U disk security encryption management method
A management method and security encryption technology, which is applied in the field of U disk security encryption management, can solve problems such as incompatibility, inconvenient use, and insecurity, and achieve the effects of not being easy to decrypt and improving use efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The preferred technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings.
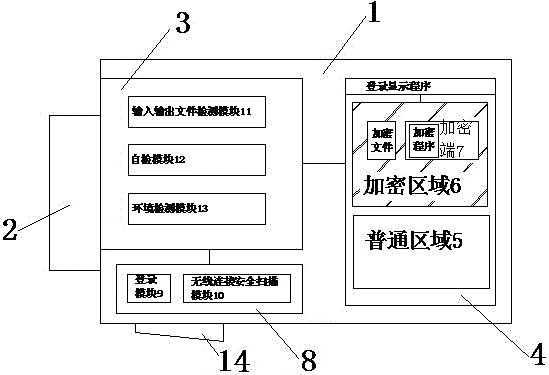
[0021] U disk safety encryption management method of the present invention comprises the following steps:
[0022] 1) Connection: Switch the switch of the U disk to the interface connection state, connect the U disk to the host through the main interface, or switch the switch of the U disk to the wireless connection state, and connect the U disk to the host through the wireless connection module;
[0023] 2) Login: When the U disk is connected to the host through the main interface, the input procedure of the login password is required. When the U disk is connected to the host through a wireless connection, it is necessary to log in through the login module, and through the wireless connection security module to Scan the signal of wireless connection to ensure the security of the wireless connection environment;
[0024] 3) Commo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com