Security authentication method for intelligent set-top box
An intelligent set-top box, security authentication technology, applied in image communication, selective content distribution, electrical components, etc., can solve the problems of password leakage, forgotten password, inconvenience, etc., to achieve the effect of quick verification and convenient management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
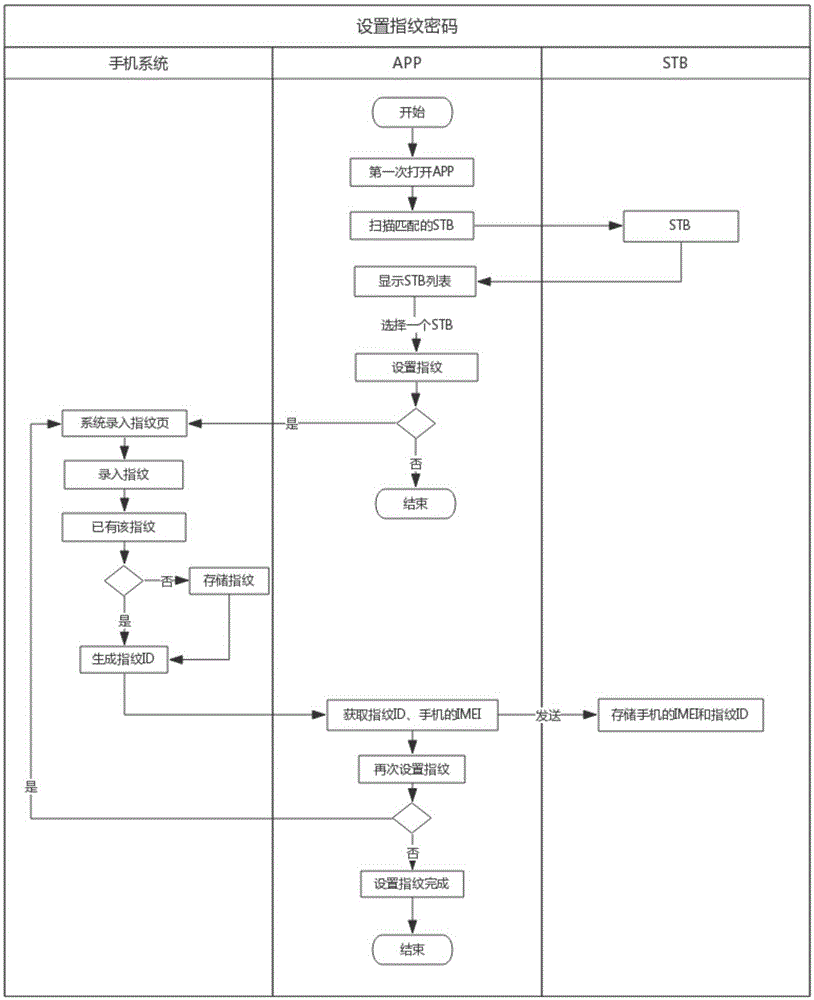
[0040] Example 1, set fingerprint password:
[0041] 1) Open the mobile APP for the first time, and the mobile APP displays the page that is scanning the set-top box connected to the Internet, such as image 3 shown.
[0042] 2) Display the list of scanned set-top boxes after scanning, such as Figure 4 shown.
[0043] 3) Select "99999999" set-top box to set the fingerprint, such as Figure 5 shown.
[0044] 4) at Figure 5 If you choose "No" in the interface shown, the page will jump to Figure 4 Select the set-top box; if you select "Yes", then jump to the fingerprint part of the mobile phone system settings, such as Figure 6 shown.
[0045] 5) After the fingerprint entry is completed, the mobile phone system will prompt the completion after it is stored, and select "OK", as follows Figure 7 shown.
[0046] 6) Then jump to the mobile APP page, and the mobile APP prompts whether to continue to enter fingerprints, such as Figure 8 shown.
[0047] 7) At the same tim...
