Highly anonymous RFID authentication protocol based on Hash function and dynamic shared key
A dynamic sharing and public key technology, applied in key distribution, can solve the problems of unfavorable large-scale application of RFID systems, unsuitable encryption algorithms, low-cost label calculation and storage capacity limitations, etc., to reduce server load and speed up the authentication process , good Dos and desynchronization attack effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
[0051] It should be understood that terms such as "having", "comprising" and "including" as used herein do not entail the presence or addition of one or more other elements or combinations thereof.
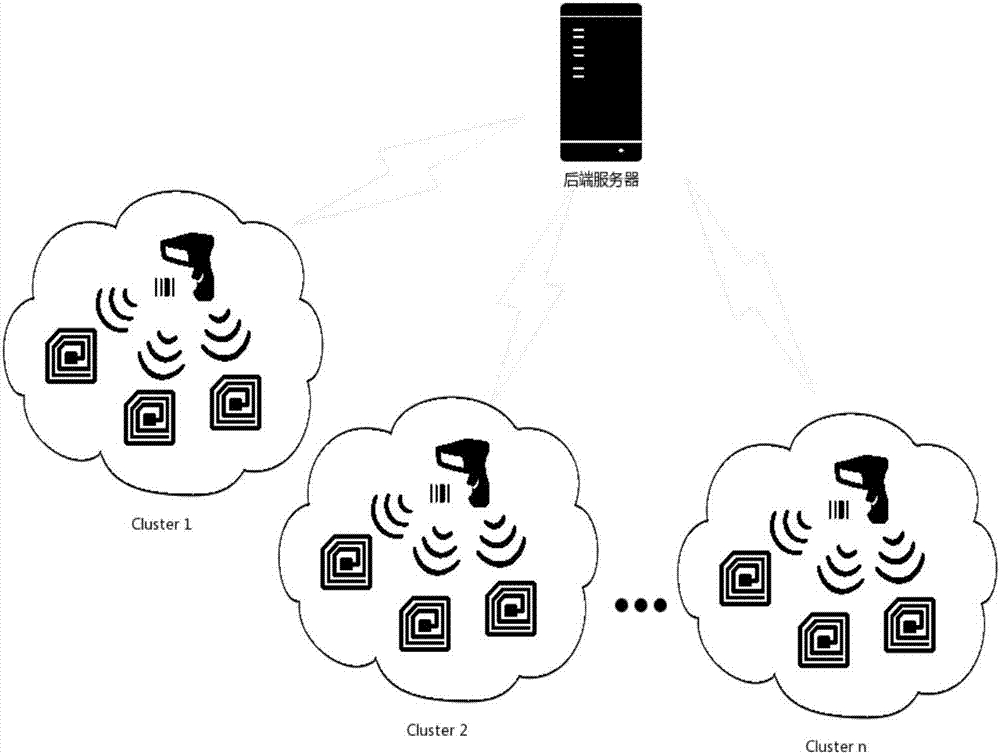
