Method and system for cloud detection of malicious software based on Hash characteristic vector
A feature vector, malware technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as overall efficiency decline, increase in computing tasks, terminal resource consumption, etc., to achieve the effect of improving efficiency, accurate positioning, and reducing the number of features
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
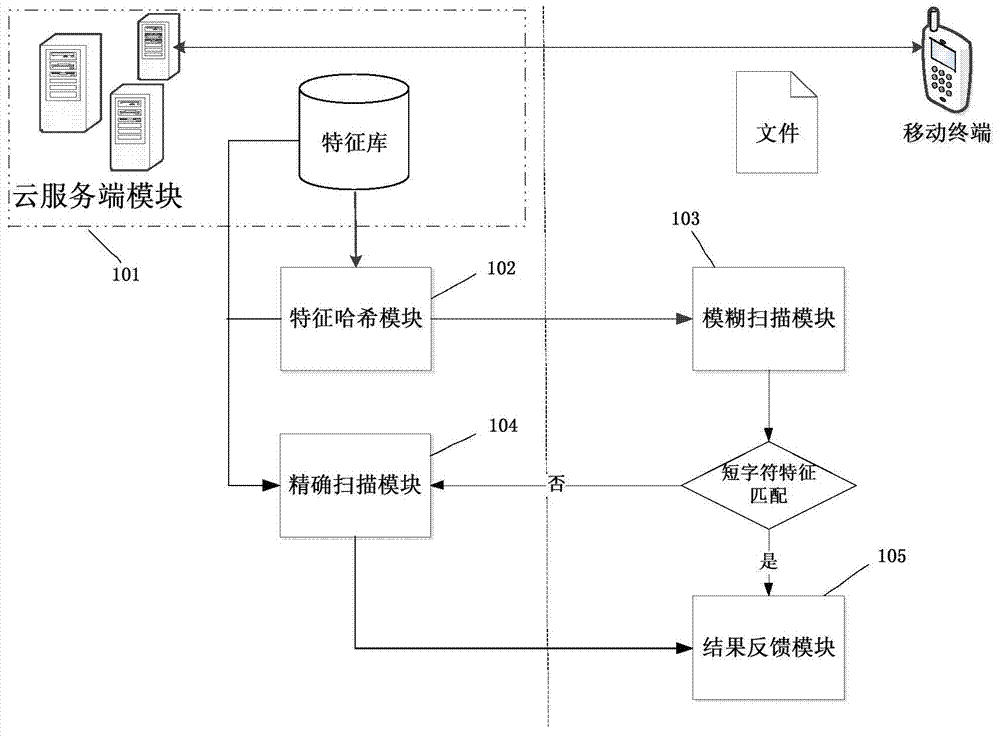
[0052] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0053] In order to reduce the overhead of malware detection terminal and the risk of privacy leakage as much as possible, the present invention uses hash mapping to compress the malware feature library into a feature information vector, and performs detection information interaction between the terminal and the cloud server. And it changes the problem that the existing cloud security technology needs to match all the files of the user with all the feature codes, and only needs to match the specific suspect files of the user with the specific feature codes.
[0054] The present invention designs a malicious software scanning strategy and framework on the basis of the Bloom Filter algorithm. The Bloom Filter algorithm is briefly introduced below. The Bloom Filter (hereinafter referred to as BF) algorithm is a binary vector data structur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com