Embodiment 2
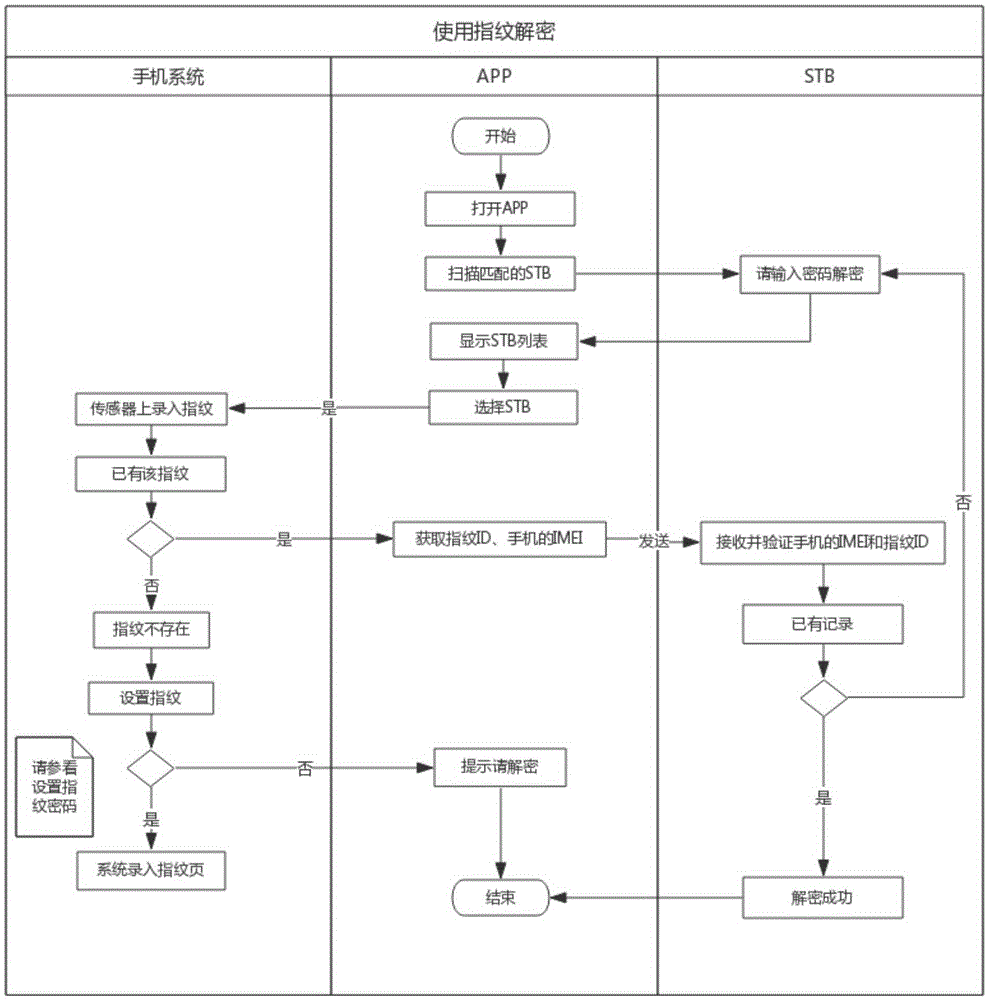
[0049] Embodiment 2, fingerprint decryption:
[0050] When using the set-top box 99999999, when a password is required, the set-top box will prompt to enter the fingerprint for decryption, such as Figure 11 shown.
[0051] At this time, the user opens the mobile APP, and the mobile APP automatically scans the set-top boxes connected to the network, such as Figure 12 shown.
[0052] After scanning, the list of scanned set-top boxes will be displayed, such as Figure 13 shown.
[0053] After the user selects the set-top box "99999999", the decryption operation can be performed, such as Figure 14 shown.
[0054] If the user selects "Set password", the mobile APP will jump to the fingerprint setting section. Figure 6 Perform the fingerprint setting operation. If you select "Decrypt", the mobile APP will prompt the user to enter the fingerprint, such as Figure 15 shown.
[0055] If the information of fingerprint 2 is entered, because the information of fingerprint 2 h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com