Method for transmitting keys, receiving terminal and distribution terminal
A technology for receiving terminals and transmitting keys, which is applied in the field of data processing, can solve problems such as increasing the operation and maintenance cost of POS equipment, a large amount of manpower, and slowing down the speed of business expansion, so as to improve convenience and security, reduce labor costs, and meet safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0128] This embodiment provides a method for transmitting a key, including:
[0129] S1. The receiving terminal obtains the first public key certificate from the authentication terminal; the distribution terminal obtains the second public key certificate from the authentication terminal; the authentication terminal is used to confirm the legitimacy of the terminal and issue a digital certificate.
[0130]Optionally, the receiving terminal is a POS machine.
[0131] Wherein, since this embodiment involves certificates, implementing this solution requires deploying a certification terminal (Certification Authority certification center) to build an effective PKI system. In this embodiment, the manufacturer establishes its own authentication terminal, and its main task is to perform identity authentication on the receiving terminal and the distribution terminal and issue digital certificates.
[0132] Optionally, the process for the receiving terminal to obtain the first public k...
Embodiment 2
[0184] This embodiment provides a receiving terminal, including one or more first processors 1 and a first memory 2, the first memory 2 stores a program, and is configured to be controlled by the one or more first processors 1Perform the following steps:
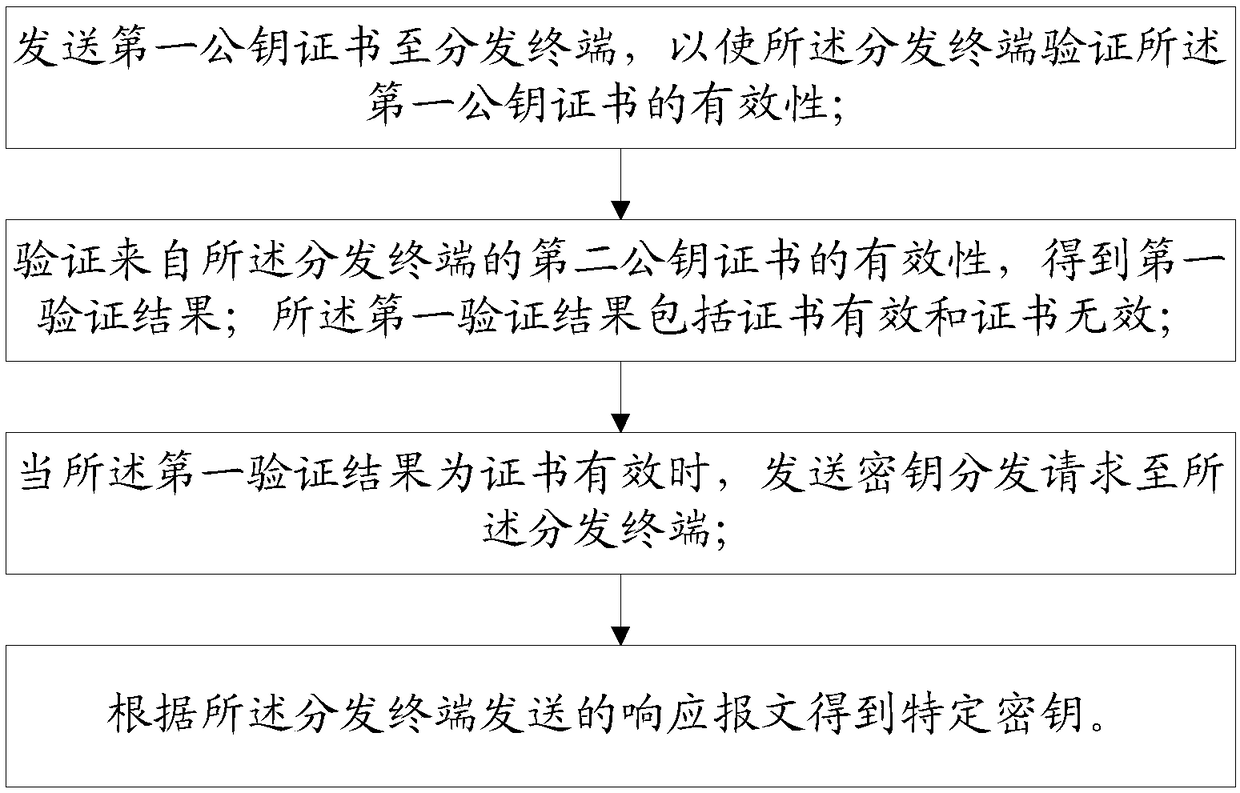
[0185] S1. Obtain a first public key certificate from an authentication terminal; the authentication terminal is used to confirm the legitimacy of the terminal and issue a digital certificate.
