A verification method for data destruction of storage media
A technology for data destruction and storage media, which is applied in the field of verification of data destruction of storage media, can solve problems such as wrongly pasted labels, subjective and intentional misoperation, and label drop-off, and achieves the effect of strengthening security and no missing verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
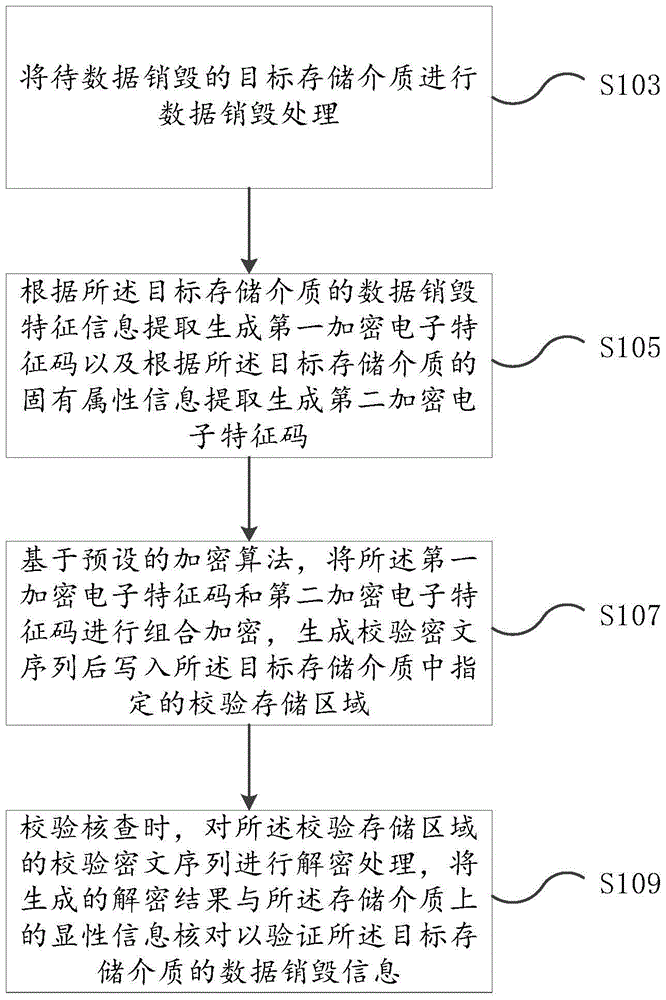
[0032] figure 1 It is a flow chart of Embodiment 1 of the verification method for destroying storage medium data according to the present invention, figure 1 The execution subject is the storage medium data destruction device and the verification verification terminal, specifically as figure 1 shown, including:
[0033] Step 103: Perform data destruction processing on the target storage medium to be destroyed. The storage medium may include, for example, hard disk, U disk, mobile hard disk, SD card, CF card and other storage media. Data destruction can be done by physically clearing and overwriting sectors, or using strong magnetism to degauss and physically destroy storage media. The specific selection method can be selected according to the requirements of data destruction.
[0034] Step 105, extracting and generating a first encrypted electronic signature according to the data destruction feature information of the target storage medium, and generating a second encrypted...
