A method and system for dynamically scheduling a network operating system
An operating system and dynamic scheduling technology, applied in the field of network security, can solve the problems of small security threats and inability to resist unknown threats, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
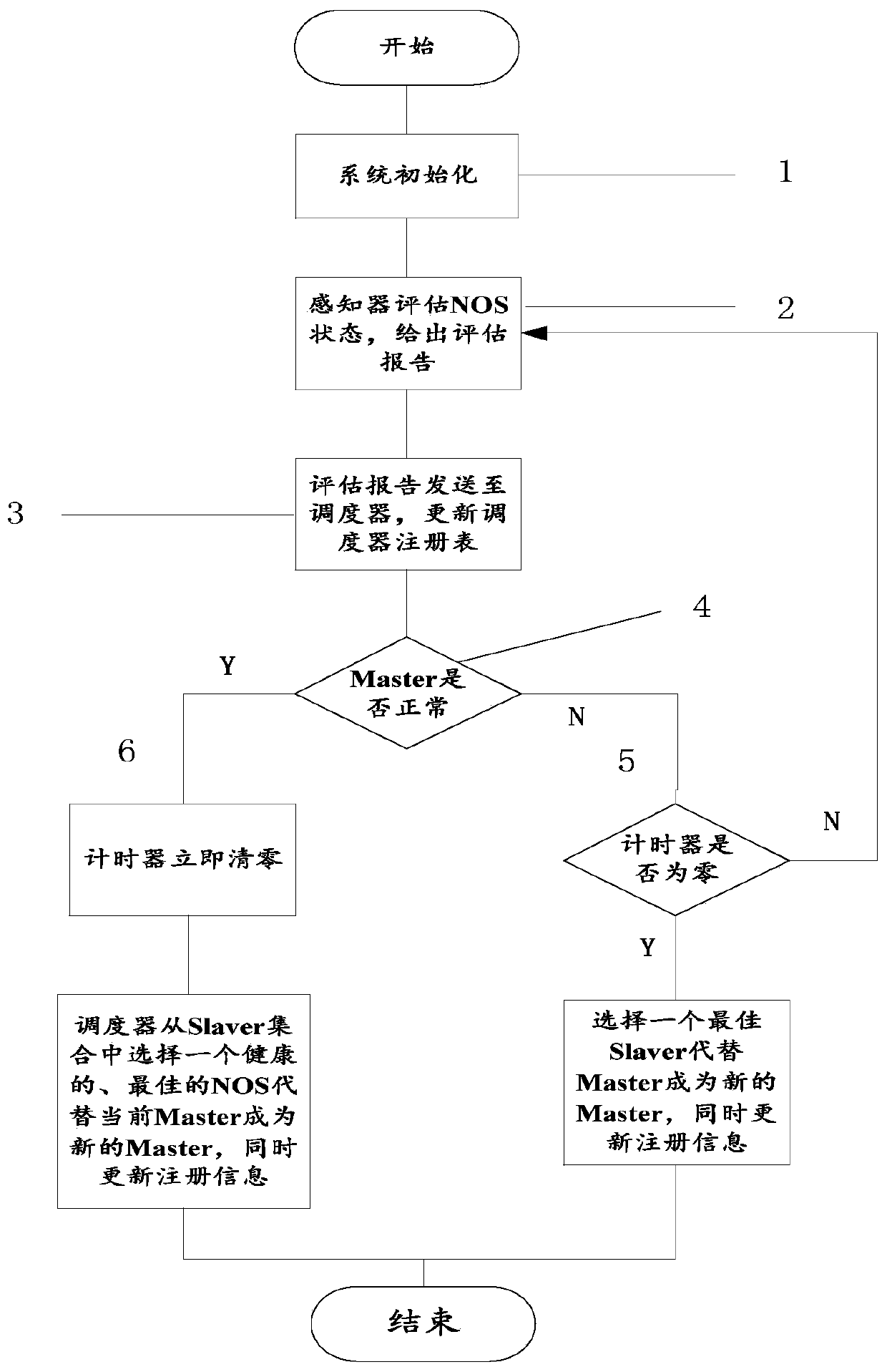
[0032] Embodiment one, such as figure 1 As shown, a method for dynamically scheduling network operating systems includes the following steps:
[0033] Step 1: System initialization;
[0034] Step 2: The perceptron is responsible for evaluating the working status of all NOS and giving an evaluation report;
[0035] Step 3: The sensor regularly sends the evaluation report to the scheduler to update the registration information;
[0036] Step 4: If the NOS evaluation result of the current Master role is normal, go to step 5, otherwise go to step 6;
[0037] Step 5: Determine whether the scheduling timer is zero. If it is zero, the scheduler will select the best Slaver to replace the Master as the new Master based on the scheduling strategy and the evaluation report, and update the registration information at the same time; if it is not zero, skip to step 2;
[0038] Step 6: If monitoring finds that the NOS of the Master role is abnormal, stop the scheduler timing and clear i...
