Single sign on log-out method and system under cluster environment
A single sign-on and single sign-on technology, applied in transmission systems, electrical components, etc., can solve problems such as insecure user accounts, javascript script programs cannot continue to execute, etc., and achieve high work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
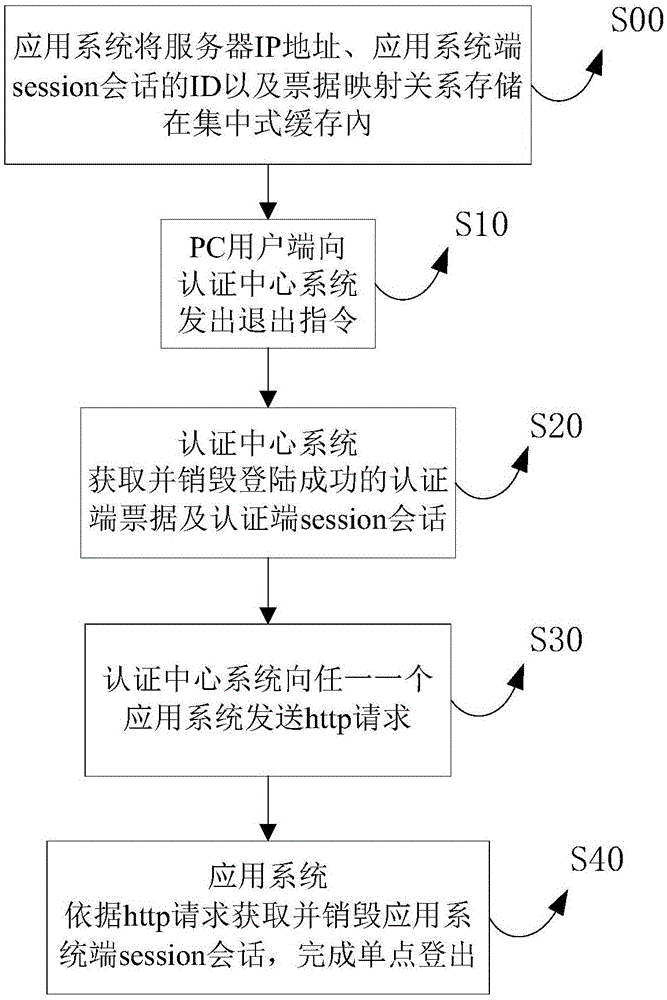
[0026] When the user logs in, the user will access the application system 1 integrated with single sign-on through the browser of the PC client. At this time, if the application system 1 does not have the application system-side ticket for the user to log in successfully, the application system 1 will generate the application system-side session , and request the authentication center system 2 through the URL jump link, and the authentication center system 2 generates the corresponding authentication terminal ticket and authentication session session, and feeds the ticket back to the application system 1 through the URL jump link, and the application system 1 is responsible for the user's Apply the ticket on the system side for verification. If the ticket is found to be an unsuccessful login ticket, send the request information and user information to the authentication center system 2 through http request again to verify the user information. If the verification is successful, ...
Embodiment 2
[0037] Such as figure 2 As shown, a single sign-on exit system for a single sign-on exit method in a cluster environment provided by Embodiment 2 includes an application system 1, an authentication center system 2, a PC client 3 and a centralized cache 12, and the application system 1. The authentication center system 2 and the PC client 3 can exchange information between each other. The application system 1 includes at least one trusted website integrated with single sign-on in the cluster environment. The authentication center system 2 is used to verify the user's account information For verification, the PC client 3 is used to log in or visit a trusted website, and the centralized cache 12 is used for temporary storage server IP address, session ID of the application system side, and ticket mapping between the application system 1 and the authentication center system 2 relationship, the trusted website is deployed on one or more application systems 1 , and the application ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com