Affine transformation subbytes box-based lightweight hash method
A technology of affine transformation and byte replacement, which is applied in the field of cryptographic hash functions, can solve the problems of increasing linear layer confusion, small hardware overhead, statistical saturation method attacks, etc., to achieve enhanced confusion, low hardware overhead, and improved resistance The effect of the ability to stat saturation attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
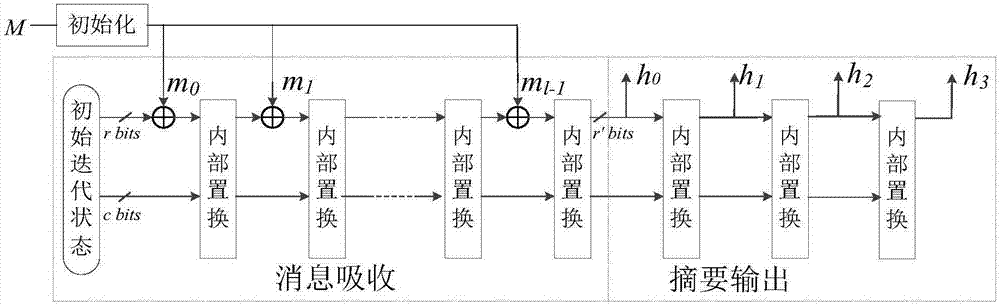
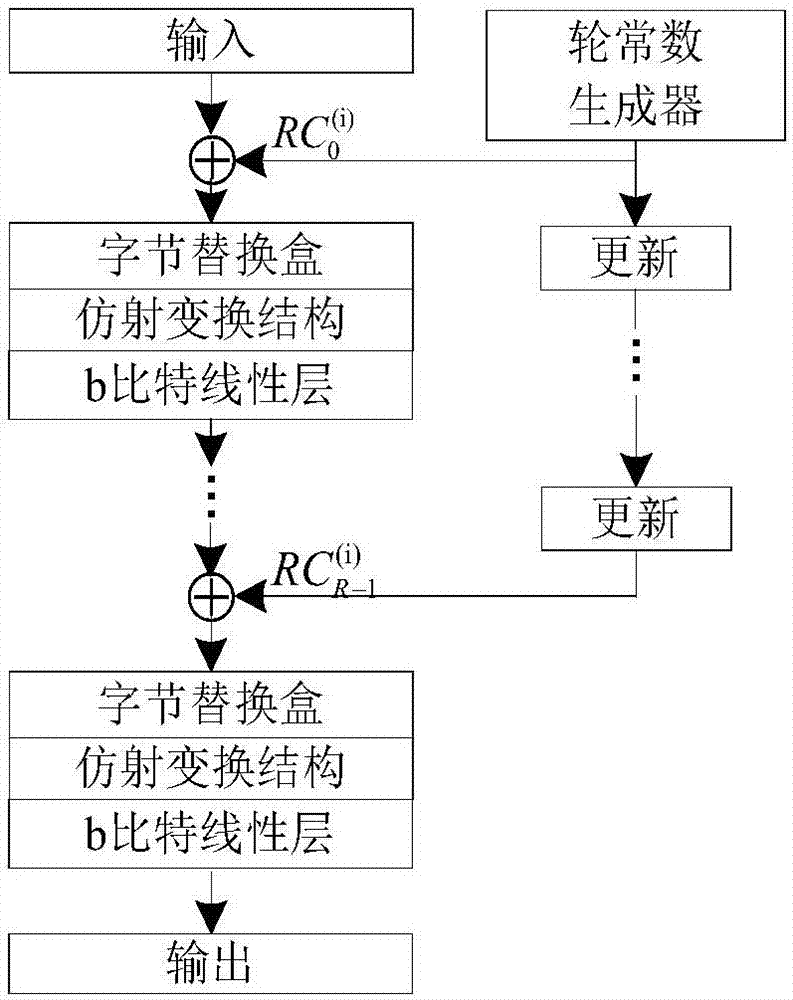
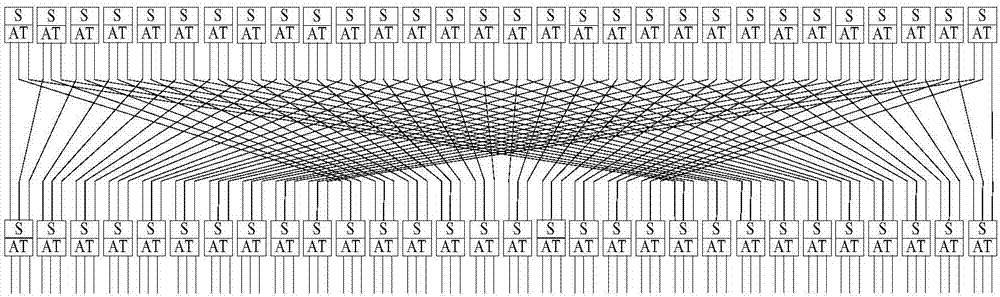
[0039] see figure 1 , is the basic logical structure of the light-weight hash method based on the affine transformation byte replacement box of the present invention. In the figure, the input message is denoted as M, and the initial iteration state is denoted as STATE 0 , the grouped message after message initialization is denoted as {m 0 ,m 1 ,..., m l-1}, the message output each time in the output summary stage is denoted as {h 0 ,h 1 ,h 2 ,h 3}, the output times of the three versions of this method are all 4 times. Among them, the length of the summary is n, the length of the internal iteration state is b, the length of the XOR of the internal permutation is not with the message, the length of the packet is r (b=r+c), and the length of the message output each time is r'(4r' =n). The present invention provides three versions of lightweight hash parameter combinations, the digest lengths n are 80 bits, 128 bits and 160 bits respectively, the internal iteration state l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com