Embodiment 2
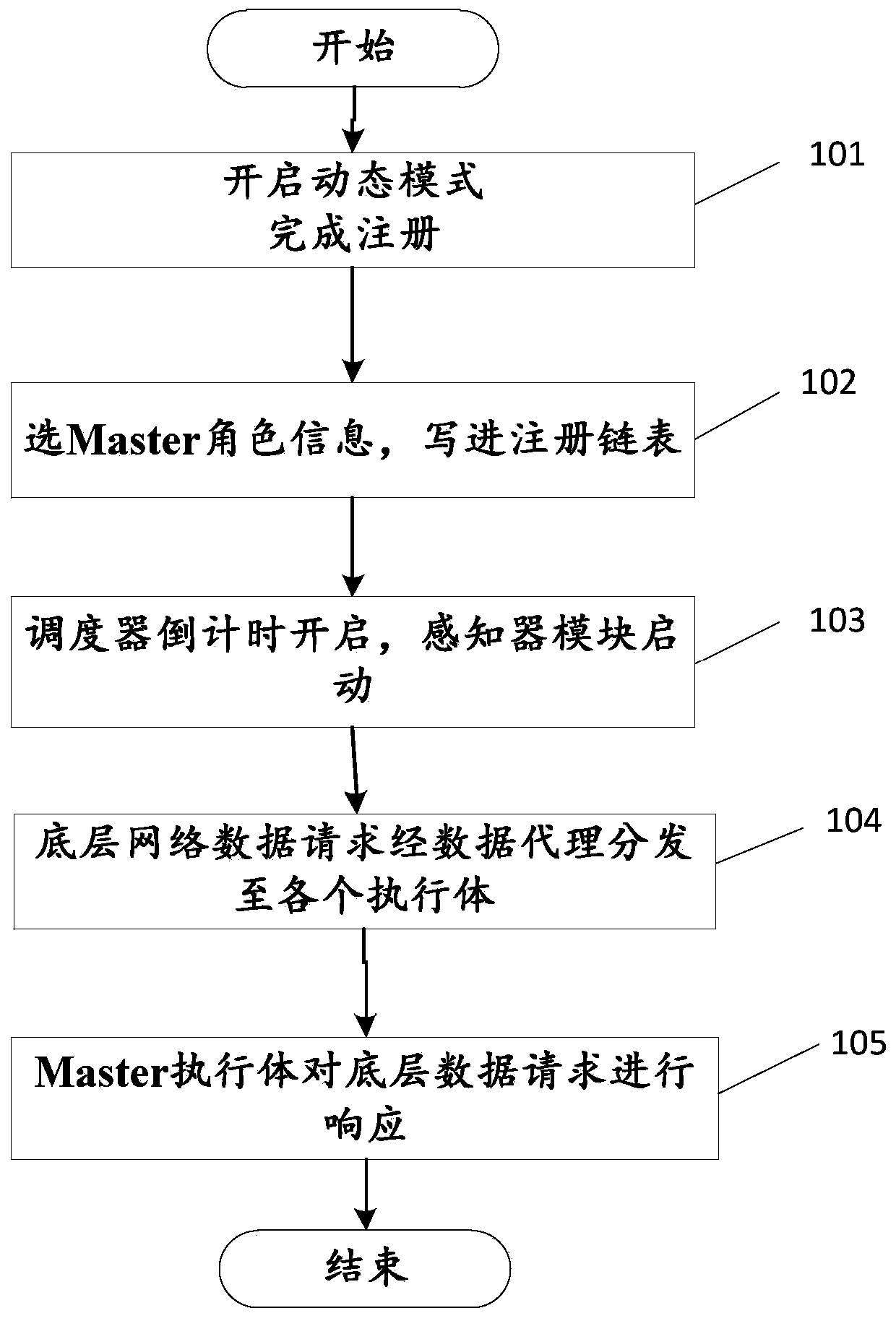
[0046] Embodiment 2, a system for implementing a method for dynamically scheduling a network operating system, comprising the following units:
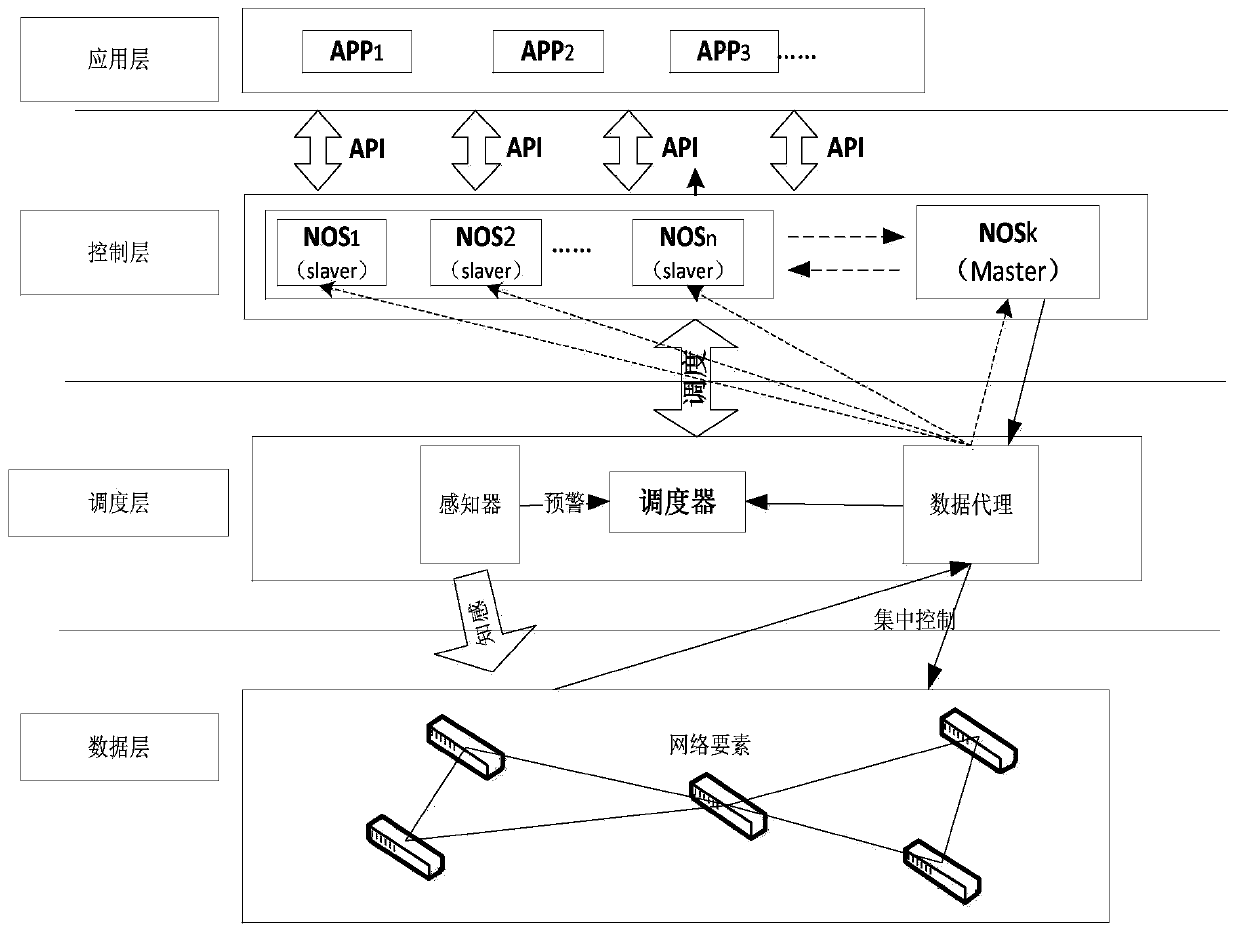
[0047] Application layer unit: various functional APPs program the underlying devices through the programming interface provided by the control layer.
[0048] Control layer unit: Contains a collection of N NOS executives with different functional equivalent structures, one is Master NOS, and there is only one, which is the NOS that actually manages the network; the other is Slaver NOS, which is an alternative NOS , Slaver is called to become Master.
[0049] Scheduling layer unit: transparent to the underlying network and the upper network operating system.
[0050] The scheduling layer unit contains a data proxy module, a sensor module, and a scheduler module, wherein
[0051] Data proxy module: It is the middle point of data interaction between the control plane and the data plane, through which the underlying network requests are ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com