A train protection logic verification method and device
A logic verification and train protection technology, which is applied in the field of train protection logic verification methods and devices, can solve problems such as poor safety and low verification efficiency, and achieve a clear and clear process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
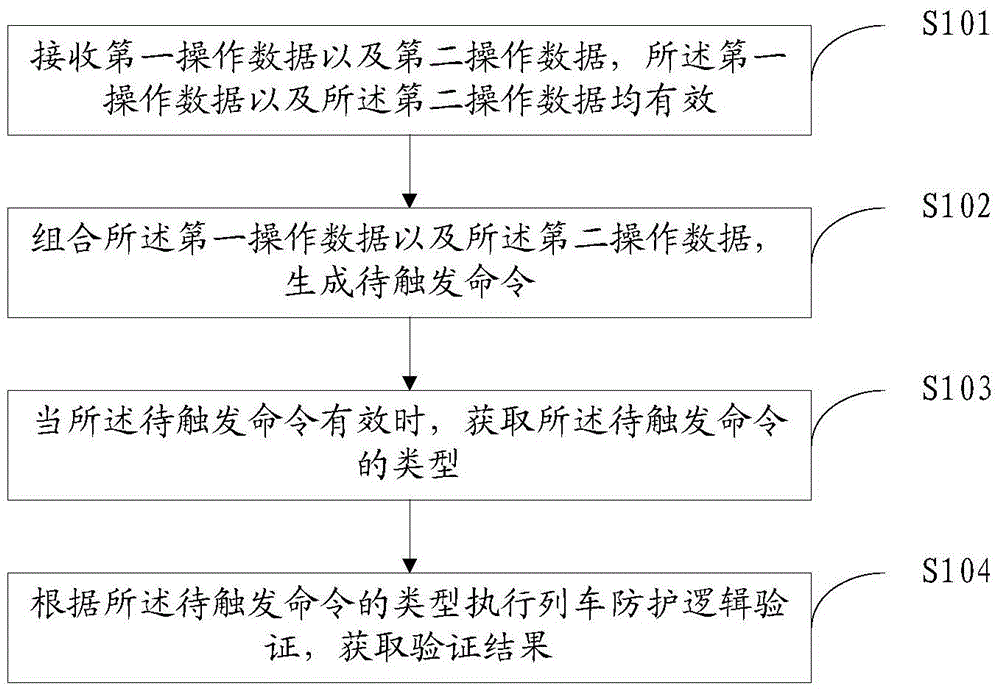
[0052] Please refer to the attached figure 1 , which is a schematic flowchart of a train protection logic verification method disclosed in Embodiment 1 of the present invention, the method specifically includes the following steps:
[0053] S101: Receive first operation data and second operation data, where both the first operation data and the second operation data are valid.
[0054] It should be noted that if the operation data includes the following content, it is called valid.
[0055] 1) Device status and click operation information
[0056] Status information of station equipment such as signal machine, section, turnout, screen door, etc.;
[0057] Click operation of signal machine, section, turnout, screen door and other station equipment.
[0058] 2) Click operation information of the function button
[0059] Function buttons include but are not limited to the following:
[0060] Turnout total positioning; turnout total reverse position; single lock; single relea...
Embodiment 2
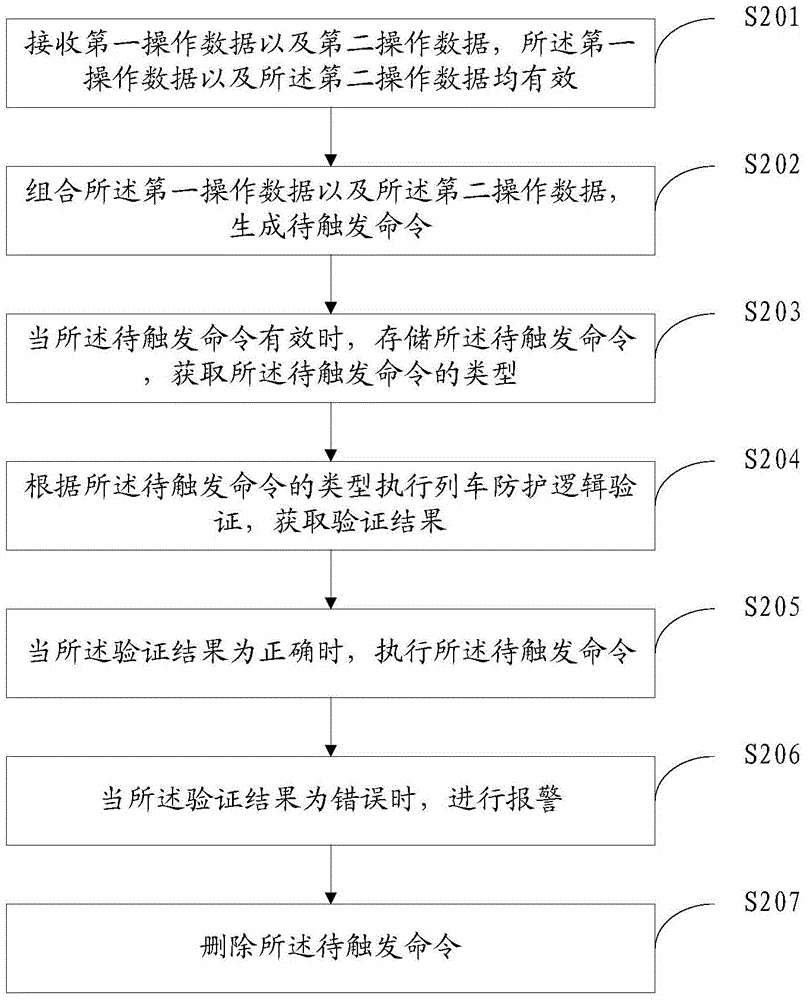
[0069] Please refer to the attached figure 2 , which is a specific flow diagram of another train protection logic verification method disclosed in Embodiment 2 of the present application. The method specifically includes the following steps:
[0070] S201: Receive first operation data and second operation data, where both the first operation data and the second operation data are valid.
