Self-representation secure routing authorization method based on identity, namely, public key
A self-representation and routing technology, applied in the field of trusted and secure network infrastructure, can solve problems such as prefix hijacking, and achieve the effect of simple principle, easy implementation and promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
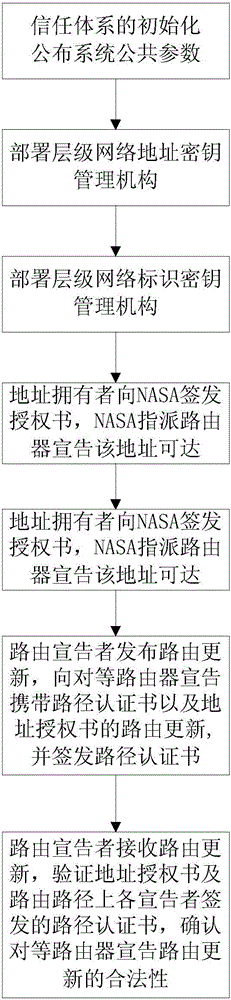
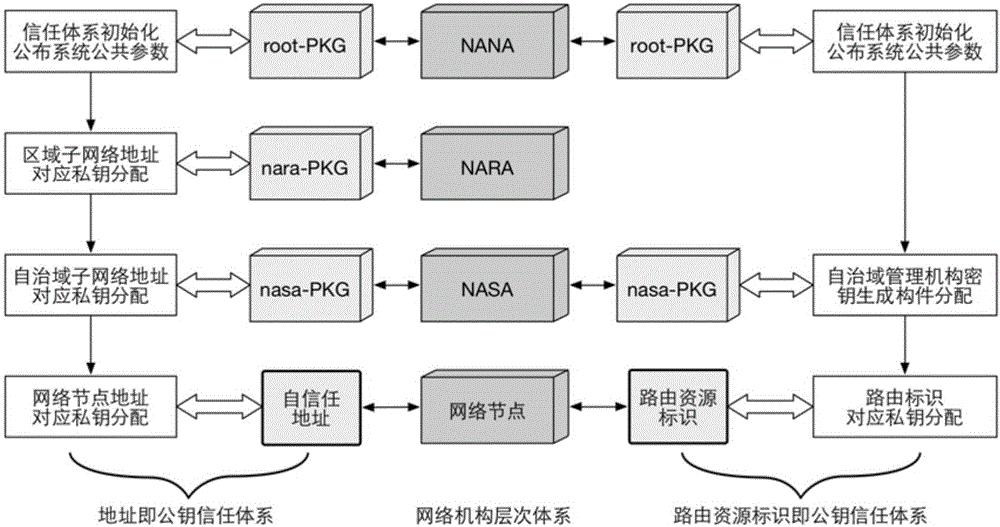
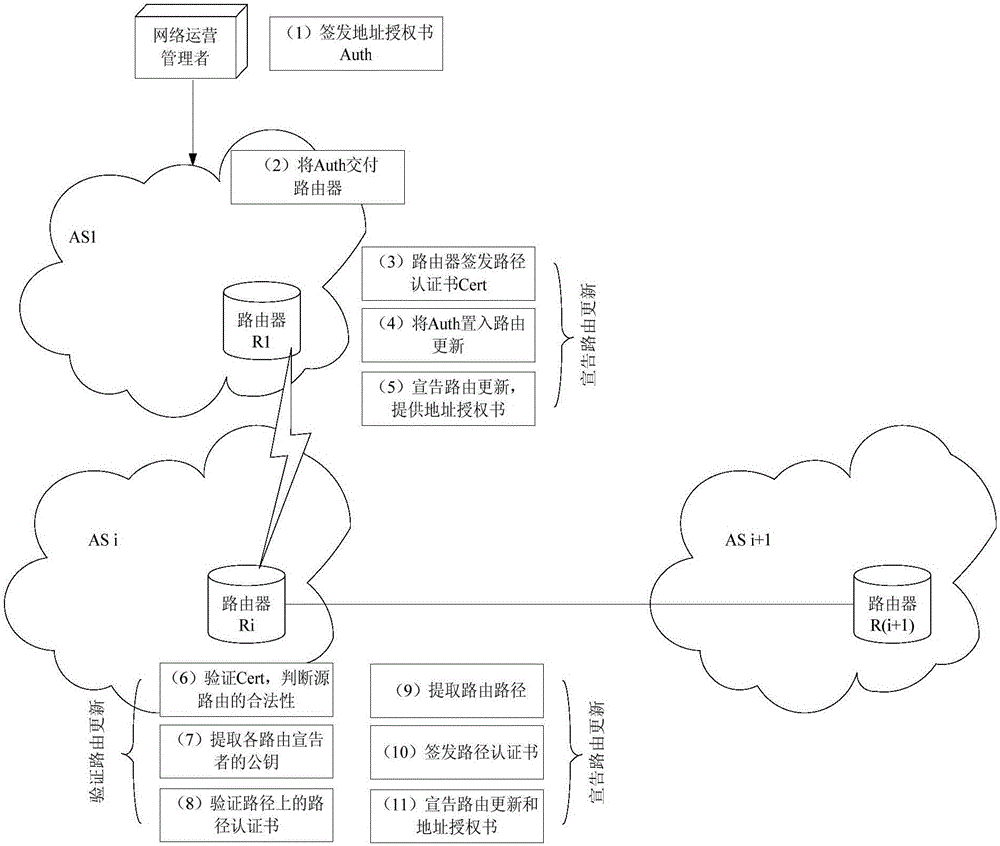
[0046] An identification of the present invention is a self-expression security routing authorization method of a public key, which is based on a self-trusted network address system and a self-trusted routing identification system, through a hierarchical security IP address private key generation and distribution mechanism, Complete the binding of IP addresses and private keys, and complete the deployment of routers through hierarchical authentication methods to realize the binding of routing resource identifiers and corresponding private keys. The owner of the network address signs its address with the private key of the network address, and the advertiser of the router signs its routing path, and the peer router extracts the public key of the routing resource i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com