Anti-attack arbitration device
An arbiter and anti-attack technology, applied in the protection of internal/peripheral computer components, etc., can solve the problems of leakage of cryptographic calculation results, being returned to other responses, and failure to return, etc., to achieve high security and reduce the risk of being leaked Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
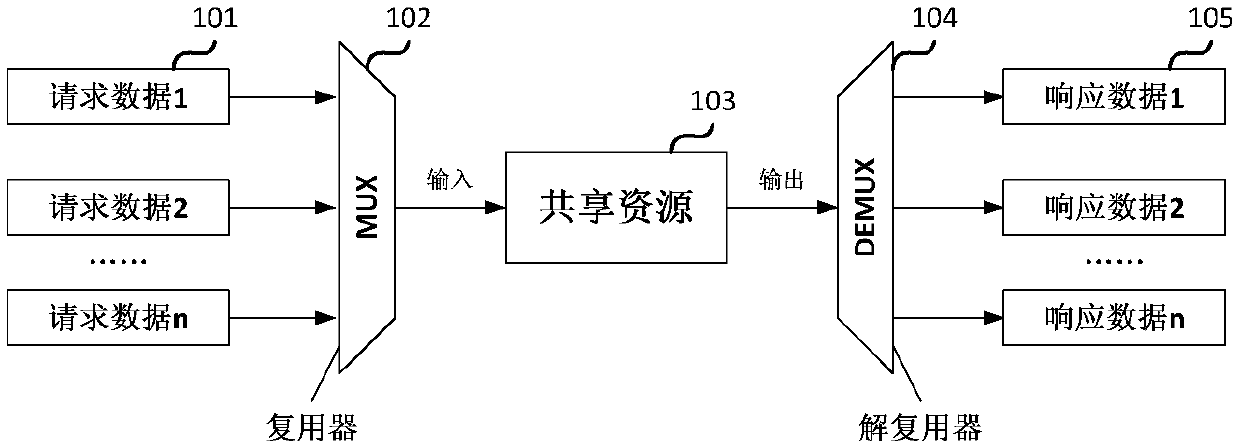
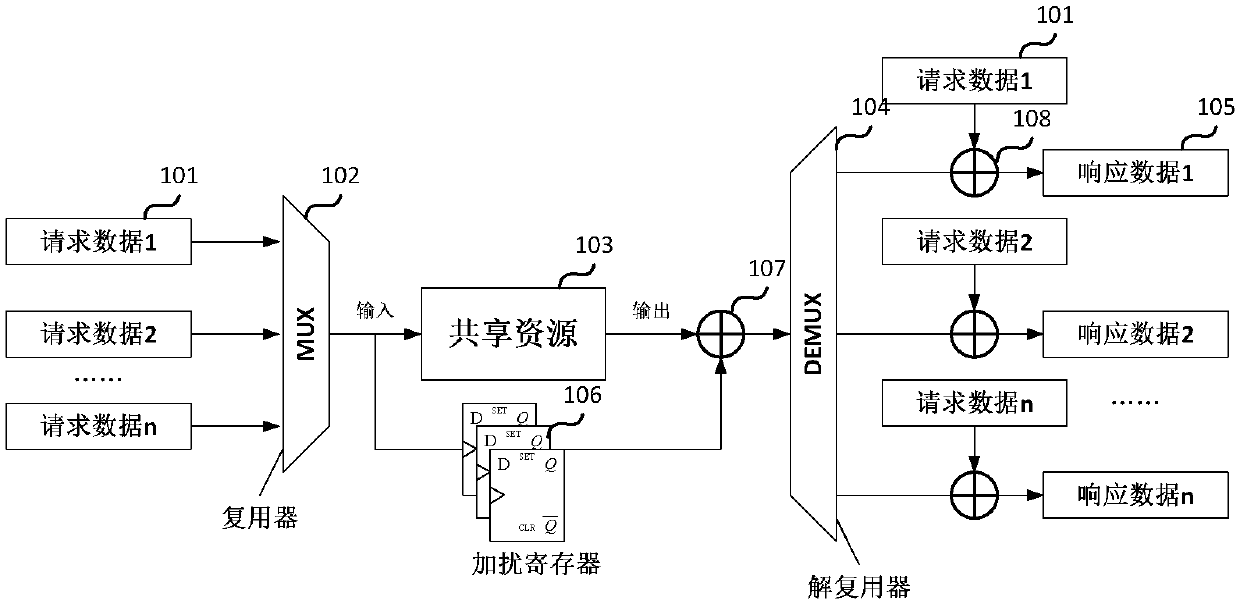
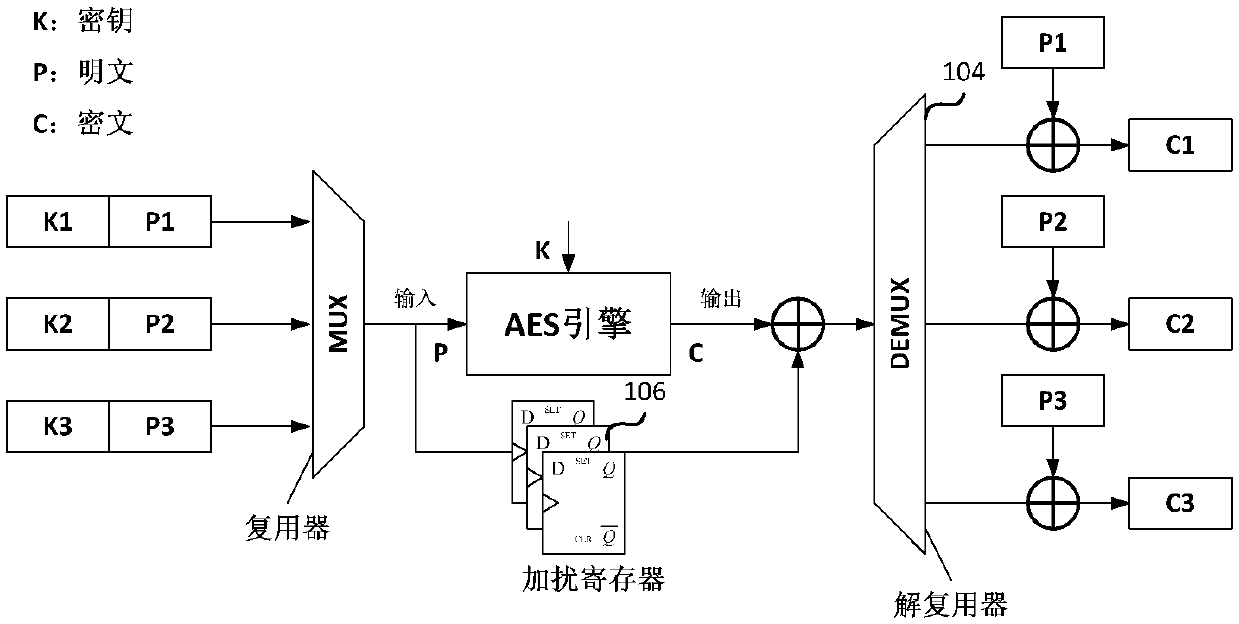
[0015] like figure 2 As shown, the present invention proposes a new arbiter structure on the basis of the prior art, and the arbiter includes a multiplexer 102, a shared resource module 103, a demultiplexer 104, a scrambler 107 and a descrambler 108 .
[0016] The multiplexer 102 is used to receive multiple requests for data, and select one of the multiple requests for data to output according to an arbitration algorithm. The shared resource module 103 is used to receive the request data selected and output by the multiplexer, start the calculation in the request response period, and output the calculation result in the output response period. Generally, the shared resource module 103 is suitable for some resource-intensive modules or algorithm modules that perform complex operations. Resource-intensive modules such as one-time programmable memory (OneTime Programmable, OTP): Assuming that there are multiple requests to read the OTP, the request data is the read address, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com