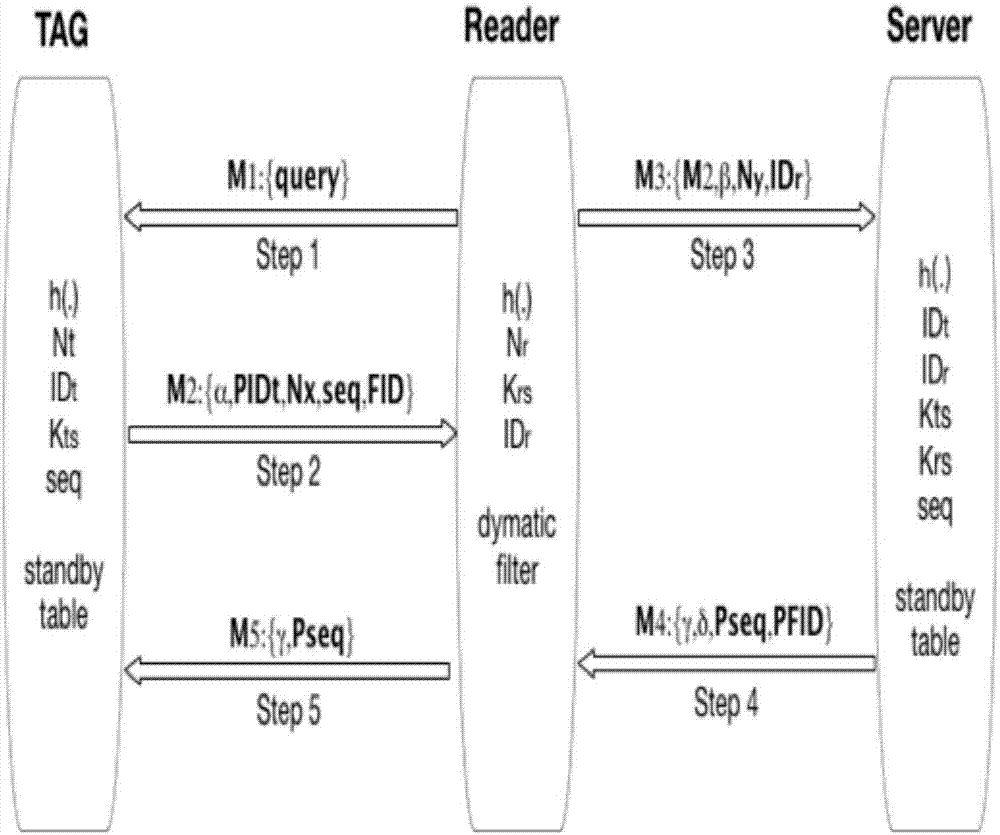
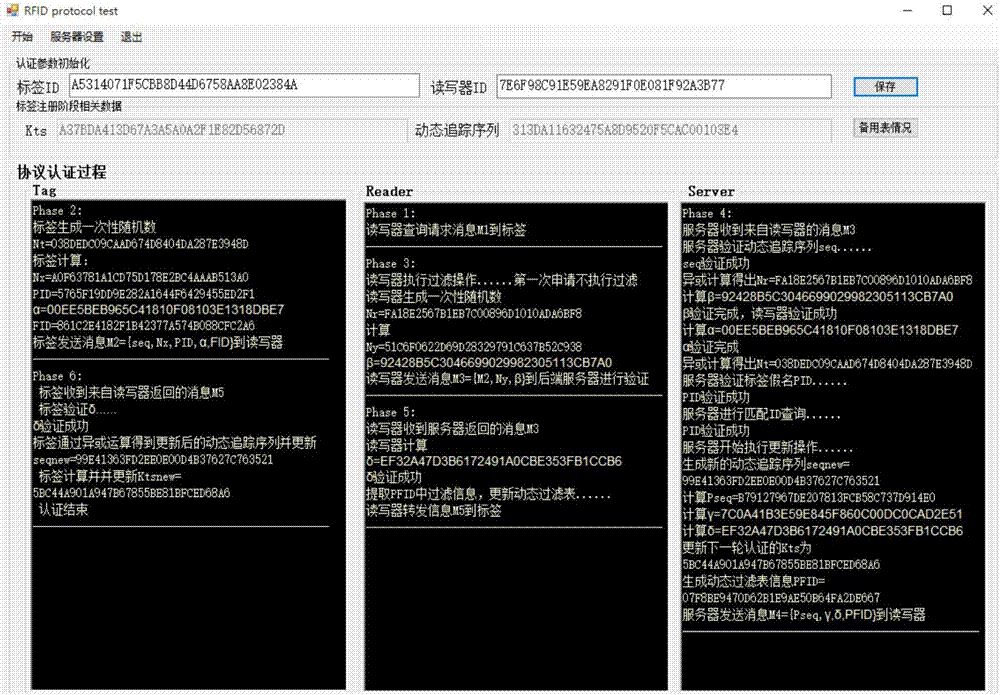
[0052] Based on Hash function and dynamic shared key to encrypt the authentication process, a lightweight RFID security authentication protocol that satisfies strong anonymity is proposed. The protocol session messages of this protocol are all encrypted with a one-way hash function combined with a dynamically updated shared key and a random number generator. Even if the message is intercepted, there will be no danger of exposing the original data. During the authentication process, the ID is transmitted in the form of a one-time pseudonym PID, and the reader cannot obtain or calc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com