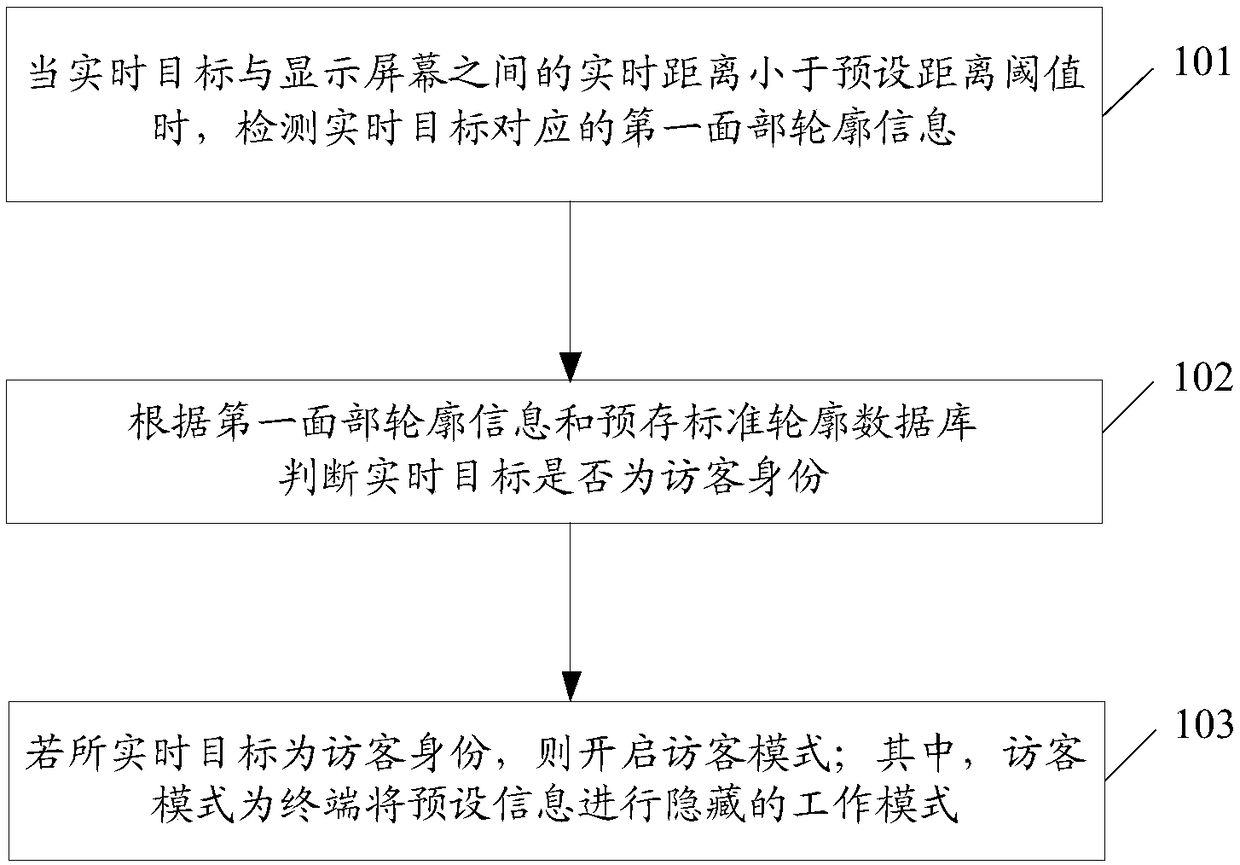
[0073] image 3 Schematic diagram of the implementation process of the method for enabling the visitor mode proposed by the embodiment of the present invention Figure 1 ,Such as image 3 As shown, in an embodiment of the present invention, the method for a terminal to enable a guest mode may include the following steps:
[0074] Step 101. When the real-time distance between the real-time target and the display screen is smaller than a preset distance threshold, detect first facial contour information corresponding to the real-time target.
[0075] In an embodiment of the present invention, if the real-time distance between the real-time target and the display screen is smaller than a preset distance threshold, the terminal may detect and obtain the first facial contour information corresponding to the real-time target.
[0076] It should be noted that, in the embodiment of the present invention, the aforementioned terminal may be a terminal configured with a display screen,...
Embodiment 2
[0104]Based on the first embodiment above, Figure 7 Schematic diagram of the implementation process of the method for enabling the visitor mode proposed by the embodiment of the present invention Figure four ,Such as Figure 7 As shown, in an embodiment of the present invention, the method for determining whether the real-time target is a visitor identity according to the first facial profile information and the pre-stored standard profile database of the terminal may include the following steps:
[0105] Step 102a, read the standard profile information in the pre-stored standard profile database.
[0106] In an embodiment of the present invention, if the real-time distance is less than the preset distance threshold, after the terminal detects the first facial contour information corresponding to the real-time target, the terminal may first read the standard facial contour information in the pre-stored standard contour database. profile information.
[0107] It should be ...
Embodiment 3
[0120] Figure 9 Schematic diagram of the implementation process of the method for enabling the visitor mode proposed by the embodiment of the present invention Figure five ,Such as Figure 9 As shown, in the embodiment of the present invention, when the real-time distance between the real-time target and the display screen is less than the preset distance threshold, before detecting the first facial contour information corresponding to the real-time target, that is, before step 101, the above-mentioned terminal turns on the visitor The mode method may also include the following steps:
[0121] Step 106, detecting second facial contour information in the preset image.
[0122] In an embodiment of the present invention, the above-mentioned terminal may first detect the second facial contour information in the preset image.
[0123] It should be noted that, in the embodiment of the present invention, the aforementioned preset image may be an image stored in the aforementione...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com