[0186] S2. Send the first public key certificate to the distribution terminal, so that the distribution terminal verifies the validity of the first public key certificate.
[0187] S3. Verify the validity of the second public key certificate from the distribution terminal to obtain a first verification result; the first verification result includes a valid certificate and an invalid certificate. Specifically:
[0188] Obtain the verification public key from the authentication terminal;
[0189] Verifying the validity of the second...
Embodiment 3
[0202] This embodiment provides a distribution terminal, including one or more second processors 3 and a second memory 4, the second memory 4 stores a program, and is configured to be controlled by the one or more second processors 3 Perform the following steps:
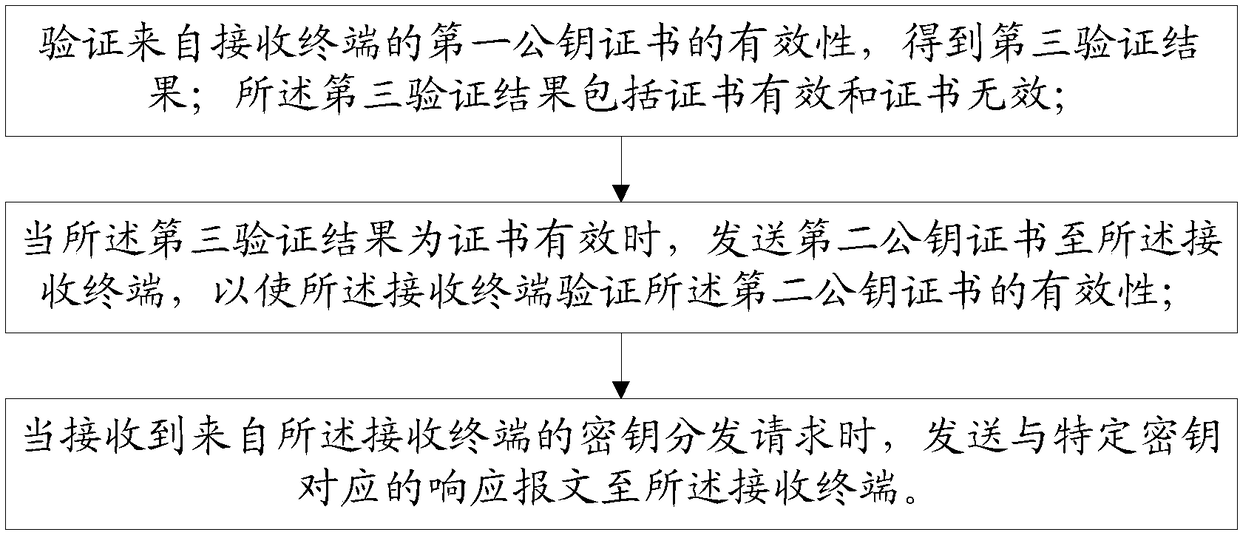
[0203] S1. Obtain a second public key certificate from an authentication terminal; the authentication terminal is used to confirm the legitimacy of the terminal and issue a digital certificate.
[0204] S2. Verify the validity of the first public key certificate from the receiving terminal, and obtain a third verification result; the third verification result includes valid certificate and invalid certificate; specifically:
[0205] Obtain the verification public key from the authentication terminal;
[0206] Verifying the validity of the first public key certificate according to the verification public key to obtain a third verification result.
[0207] S3. When the third verification result is that the certificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com