PDF signature method and system supporting SM3 password hash algorithm and SM2 digital signature algorithm
A technology of digital signature and hash algorithm, which is applied in the direction of digital transmission system, transmission system, digital data protection, etc., can solve the problem of unrecognizable SM2 algorithm, etc., and achieve the effect of strong security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
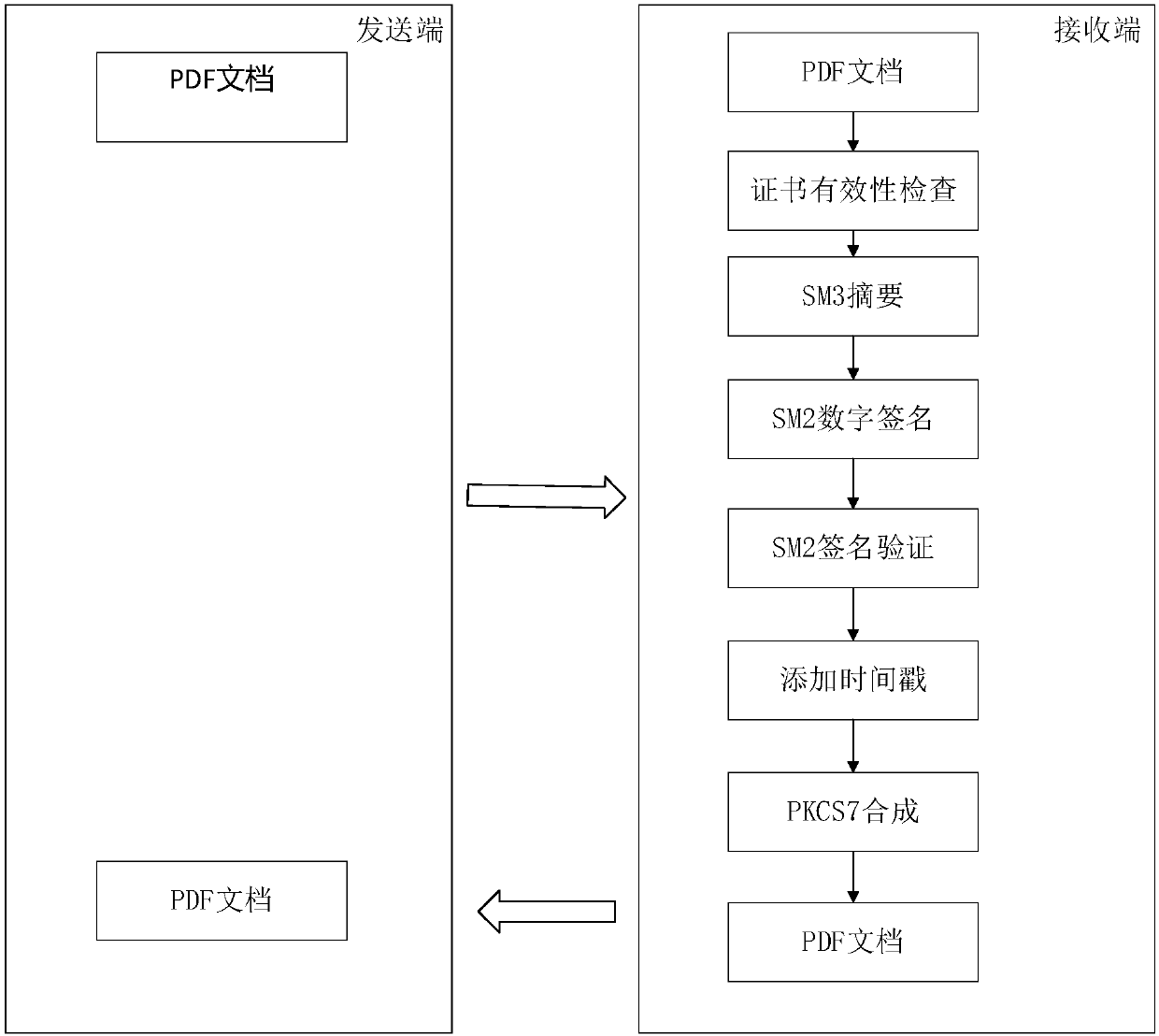
[0066] This example supports the PDF signature method of SM2 such as figure 1 As shown, it includes the sending and receiving process at the sending end and the signing process at the receiving end.
