Security authentication method and authentication system for mutual authentication of terminal and camera equipment
A technology of camera equipment and security authentication, applied in the field of communication, to achieve the effect of reducing the number of communications, communication security, and increasing authentication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
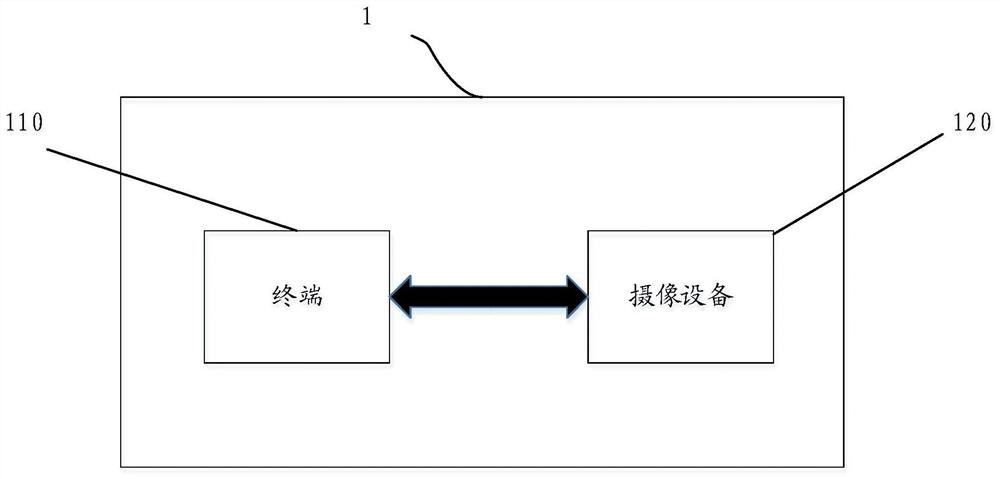
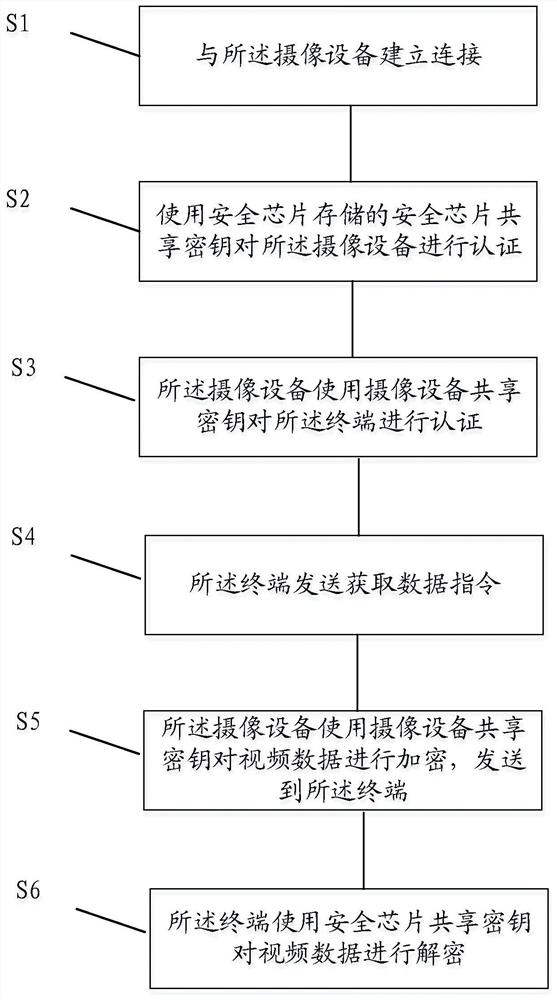
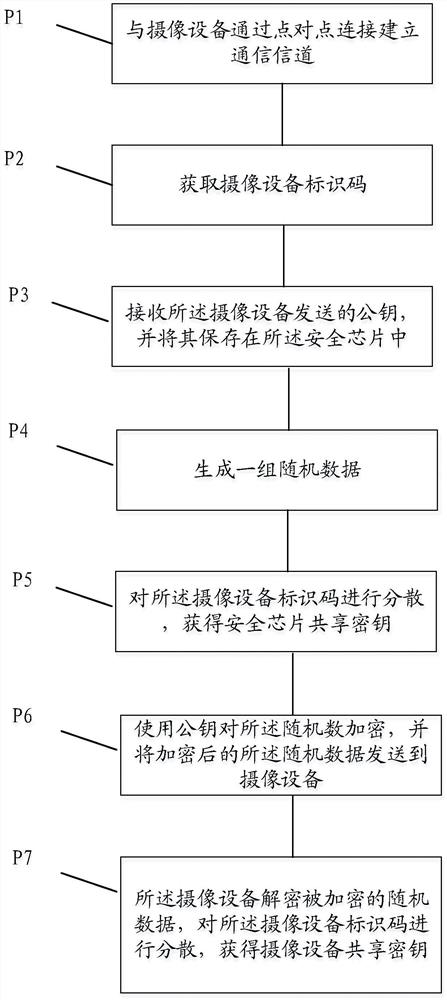
[0115] The above combined Figure 1-3 The security authentication system and security authentication method are introduced, and the following is combined with the attached Figure 4 with 5 The terminal 110 and camera equipment 120 in the security authentication system are introduced. Among them such as Figure 4 As shown, the terminal 110 includes the following components:
[0116] The security chip 410 generates and stores the security chip shared key;
[0117] The communication device 420 establishes a communication connection with the imaging device, sends an instruction to acquire data to the imaging device, and receives encrypted video data sent by the imaging device;
[0118] The security authentication device 430 uses the security chip shared key stored in the security chip to authenticate the imaging device, generates a command to acquire data after the authentication is passed, and uses the security chip shared key to decrypt the encrypted video data. The aforeme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com