Risk event handling method and system
An event processing and risk technology, applied in data processing applications, instruments, finance, etc., can solve problems such as the inability to understand the processing progress of multiple insurance companies at the same time, and the inability of customers to obtain them, so as to improve the claim experience and facilitate use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
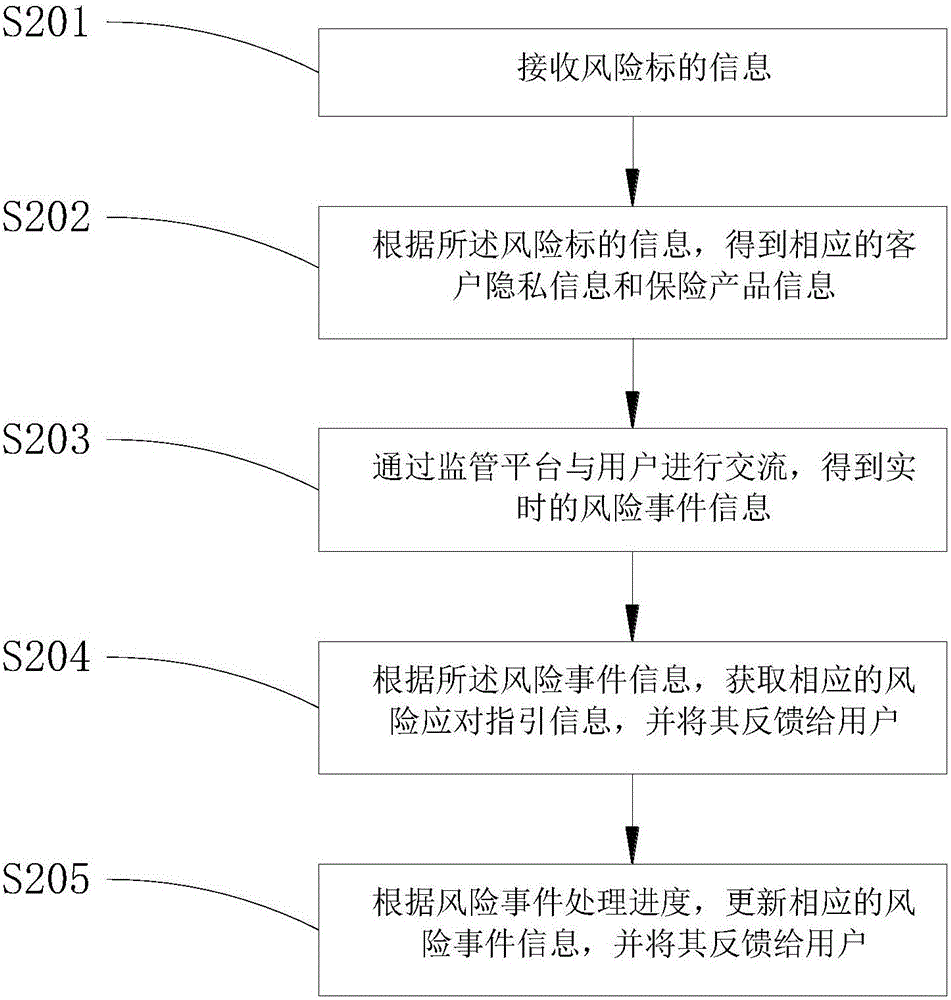
[0035] figure 2 The flow of a risk event processing method provided by an embodiment of the present invention is shown, and the details are as follows:
[0036] In step S201, risk target information is received.
[0037] In step S202, according to the risk target information, corresponding customer privacy information and insurance product information are obtained.
[0038] In the embodiment of the present invention, both the customer privacy information and the insurance product information are acquired by the server from the corresponding insurance company.
[0039] In step S203, communicate with the user through the monitoring platform to obtain real-time risk event information.
[0040] In the embodiment of the present invention, the supervisory platform is used to interact with users when risk events occur, so as to obtain real-time and accurate risk event information. Directly to the salesperson of the insurance company corresponding to the insurance order.
[0041]...
Embodiment 2
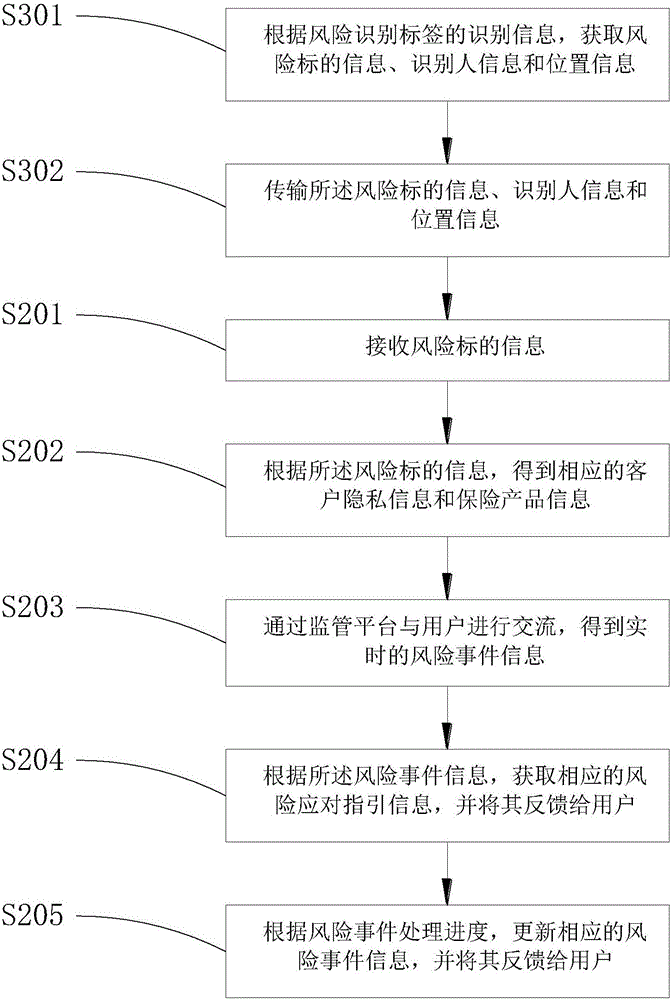
[0048] image 3 The flow of another risk event processing method provided by the embodiment of the present invention is shown, and the details are as follows:
[0049] Before step S201, step S301 and step S302 are also included.
[0050] In step S301, according to the identification information of the risk identification label, the risk object information, identification person information and location information are acquired.
[0051] Wherein, the risk identification label is a physical label that can bear the unique identification of the risk object, which includes one or more of barcode, two-dimensional code and RFID label.
[0052] At this time, the location information is information on the location of the risk identification tag, and its positioning method includes one or more of GPS positioning, base station positioning, wifi positioning and three-axis gyroscope positioning.
[0053] In step S302, the risk target information, identifier information and location infor...
Embodiment 3
[0059] Figure 4 It shows the process of communicating with users through the supervision platform to obtain real-time risk event information provided by the embodiment of the present invention, and the details are as follows:
[0060] In step S401, judge whether the user is the customer himself or not according to the customer's private information, if not, go to step S402; if yes, go to step S403.
[0061] In step S402, according to the identification information and location information, the customer privacy information is updated, and the risk event information other than the customer himself is obtained.
[0062] In the embodiment of the present invention, as an independent risk event information, the non-customer has corresponding risk response guidance information, and the risk event for the risk object will be used as another new risk event information, and the risk response guidance will be carried out again .
[0063] In step S403, real-time risk event information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com