Key algorithm adding method and system of client, client and service end
A client-side and server-side technology, applied in the field of communications, can solve problems such as multi-system processing resources, reduced user experience, and large storage space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
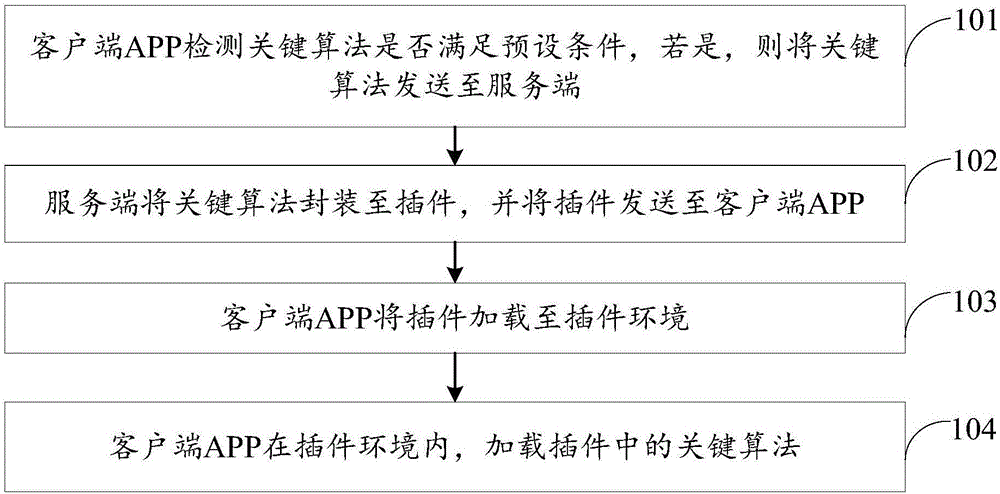
[0105] Embodiment 1 is a client key algorithm addition method provided by the embodiment of the present invention, refer to figure 1 As shown, the method includes:
[0106] 101. The client APP detects whether the key algorithm meets the preset condition, and if so, sends the key algorithm to the server.
[0107] Specifically, through any one of the following operations, the client APP detects whether the key algorithm meets the preset conditions:
[0108] detect missing key algorithms; or
[0109] The version of the detection key algorithm is lower than the current latest version; or
[0110] Detect critical algorithm corruption.
[0111] 102. The server encapsulates the key algorithm into a plug-in, and sends the plug-in to the client APP.
[0112] Specifically, set the communication configuration data between the key algorithm and the data layer;
[0113] Encapsulate communication configuration data and key algorithms into plug-ins.
[0114] 103. The client APP loads t...
Embodiment 2
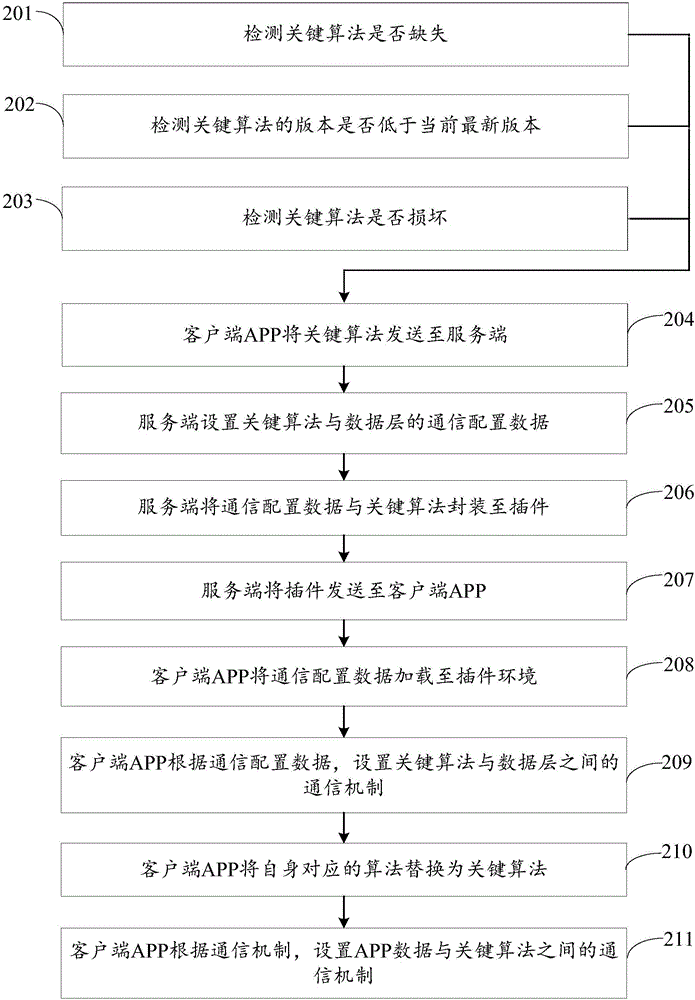
[0121] Embodiment 2 is a client key algorithm addition method provided by the embodiment of the present invention, refer to figure 2 As shown, the method includes:
[0122] 201. Detect whether the key algorithm is missing, and if so, perform step 204.
