Big data security fusion method without revealing privacy
A fusion method and big data technology, applied in the direction of digital data protection, can solve problems such as privacy data leakage, and achieve the effect of ensuring data security, simple implementation, and promoting information sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] It should be noted that, according to the embodiments disclosed in the present invention, the first party stores the first data set in the first database, and the second party stores the second data set in the second database.
[0012] The first and second data sets respectively record different information, such as activity information of multiple users on different occasions. The first and second data sets have intersections of information, for example, user identity information, which can be extracted as associated fields.
[0013] The present invention provides various implementation manners for performing big data fusion on the first and second data sets.
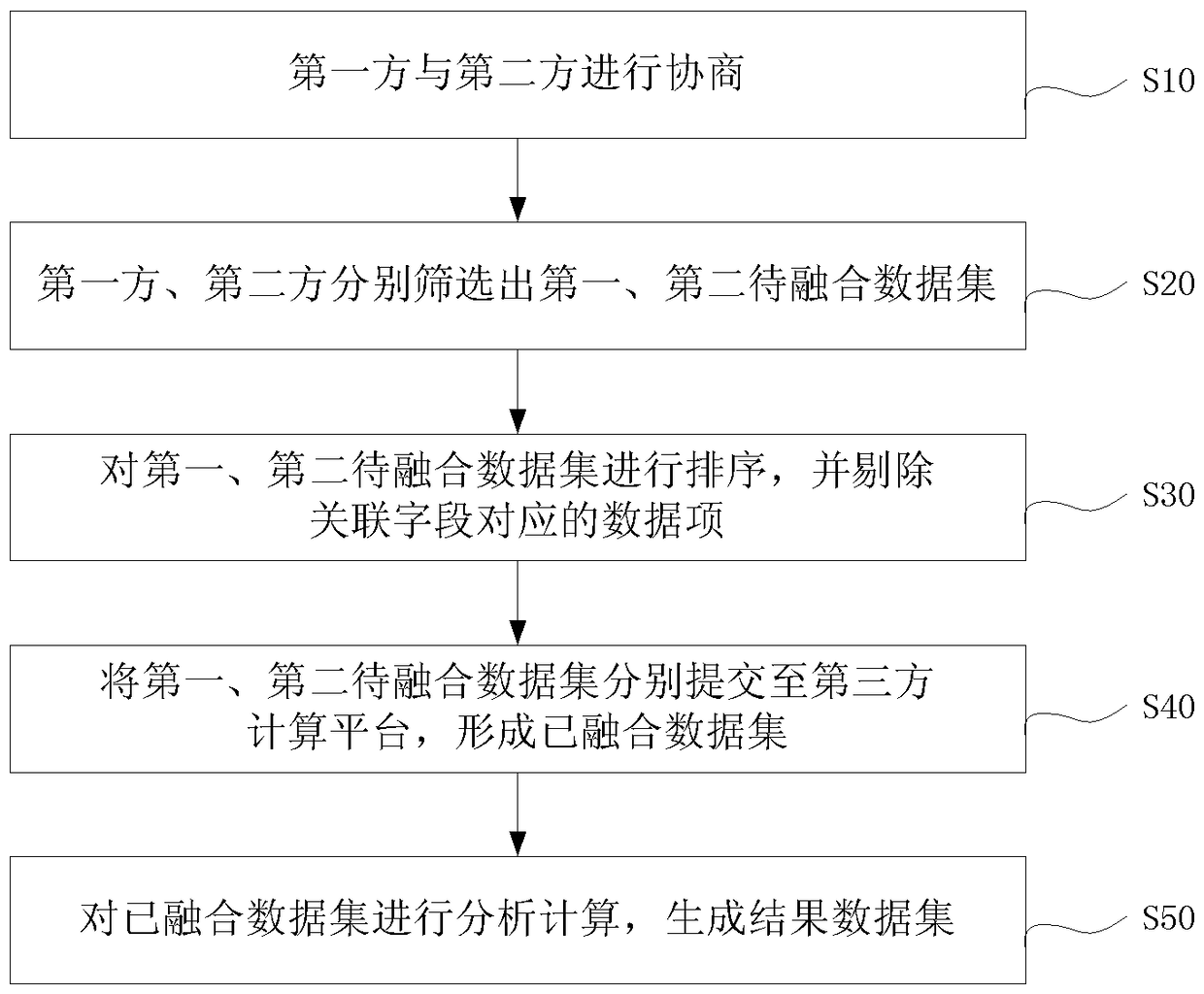
[0014] Such as figure 1 As shown, the first embodiment of the present invention provides a big data security fusion method, which includes the following steps:
[0015] Step S10: The first party and the second party negotiate the associated fields, the data items required by each, and the sorting rules.
[0016] Specifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com