A method and device for identifying identity characteristics of email senders
An e-mail sending and identity feature technology, applied in the field of e-mail system, can solve the problem of not being able to confirm the identity of the sender of the e-mail
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
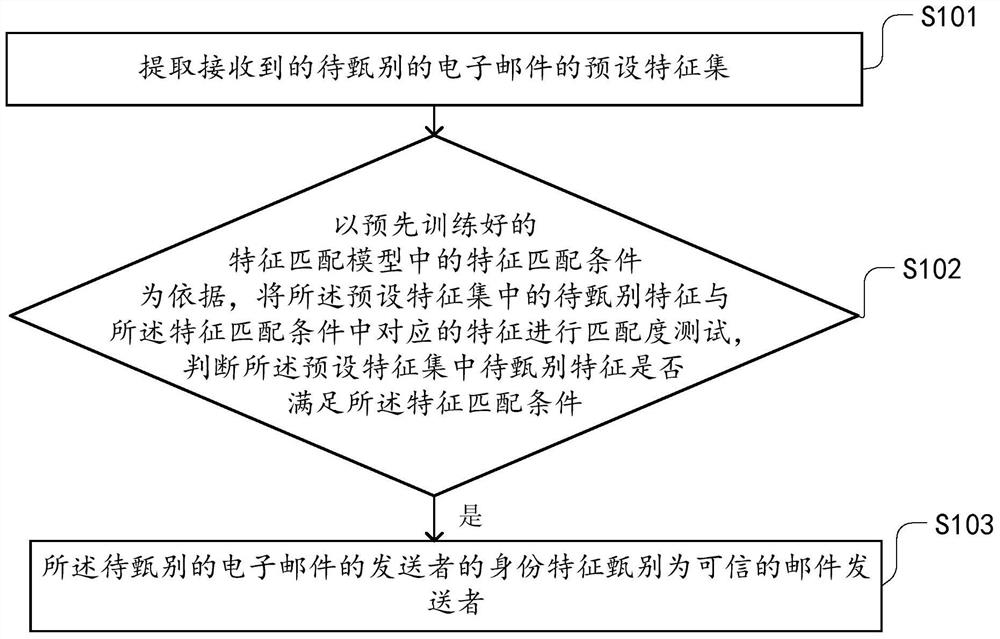
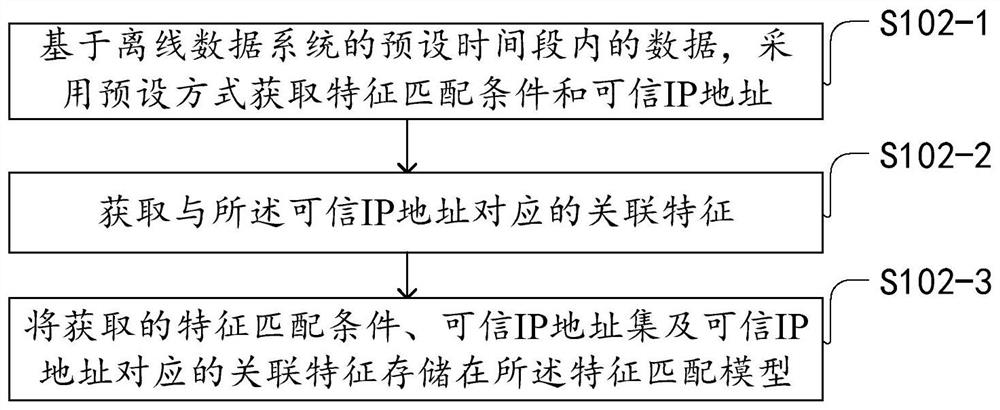
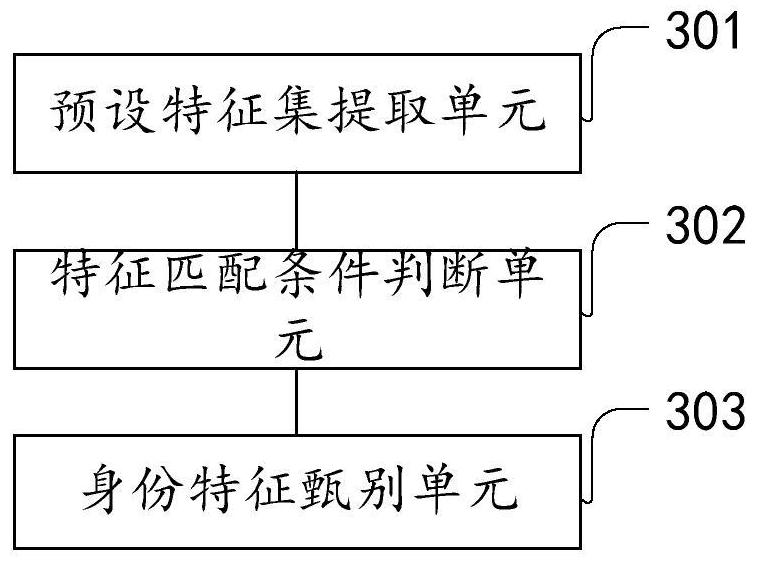
[0189] The first embodiment of the present application provides a method for identifying the identity of an e-mail sender. The method is used to identify whether the e-mail sender has a real identity. When an e-mail is transmitted between two different e-mail systems , the recipient system needs to screen and verify the authenticity of the domain name identity of the sending address of the received mail to determine whether the received mail is indeed from the email system authorized by the domain name owner, or to determine whether the Whether the received email is sent from the email sending IP address authorized by the domain name owner, further this method can identify suspicious emails sent by forging or pretending to be someone else's domain name.
[0190] Among them, the e-mail system is a separate system, which has its own server. Multiple domains can be set up in the e-mail system, and multiple users can be set up in each domain. For example, if you buy a The commerci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com