[0071] The receiving the first operation data and the second operation data specifically includes:
[0072] Receive the first operation data;
[0073] When the first operation data is valid, determine that the first operation data is the first operation data;
[0074] Start the preset timer and receive the second operation data;
[0075] When the second operation data is received and valid before the timer finishes timing, the second operation data is determined to be the second operation data.
[0076] S202: Combine the first operation data and the second operation data to generate a co...
example 1
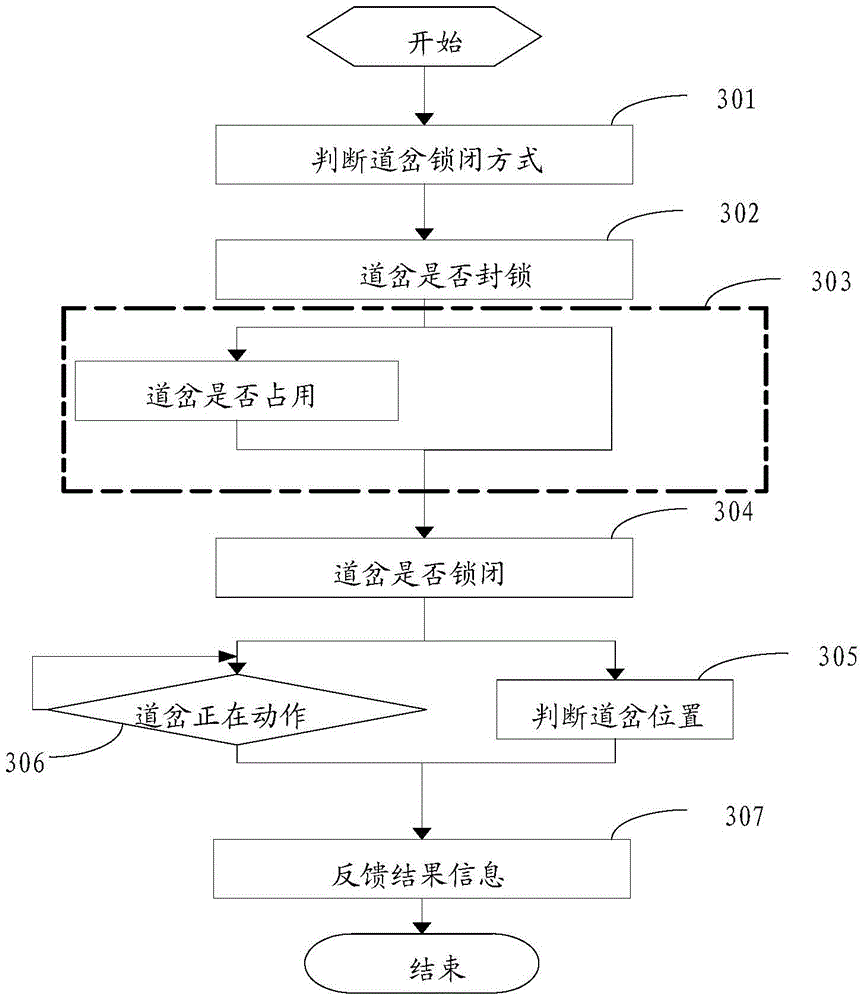
[0087] Please refer to the attached image 3 , which is a schematic flow chart of a method for automatic verification of turnout locking logic disclosed in Example 1 of the present invention. The method specifically includes the following steps:
[0088] 301. Judging the locking mode of the switch.
[0089] It should be noted that this step involves the type of the received command message. If it is a turnout single lock command, it is to lock the turnout separately. The judging conditions for the single lock of the turnout and the locking of the turnout in the process of route selection are different, so the logic verification process is also different.
[0090] 302. Determine whether the switch is blocked.
[0091] If the turnout is blocked, feed back a warning message; otherwise, go to the next step.
[0092] 303. Determine whether the turnout section is occupied.
[0093] It should be noted that, when the judging result of step 301 is that the switch is individually l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com