Intrusion intension recognition system and method based on hidden markov and probability inference
A technology for identifying systems and intentions, which is applied in the field of computer security and can solve the problem of ignoring the relationship between time and space of attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0028] The technical scheme that the present invention solves the above-mentioned technical problem is,
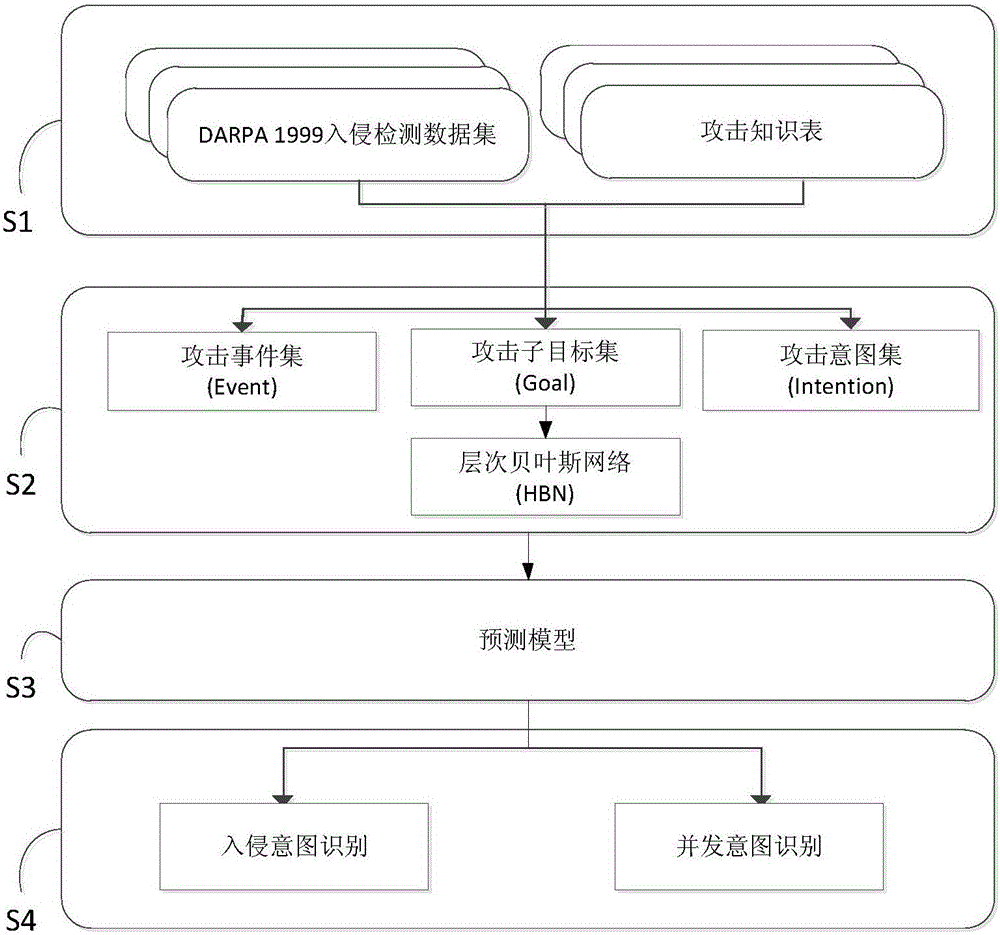
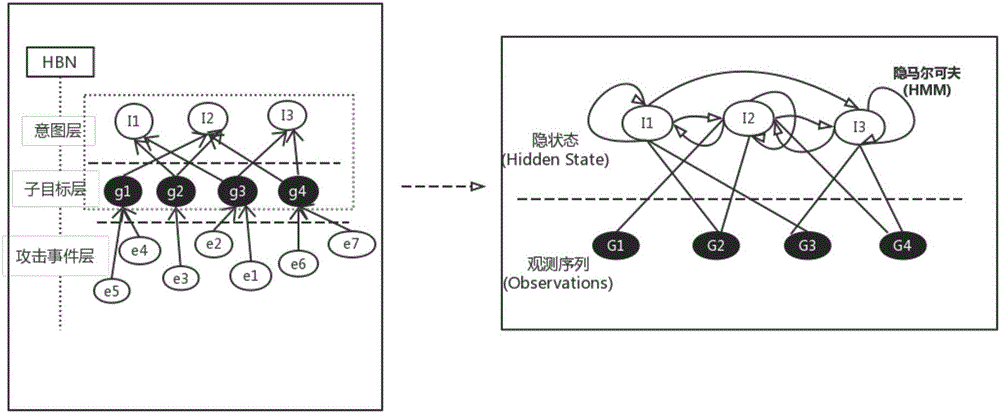
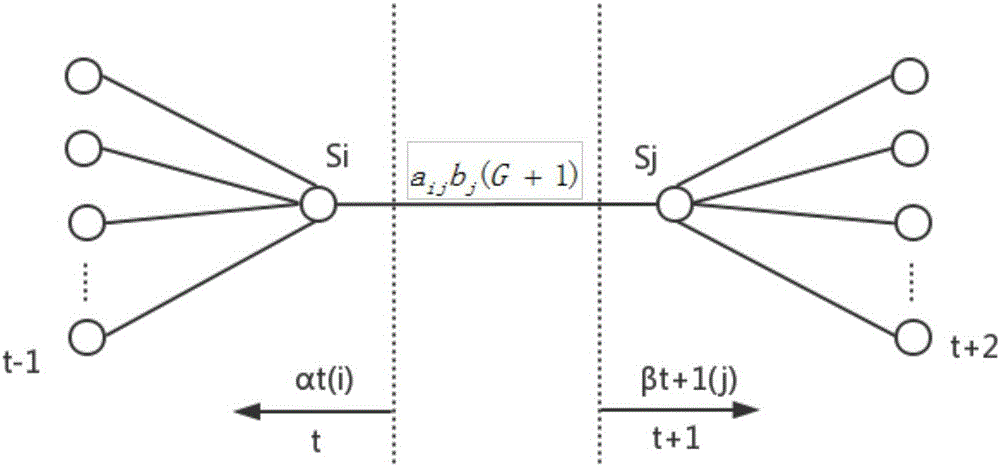
[0029] Such as figure 1 Shown is the overall flow chart of the present invention, including: an intrusion data acquisition module, an attack model building module, a model parameter training module and a predictive analysis module, wherein the intrusion data acquisition module is used to obtain an intrusion data source; the attack model building module is used to Build an attack model, the attack model is divided into three layers of nodes, respectively attack event layer, sub-target layer and intent layer, first, the same source IP address, destination IP address and alarm type, but different attack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com