[0123] Specifically, abnormal events during the running process of the client APP are detected, and the abnormal events include running errors, slow running speeds, normal running of the client APP, errors in loading content, and the like.
[0124] The above abnormal events can be realized by detecting the operation log of the client APP.
[0125] Analyze the abnormal event and detect whether the abnormal event is caused by the lack of a key algorithm.
[0126] 202. Detect whether the version of the key algorithm is lower than the current latest version, and if so, execute step 204.
[0127] Specifically, periodically check whether the version of the key algorithm is lower than the latest version released by the server, and...
Embodiment 3
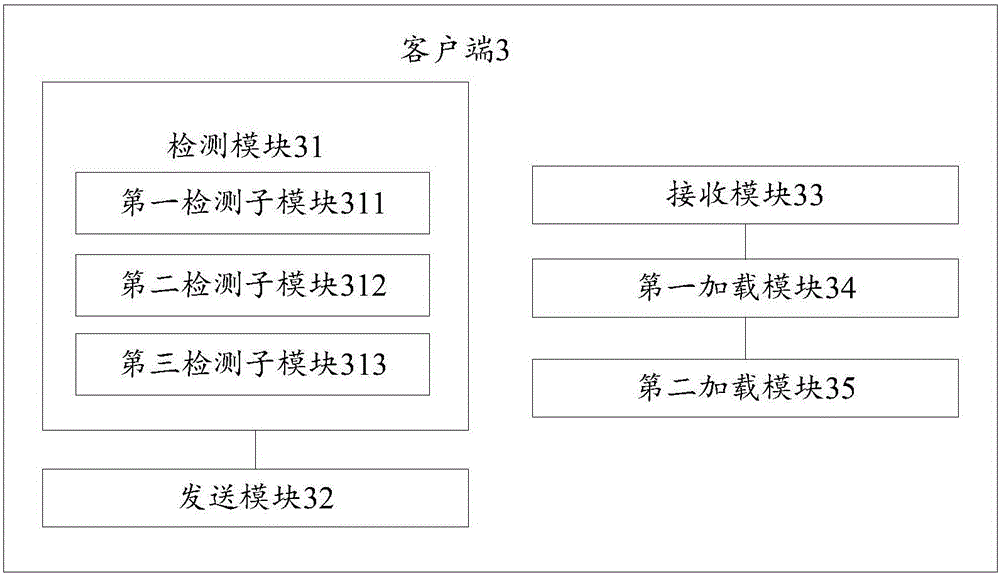
[0156] Embodiment 3 is a client 3 provided by the embodiment of the present invention, refer to image 3 As shown, the client 3 includes:
[0157] A detection module 31, configured to detect whether the key algorithm meets a preset condition;
[0158] The sending module 32 is used to send the key algorithm to the server when the detection module detects that the key algorithm meets the preset conditions, so that the server encapsulates the key algorithm into the plug-in;
[0159] The receiving module 33 is used to receive the plug-in sent by the server;
[0160] The first loading module 34 is used to load the plug-in into the plug-in environment;
[0161] The second loading module 35 is configured to load key algorithms in the plug-in in the plug-in environment.
[0162] Optionally, the detection module 31 includes:
[0163] The first detection sub-module 311 is used to detect the absence of key algorithms;
[0164] The second detection submodule 312 is used to detect tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com