Embodiment 2
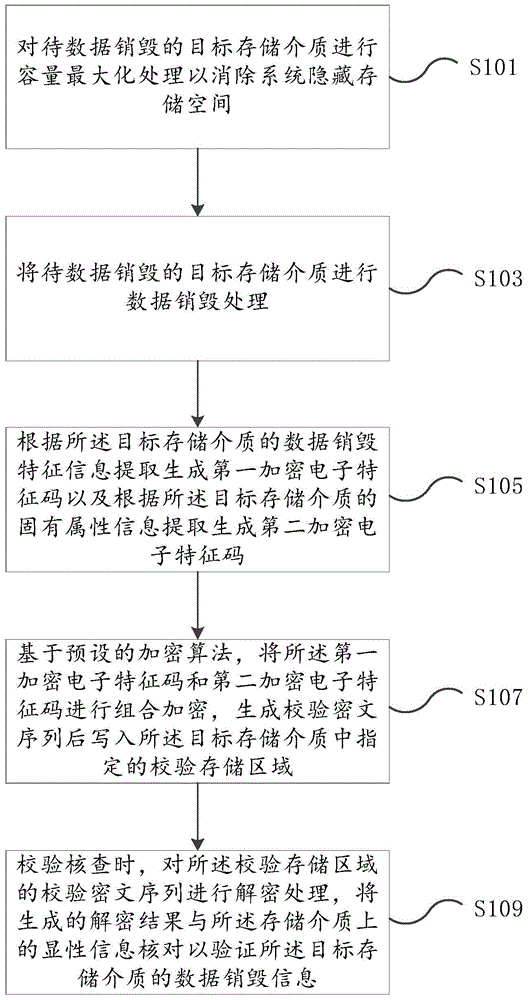
[0044] figure 2 It is the flow chart of Embodiment 2 of the verification method for storage medium data destruction in the present invention. On the basis of Embodiment 1, Embodiment 2 adds a step of maximizing the storage medium capacity, specifically as figure 2 shown, including:
[0045] Step 101, maximizing the capacity of the target storage medium to eliminate system hidden storage space;
[0046] Step 103, performing data destruction processing on the target storage medium to be destroyed;
[0047] Step 105, extracting and generating a first encrypted electronic signature according to the data destruction feature information of the target storage medium, and generating a second encrypted electronic signature according to the extraction of inherent attribute information of the target storage medium;
[0048] Step 107: Encrypt the first encrypted electronic signature and the second encrypted electronic signature based on a preset encryption algorithm, generate a verifi...
Embodiment 3
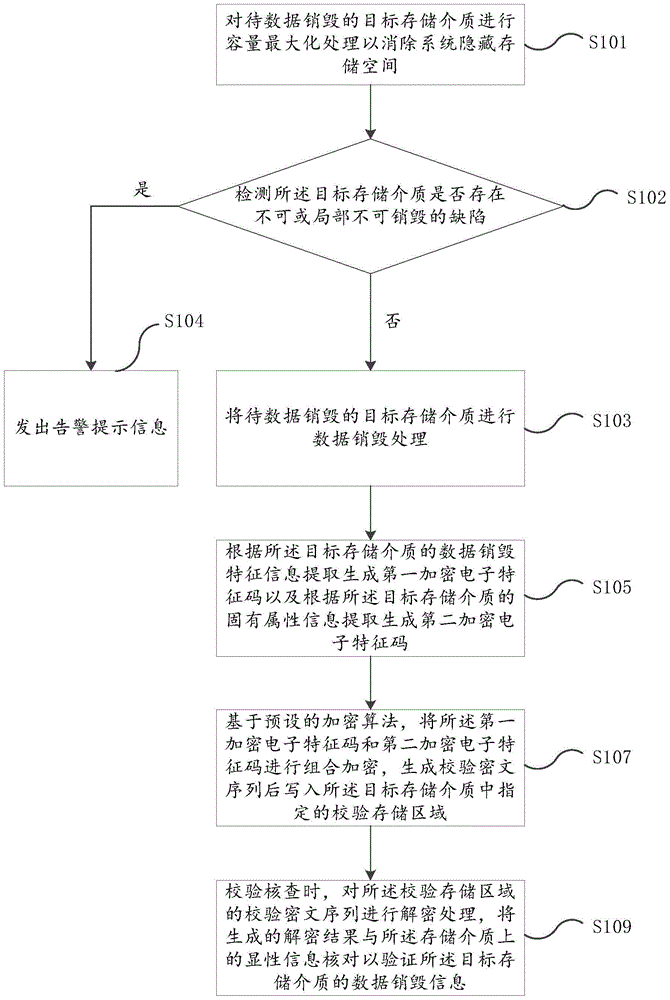
[0052] image 3 It is the flow chart of Embodiment 3 of the verification method for data destruction of storage media in the present invention. Embodiment 3 is based on the above-mentioned embodiments, adding a defect detection step for judging whether there is an indestructible or partially indestructible defect, specifically as follows image 3 shown, including:
[0053] Step 101, maximizing the capacity of the target storage medium to eliminate system hidden storage space;
[0054] Step 102. Detect whether the target storage medium has an indestructible or partially indestructible defect. If it does not exist, execute step 103. If it exists, execute step 104, that is, send an alarm prompt message to confirm whether to perform physical destruction for thorough processing .
[0055] Step 103, performing data destruction on the target storage medium to be destroyed;
[0056] Step 105, extracting and generating a first encrypted electronic signature according to the data des...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com