[0067] The sending and receiving process of the sending end includes the following steps:
[0068] S1. The sender sends the PDF document to be signed.
[0069] S2. Receive the signed PDF document;
[0070] The signature process at the receiving end includes the following steps:
[0071] S1. The digital certificate of the signer exists at the receiving end, and the receiving end obtains the PDF document. The digital certificate includes a private key and a public key certificate. The public key certificate contains information such as the public key of the identity owner, the name, the name of the issuing authority, the digital ID number, and the digital signature of the issuing authority. Digital identity can be issued by a trusted digital certificate certification center. Call SSQ-GM t...
Embodiment 2
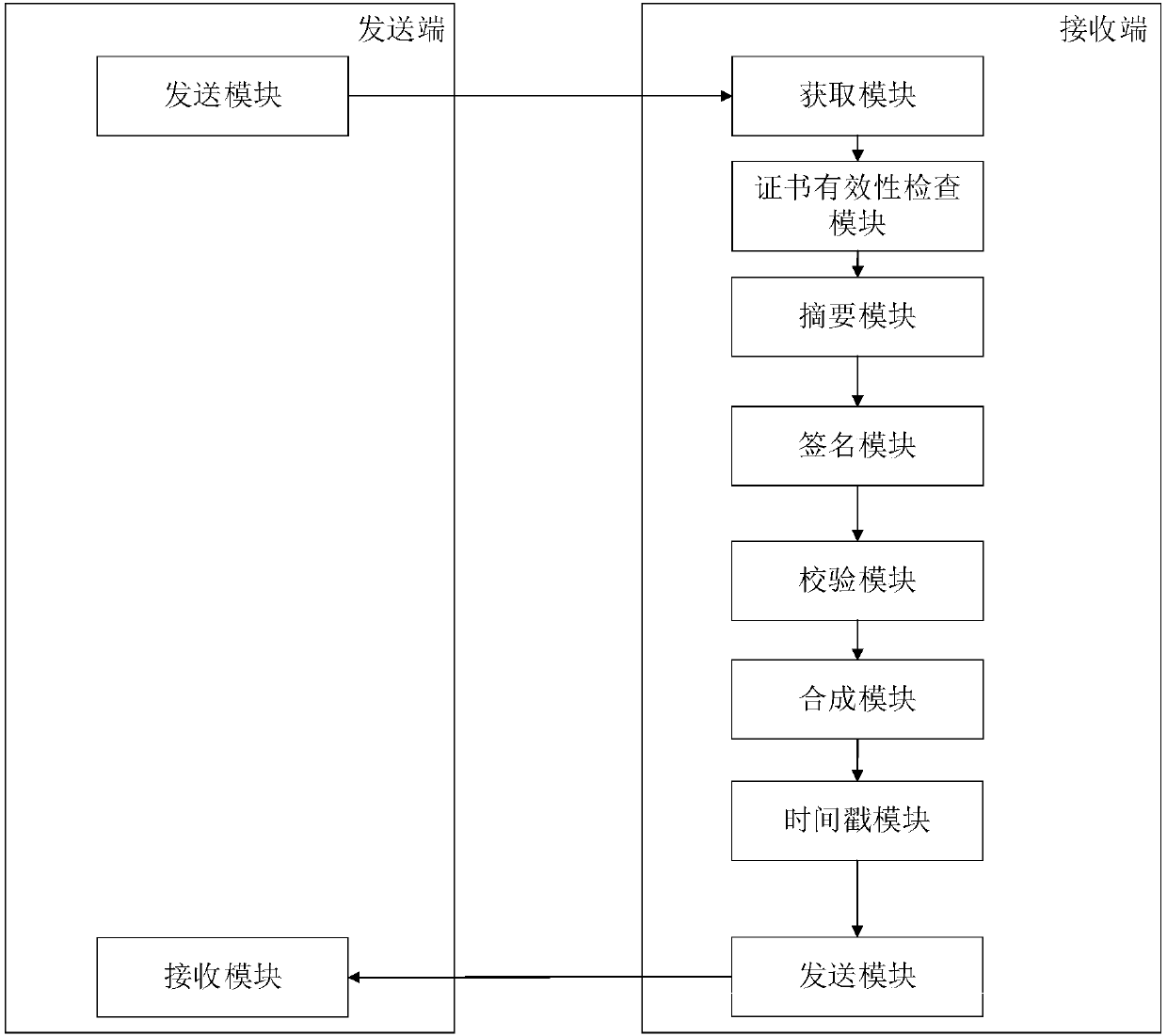
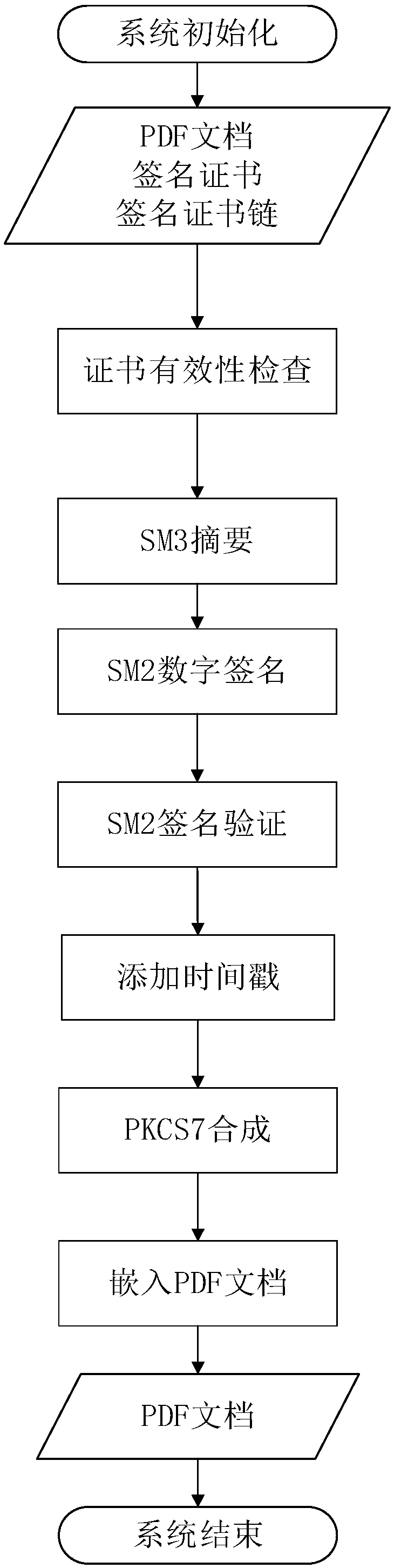
[0080] Such as figure 2 As shown, this embodiment provides a PDF signature system supporting SM3 cryptographic hash algorithm and SM2 digital signature algorithm, and the system includes a sending end and a receiving end. The overall process is as image 3 As shown, the sender sends a PDF document, and the signature certificate and signature certificate chain are signed by the receiver and embedded in the PDF and then sent back to the sender.
[0081] The sending end includes a sending module and a receiving module, and the specific functions of each module are as follows:
[0082] The sending module is used to send the PDF document to be signed.
[0083] The receiving module is used to obtain the PDF document signed by the receiving end.
[0084] The receiving end includes an acquisition module, a summary module, a signature module, a verification module, a synthesis module, a time stamp module, and a sending module. The specific functions of each module are as follows:
[0085] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com