File access control method and device for operating system
An operating system and file access technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of inability to meet diverse file access control requirements, poor flexibility of file access control, etc., to facilitate management and improve Flexibility, the effect of satisfying safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
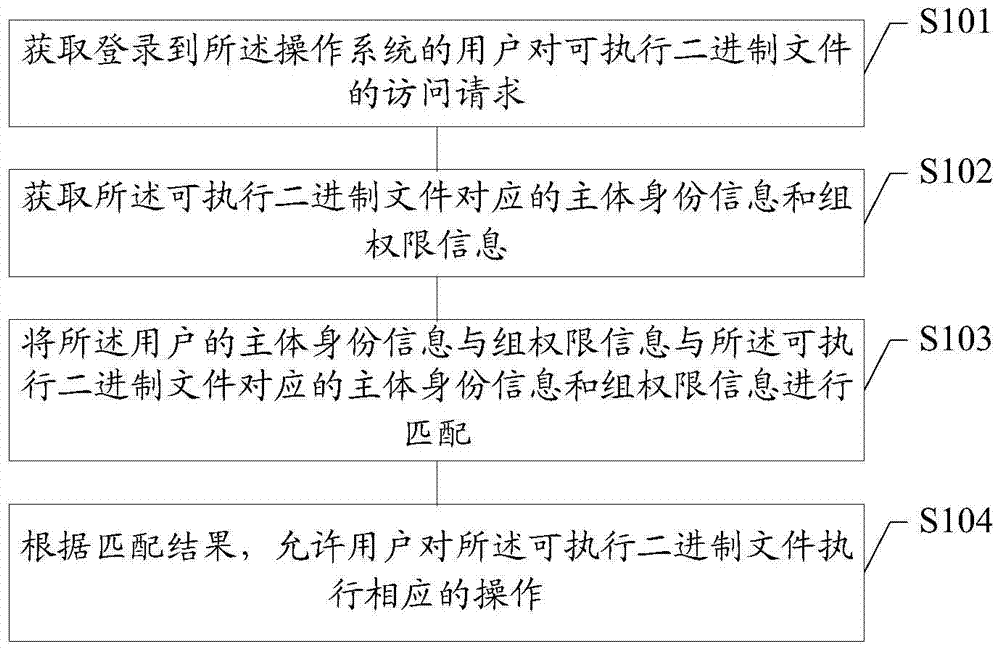
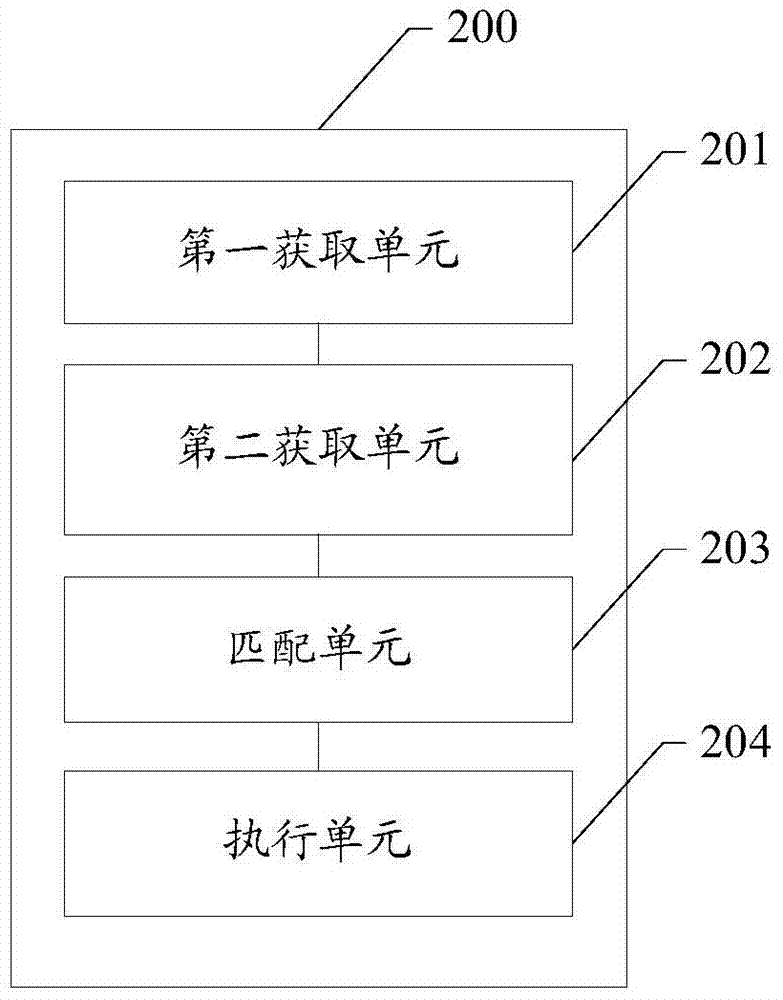
[0028] In the prior art, the operating system can respectively access executable binary files in the operating system through its own subject access control method and role-based access control method. Because discretionary access control methods and role-based access control methods operate independently. It is used to perform corresponding operations on the same executable binary file through corresponding user permissions or group permissions. However, the file access control method in the prior art cannot meet the diversified access requirements of users, and there is a problem of poor flexibility.
[0029] For example, there is a server in the financial department for sharing files, and the maintenance of this server is in the charge of ordinary operation and maintenance engineers, so the operation and maintenance engineers have obtained the special authority "root", and according to the company's access control policy requirements, the storage on the server I do not wan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com